当前位置:网站首页>Redis cluster
Redis cluster
2022-06-23 18:11:00 【BugMaker-shen】
List of articles
One 、 Cluster concept
Peak bottlenecks in business development :
- redis Services provided OPS You can achieve 10 ten thousand / second , Current business OPS Already achieved 20 ten thousand / second
- The memory capacity of a single machine reaches 256G, Current business needs memory capacity 1T
At this time, cluster can be used to quickly solve the above problems
Cluster architecture : Cluster is to use the network to connect several computers , And provide a unified way of Management , Make it present the service effect of single machine
The role of clusters :
- Disperse the access pressure of a single server , Load balancing
- Disperse the storage pressure of a single server , Achieve scalability
- Reduce the possibility of business disaster caused by single server downtime , Achieve high availability

Two 、 Cluster data storage design
- adopt hash Algorithm design , To calculate the key Where it should be saved
- Cut all storage space into 16384 Share , Each host holds a part of , Each represents one storage space ( Slot ), Is not a key The preservation space of , This storage space can hold many key
- take key According to the calculated results, put them into the corresponding storage space

Suppose we now add a machine , How should the stored data and space be allocated ?

A machine is divided into slots for new machines , The so-called add machine and delete machine , Change the machine stored in the slot
3、 ... and 、 The design of communication within the cluster
- Communication databases , Save the number of slots in each library
- One hit , Go straight back to
- A miss , Tell me the exact location , Hit twice at most

At this point, a client is looking for key, First it will pass hash The algorithm calculates key Corresponding slot number , Then find the corresponding machine on the hash ring , Check if there are corresponding slots on this machine ( Due to the possible addition of machines 、 Delete , Slots on the machine will be added to different machines )
If this machine has key Corresponding slot , Direct search returns ; without , Then find the slot number of each machine and the record of the machine , Then go to the corresponding machine to get it
Four 、 Set up the cluster
Cluster To configure
Set join cluster, Become one of the nodes
cluster-enabled yes|no
cluster Profile name , This file is automatically generated , And it's only used to quickly find files
cluster-config-file <filename>
Node service response timeout , Used to determine whether the node is offline or switched to slave
cluster-node-timeout <milliseconds>
master Connected slave Minimum quantity
cluster-migration-barrier <count>
To configure 3 masters—3 slaves
To write redis-6379.conf
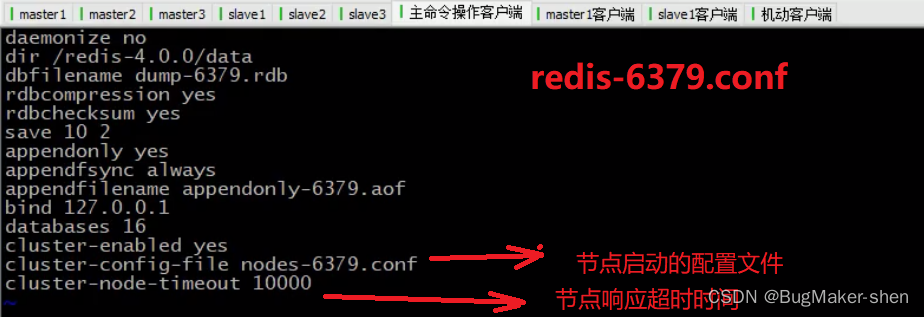
from redis-6379.conf obtain redis-6380.conf、redis-6381.conf、redis-6382.conf、redis-6383.conf、redis-6384.conf, Respectively as 3 individual master and 3 individual slave The startup profile for
Start all of master and slave


This is also a node by node , We need to connect them , stay src There is a redis-trib.rb Executable program of ( This file needs to be installed ruby)

# there n Express 1 individual master Corresponding n individual slave
# hinder ip:port Express master and slave Information about ,master and slave The quantity needs to be the same as the previous one n Corresponding
# hypothesis n=1, Yes 6 Group ip:port, It means before 3 A for master, after 3 A for slave, Realization 1 Lord 1 from
# hypothesis n=2, Yes 9 Group ip:port, It means before 3 A for master, after 6 A for slave, Realization 1 Lord 2 from
./redis-trib.rb create --replicas n ip1:port1 ip2:port2 ....
Write 6 Group ip:port, Execution instruction , Generate 3 Group 1 Lord 1 from

