边栏推荐
- Data-centric vs. Model-centric. The Answer is Clear!
- Unity addressable batch management
- NIPS 2014 | Two-Stream Convolutional Networks for Action Recognition in Videos 阅读笔记
- Want to open an account, is it safe to open an online stock account?
- How to calculate the characteristic vector, weight value, CI value and other indicators in AHP?
- 在哪个平台买股票开户安全?求分享
- Stimulsoft Ultimate呈现报告和仪表板
- Trendmicro:apex one server tools folder
- About i/o -- the relationship between memory and CPU and disk
- Is it really safe to pay new debts? Is it risky
猜你喜欢

How is the ISM model analyzed?

Unity Addressable批量管理

How to calculate the information entropy and utility value of entropy method?

浏览器查看当前页面所有的监听事件
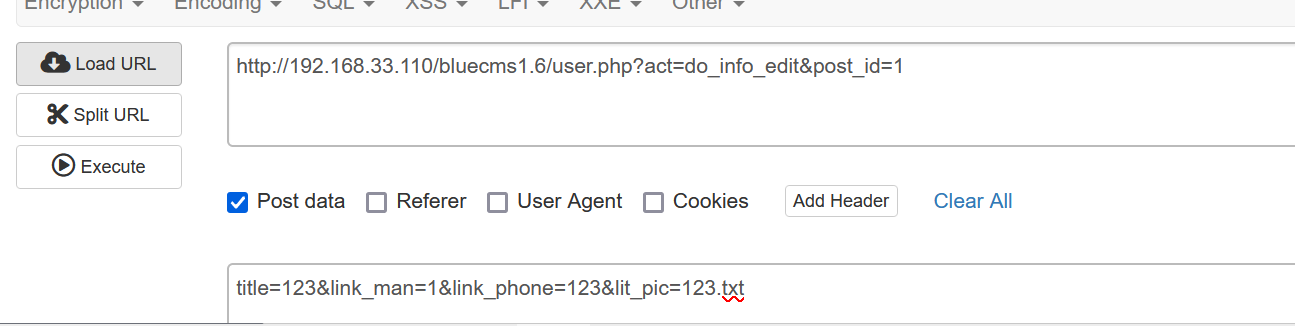
Bluecmsv1.6-代码审计

What do various optimizers SGD, adagrad, Adam and lbfgs do?
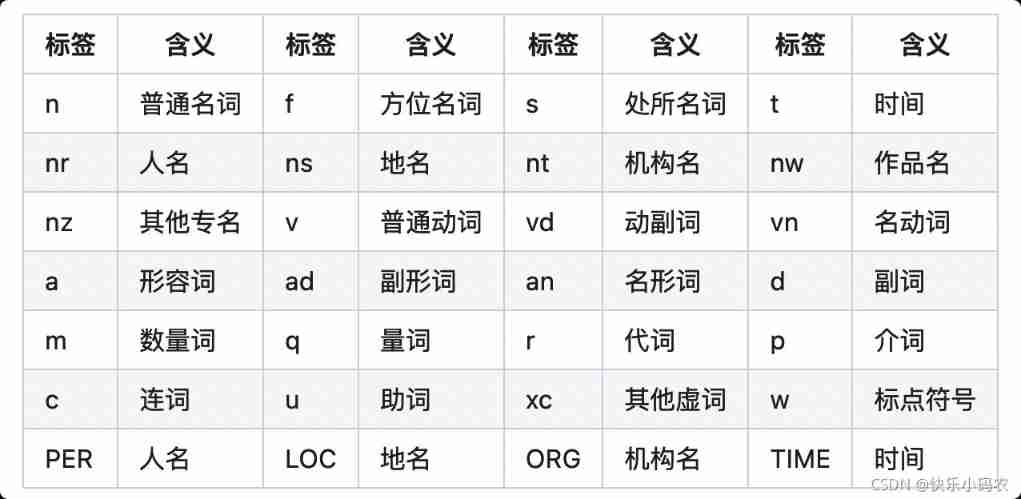
Meaning of Jieba participle part of speech tagging

Scanpy(七)基于scanorama整合scRNA-seq实现空间数据分析

NIPS 2014 | Two-Stream Convolutional Networks for Action Recognition in Videos 阅读笔记

Data preprocessing: discrete feature coding method
随机推荐
What about the exponential smoothing index?
Is there any risk in the security of new bonds
Similarity calculation method
打新债安不安全 有风险吗
紧急行政中止令下达 Juul暂时可以继续在美国销售电子烟产品
Word2vec, phrases, phraser, keyedvectors commonly used in gensim
Go language learning tutorial (13)
在哪个平台买股票开户安全?求分享
With the beauty of technology enabled design, vivo cooperates with well-known art institutes to create the "industry university research" plan
How to calculate critical weight indicators?
Can I grant database tables permission to delete column objects? Why?
atguigu----17-生命周期
C language "Recursion Series": recursively realizing the n-th power of X
关于I/O——内存与CPU与磁盘之间的关系
How to implement a system call
打新债真的安全吗? 风险大吗
Sharepoint:sharepoint server 2013 and adrms Integration Guide
The city chain technology platform is realizing the real value Internet reconstruction!
Common action types
Index analysis of DEMATEL model