当前位置:网站首页>How to create a virtual server through a fortress machine? What are the functions of the fortress machine?
How to create a virtual server through a fortress machine? What are the functions of the fortress machine?
2022-06-23 22:26:00 【User 8715145】
Many enterprises or universities now use fortress machines to manage servers , First, the efficiency of the fortress machine is very high , In addition, the improvement of server security is also very obvious . Fortress machine is of great significance in operation and maintenance , At the same time, it can also audit the operation and maintenance . that , Do you know How to create a virtual server through a fortress machine Well ? There will be a detailed introduction below .
How to create a virtual server through a fortress machine ?
1、 First of all, of course, you need to download and install xshell, Click open and new .
2、 On the next page, enter the host's ip Address and fill in the name of the fortress machine .
3、 Click on user authentication and enter the account name and password , Then you will enter the server group , Enter the corresponding number to view the corresponding server .
What are the functions of the fortress machine ?
For the partners of the Digital Fortress machine , It is difficult to explain the functions of the fortress machine , Because it has many functions . But generally speaking, fortress has two core functions , One is resource authorization , The other is identity authentication . Resource authorization is equivalent to setting different permissions for each user , The operation and maintenance personnel need to access the server through the fortress machine . Identity authentication improves the security of the server database , Various authentication methods , It can ensure that there is no problem with the identity of visitors . That is to say , The improvement of Fortress machine for operation and maintenance efficiency and data information security is visible to the naked eye .
How to create a virtual server through a fortress machine , We introduced it above , Now you should be able to verify the operation . In addition, we have also made a brief introduction to the functions of the fortress machine , I hope it can help you better understand the fortress machine , Can understand its functions and functions .
边栏推荐
- Devops sharing: how to hold the meeting?
- Peking University, University of California Berkeley and others jointly | domain adaptive text classification with structured knowledge from unlabeled data (Domain Adaptive Text Classification Based o
- Digital transformation solution for raw material industry chain supply chain platform
- 应用实践 | Apache Doris 整合 Iceberg + Flink CDC 构建实时湖仓一体的联邦查询分析架构
- Valid read-only attribute
- Knowda: all in one knowledge mixture model for data augmentation in feed shot NLP
- [tutorial] build a personal email system using Tencent lightweight cloud
- [tcapulusdb knowledge base] example of deleting data (TDR table)
- How to solve the problem that the GPU VNC has two mice with large deviation
- Detailed explanation of GC principle
猜你喜欢

Opengauss Developer Day 2022 was officially launched to build an open source database root community with developers