Before generating multiple groups of master-slave structures , Let's take a look first data Catalog ( stay redis- port .conf Middle configuration ) The configuration file of the generated node nodes- port .conf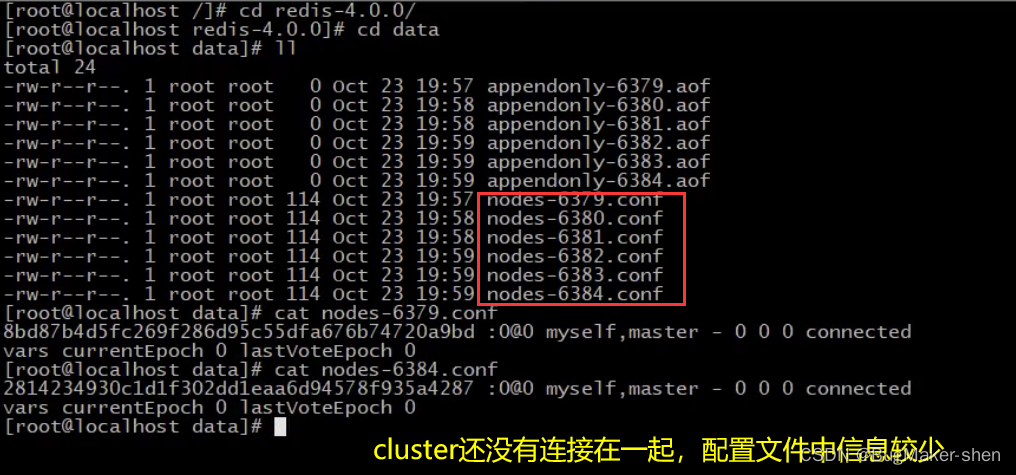
We type in yes, Generate 3 Group 1 Lord 1 from 
cluster When connected together , The cluster is configured , here nodes- port .conf And it changed . Let's see master 6379 Corresponding node configuration file 
Let's see 6379master Prompt information of the terminal

5、 ... and 、 Cluster usage practice
1. Use the cluster to store data

We're connected to 6379 Port of redis After the server , Want to be in 6379 Put data on the server , It can be done by CRC Algorithm and module 16384 To calculate the itheima This data should be placed in 5798 Slot No , And this slot is 6380 On the machine , We are not allowed to put 6379 On the machine
We use -c Parameter login server , This parameter is dedicated to cluster operation

We are still connected 6379 The server , When you put the data , Give tips , Although we are 6379 Put data on , But through CRC Algorithm and module 16384 To calculate the itheima This data should be placed in 5798 Slot No , So we redirected to 6380 machine
We go through -c Parameter login 6382 The machine slave The server fetches data 
The prompt message tells us , Redirect to 6380 On the machine 5798 From slot No . As long as we log in to any machine in the cluster , Can be in 6380 On the machine 5798 Take out slot No , If we log in 6380 The machine will not have redirection information , Instead, you take the data directly
2. slave The impact of dropping the line on the cluster
The biggest advantage of a cluster is not that it can store data on multiple machines , Instead, the cluster can solve the business disaster caused by downtime
Let's stop first 6382 slave1

Let's see slave1 Corresponding master1,master1 Find out slave1 10s No response within , Mark it as offline 
At this time, the others in the cluster master and slave Will receive master1 The notice of ,slave1 Offline

Then we let slave1 Back online

After going online and master1 Just resynchronize ,master1 Then inform others master and slave of slave1 Online information of , The other machines are cleared slave1 End of line marking for

summary : slave After offline , It corresponds to master It will be marked as offline , At the same time, other machines in the cluster are notified of this slave Offline ; When it goes online , And then synchronize the data with it , Then notify the other machines in the cluster of this slave Online information of
3. master The impact of dropping the line on the cluster
Let's stop. master1

Here is with master1 Corresponding slave1 The operation of
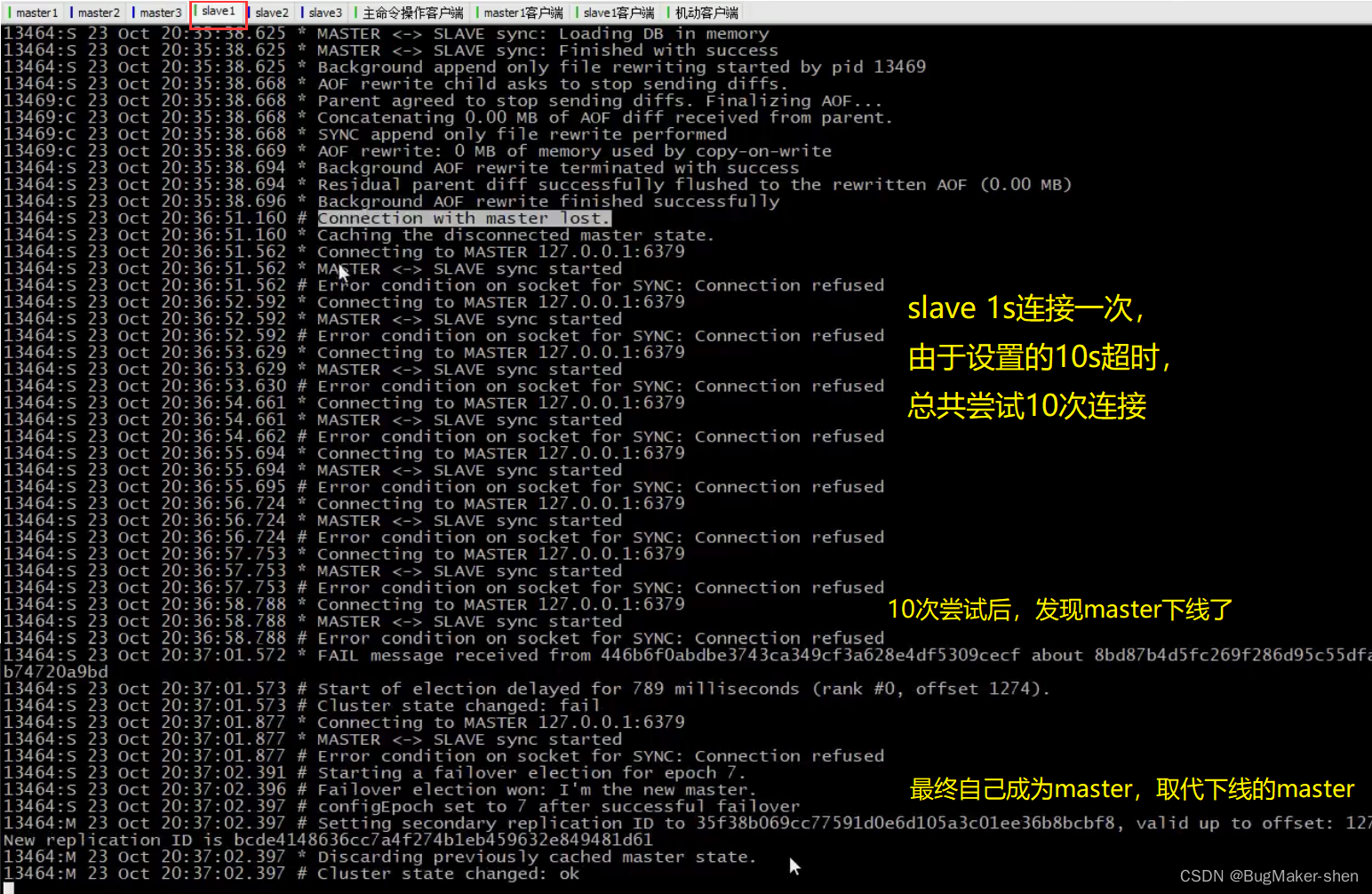
We use it cluster nodes Check the node information , Found to have 4 individual master, among 6379 Marked as fail