游戏安全丨喊话CALL分析-写代码

SLSA: 成功SBOM的促进剂
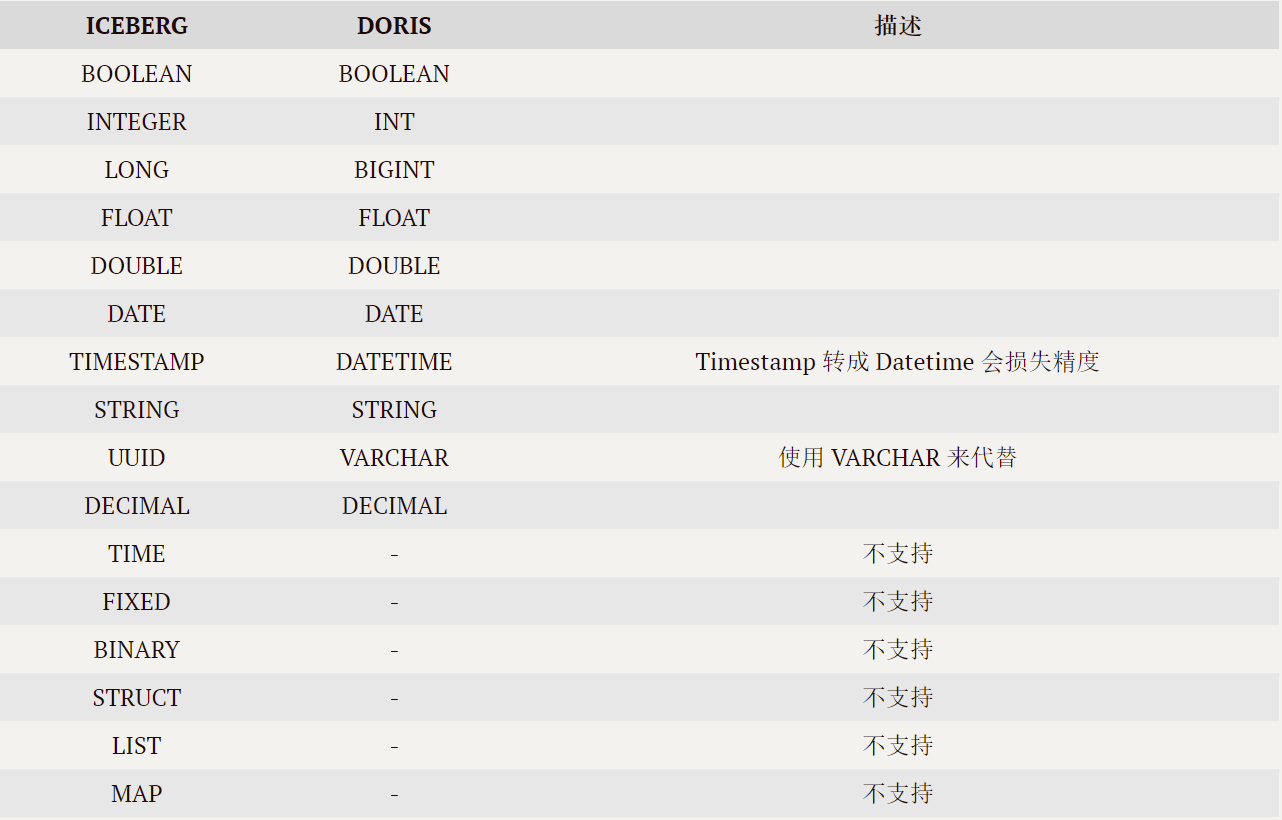
应用实践 | Apache Doris 整合 Iceberg + Flink CDC 构建实时湖仓一体的联邦查询分析架构

為什麼你的數據圖譜分析圖上只顯示一個值?

Beauty of script │ VBS introduction interactive practice

ICML2022 | 基于对比学习的离线元强化学习的鲁棒任务表示

使用 Provider 改造屎一样的代码,代码量降低了2/3!

Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse

The latest research progress of domain generalization from CVPR 2022
随机推荐
Change sql- Tencent cloud database tdsql elite challenge - essence Q & A
Flutter Utils
Detailed explanation of GC principle
Ten thousand words! Understand the inheritedwidget local refresh mechanism
CMU doctoral thesis | meta reinforcement learning through memory, 118 Pages pdf
What if the fortress remote access server fails? What are the reasons why the fortress computer fails to connect to the server?
Judge whether the target class conforms to the section rule
How ppt creates a visual chart
Use bcryptjs to encrypt the password
[emergency] log4j has released a new version of 2.17.0. Only by thoroughly understanding the cause of the vulnerability can we respond to changes with the same method
Detailed explanation of bitmap optimization
Why is the server fortress machine error code 110? How to solve error code 110?
Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse
Icml2022 | robust task representation for off-line meta reinforcement learning based on contrastive learning
Benchclock: a benchmark for evaluating semantic analysis language models
Implement sequence restriction on memory operations
This article takes you to understand the JVM class loading mechanism
脚本之美│VBS 入门交互实战
there can be only one auto column and it must be defined as a key
You must like these free subtitle online tools: Video subtitle extraction, subtitle online translation, double subtitle merging