We now restart 6379

6379 Request and 6382 Data synchronization 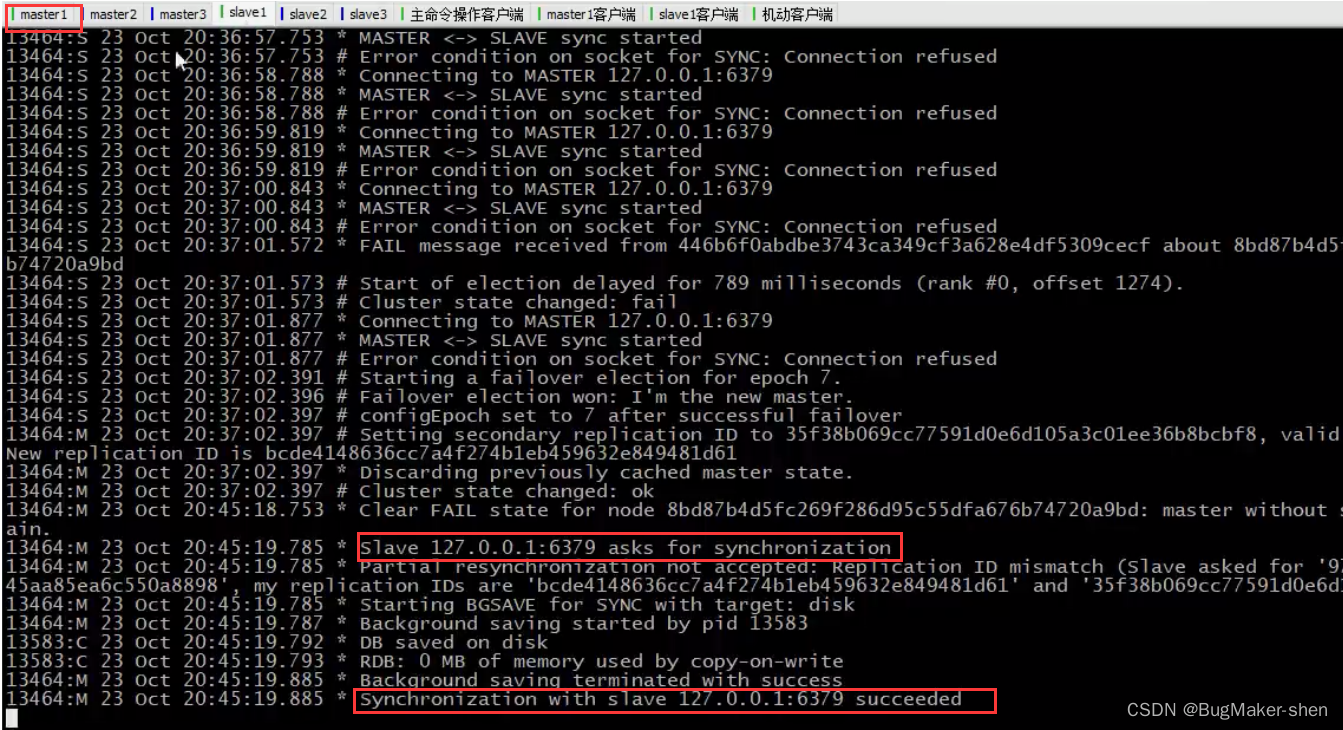
Reuse cluster nodes Check the node information ,6379 The state of the from master fail Changed to slave

summary : When master1 After offline , Corresponding slave1 Will try to connect , After the timeout, you become a new master, Then notify the other machines in the cluster ,master1 Go offline and become master The news of ,master1 The state of is marked as master fail;6379 When it comes back online , It's going to be slave, And with their own master Data synchronization
Cluster Node operation command
View the cluster node information
cluster nodes
Enter a slave node redis, Switch its master node
cluster replication <master-id>
Find a new node , Add master node
cluster meet ip:port
Ignore one without slot The node of
cluster forget
Manual failover
cluster failover
边栏推荐
- Video anomaly detection data set (shanghaitech)
- 论文阅读 (58):Research and Implementation of Global Path Planning for Unmanned Surface Vehicle Based...
- 7、VLAN-Trunk
- [esp8266 - 01s] obtenir la météo, Ville, heure de Beijing
- [Wwise] there is no sound problem after Wwise is embedded in unity and packaged
- How code 39 check bits are calculated
- History of storage technology: from tape to hardware liquefaction
- Goframe framework: fast implementation of service end flow limiting Middleware
- QML类型:Loader
- [learning notes] tidb learning notes (III)
猜你喜欢

org. apache. ibatis. binding. BindingException: Invalid bound statement (not found):...

科技互动沙盘是凭借什么收获人气的

Counter attack and defense (1): counter sample generation in image domain

论文阅读 (50):A Novel Matrix Game with Payoffs of Maxitive Belief Structure

Alien world, real presentation, how does the alien version of Pokemon go achieve?

Paper reading (54):deepfool: a simple and accurate method to four deep neural networks

Self training multi sequence learning with transformer for weakly supervised video animation

2022年T电梯修理考试题库及模拟考试
【Wwise】Wwise嵌入Unity后打包出现没有声音问题

Redis 集群
随机推荐
Reinforcement learning series (I) -- basic concepts
Cryptography involved in IOT device end
How to solve the problem that the esp8266-01s cannot connect to Huawei routers
2022年在网上办理股票开户安全吗?
org. apache. ibatis. binding. BindingException: Invalid bound statement (not found):...
聊一聊数据库的行存与列存
Troubleshooting and modification process of easycvr interface dislocation in small screen
How to make towel washing label
POC about secureworks' recent azure Active Directory password brute force vulnerability
Baidu AI Cloud product upgrade Observatory in May
Paper reading (50):a novel matrix game with payoffs of maximal belt structure
对抗攻击与防御 (1):图像领域的对抗样本生成
How to quickly obtain and analyze the housing price in your city?
科技互动沙盘是凭借什么收获人气的
[tool C] - lattice simulation test 2
CRMEB 二开短信功能教程
Alien world, real presentation, how does the alien version of Pokemon go achieve?
论文阅读 (49):Big Data Security and Privacy Protection (科普文)
Paper reading (49):big data security and privacy protection (Kopp)
Kdevtmpfsi processing of mining virus -- Practice