当前位置:网站首页>Urgent! Tencent cloud container security supports the detection of Apache log4j2 vulnerabilities for the first time. It is in free trial
Urgent! Tencent cloud container security supports the detection of Apache log4j2 vulnerabilities for the first time. It is in free trial
2022-06-23 22:50:00 【Tencent virtual machine security】
Tencent cloud container security service team found tens of thousands of images affected by ApacheLog4j2 Remote Code Execution Vulnerability affects , There is a high risk ! In order to help customers across the network quickly repair vulnerabilities , Free trial for users , Log in to the console (https://console.cloud.tencent.com/tcss) You can experience it quickly .
Vulnerability description
Tencent cloud container security service team noticed ,12 month 9 Friday night ,Apache Log4j2 Details of the deserialization Remote Code Execution Vulnerability have been disclosed ,Apache Log4j-2 in JNDI Inject holes , When the program logs the data entered by the user , This vulnerability can be triggered , Successful exploitation of this vulnerability can execute arbitrary code on the target server .
Apache Log4j2 It's based on Java The logging tool for . The tool rewrites Log4j frame , And introduced a lot of rich features . The log framework is widely used in business system development , Used to record log information . Most of the time , Developers may write the error information caused by user input to the log . Because this component is widely used , The use threshold is very low , Great harm , Tencent security experts recommend that all users upgrade to a secure version as soon as possible .
Vulnerability risk
High-risk , The vulnerability affects a wide range , The use threshold is very low , Great harm .
CVSS score :10( highest )
Vulnerability details | Loophole PoC | Loophole EXP | Use in the field |
|---|---|---|---|
It has been made public | It is known that | It is known that | It has been found that |
Vulnerability version impact
Apache log4j2 2.0 - 2.14.1 Versions are affected .
Security version
Apache log4j-2.15.0-rc2 (2.15.0-rc1 edition , Verified by Tencent security experts, it can be bypassed )
Suggestions for bug fixing
Tencent cloud container security team recommends that users use Tencent container security services (TCSS) Perform a security scan on the used image , Detect and fix mirror vulnerabilities , The detailed operation steps are as follows :
(1) Log in to Tencent container security service console (https://console.cloud.tencent.com/tcss), receive 7 Day free trial ;
(2) Open the left side in turn “ Image security ”, Check the local image and warehouse image ;
(3) Local mirror / Warehouse mirroring function - Click one button to detect , Batch selection ApacheLog4j Component associated image , Confirm one click Scan ;
(4) Scan complete , Click Details to confirm that the asset exists Apache Log4j Component remote code execution vulnerability risk ;
(5) Upgrade to Apache Log4j To the safe version ;
(6) Go back to the container security service console and open it again “ Image security ”, Retest to ensure that assets are not subject to Apache Log4j Component Remote Code Execution Vulnerability affects ;
(7) After confirming the repair , Restart the container based on the new image .
tencent T-Sec Host security ( Cloud mirror )、 Tencent security T-Sec Web Application firewall (WAF)、 tencent T-Sec Advanced threat detection system (NDR、 Royal boundary )、 tencent T-Sec Cloud firewall products have supported detection, interception and utilization Apache Log4j2 Attack activities of Remote Code Execution Vulnerability .
Official patch
upgrade ApacheLog4j All relevant applications to the latest Log4j-2.15.0-rc2 edition . (2.15.0-rc1 edition , Verified by Tencent security experts, it can be bypassed )
Patch address
https://github.com/apache/logging-log4j2/releases/tag/log4j-2.15.0-rc2
Mitigation measures
Scheme 1 : modify Java Virtual machine startup parameters , add to -Dlog4j2.formatMsgNoLookups=true
Option two : Configure... In the code System.setProperty("log4j2.formatMsgNoLookups","true"), REPACK jar package
About Tencent's security engine capability
Tencent cloud container security service integrates Tencent security team's self-developed rhino engine capability , The rhinoceros engine is based on the public vulnerability database and the vulnerability information database accumulated by Tencent security for many years , It can accurately identify the vulnerabilities of system components and application components , Dynamically assess vulnerability risk , Accurately locate the vulnerabilities that need to be fixed first .
(1) Support Redhat、centos、ubuntu、debian、alpine And other mainstream operating systems , Support java、python、golang、nodejs、php、ruby And other mainstream programming languages .
(2) Dynamic vulnerability risk assessment is based on the general vulnerability scoring system (CVSS), According to the real propagation status of vulnerability exploitation 、 How easy it is to fix the vulnerability 、 The actual harm that a vulnerability can cause 、 Safety expert evaluation, etc , Dynamically assess the actual risk of vulnerabilities .
(3) There are many version types in system components and application components 、 Open loopholes, inaccurate information and other issues , The engine combines the research and judgment of automation operation and security experts , Provide multidimensional accurate vulnerability identification .
About Tencent container security service (TCSS)
Tencent container security service (Tencent Container Security Service, TCSS) Provide container asset management 、 Image security 、 Security services such as runtime intrusion detection , Ensure that the container is generated from the image 、 The full lifecycle of storage to runtime , Help enterprises build container safety protection system .
The Tencent container security service product team polished the product in combination with the safety management and operation experience of the largest container cluster in the industry , Promote the preparation and formulation of industry standards and specifications , And start 《 Container safety white paper 》, The present situation of domestic container environmental safety is analyzed and summarized , Help the standardization and healthy development of cloud native security ecology .
边栏推荐
- 应用实践 | Apache Doris 整合 Iceberg + Flink CDC 构建实时湖仓一体的联邦查询分析架构
- 运维故障经历分享
- 专业“搬砖”老司机总结的 12 条 SQL 优化方案,非常实用!
- Detailed explanation of flutter exception capture
- C language picture transcoding for performance testing
- How to use FTP to upload websites to the web
- What are the application flow restrictions of API gateway framework?
- How to set dynamic background for website construction what are the benefits of dynamic background
- Batch production of plant hangtag
- How to set the website address for website construction can the website be put on record
猜你喜欢

Slsa: accelerator for successful SBOM

Section 29 basic configuration case of Tianrongxin topgate firewall

為什麼你的數據圖譜分析圖上只顯示一個值?

SAVE: 软件分析验证和测试平台

为什么你的数据图谱分析图上只显示一个值?

Why is only one value displayed on your data graph?

C#/VB.NET Word转Text

混沌工程,了解一下

【技术干货】蚂蚁办公零信任的技术建设路线与特点
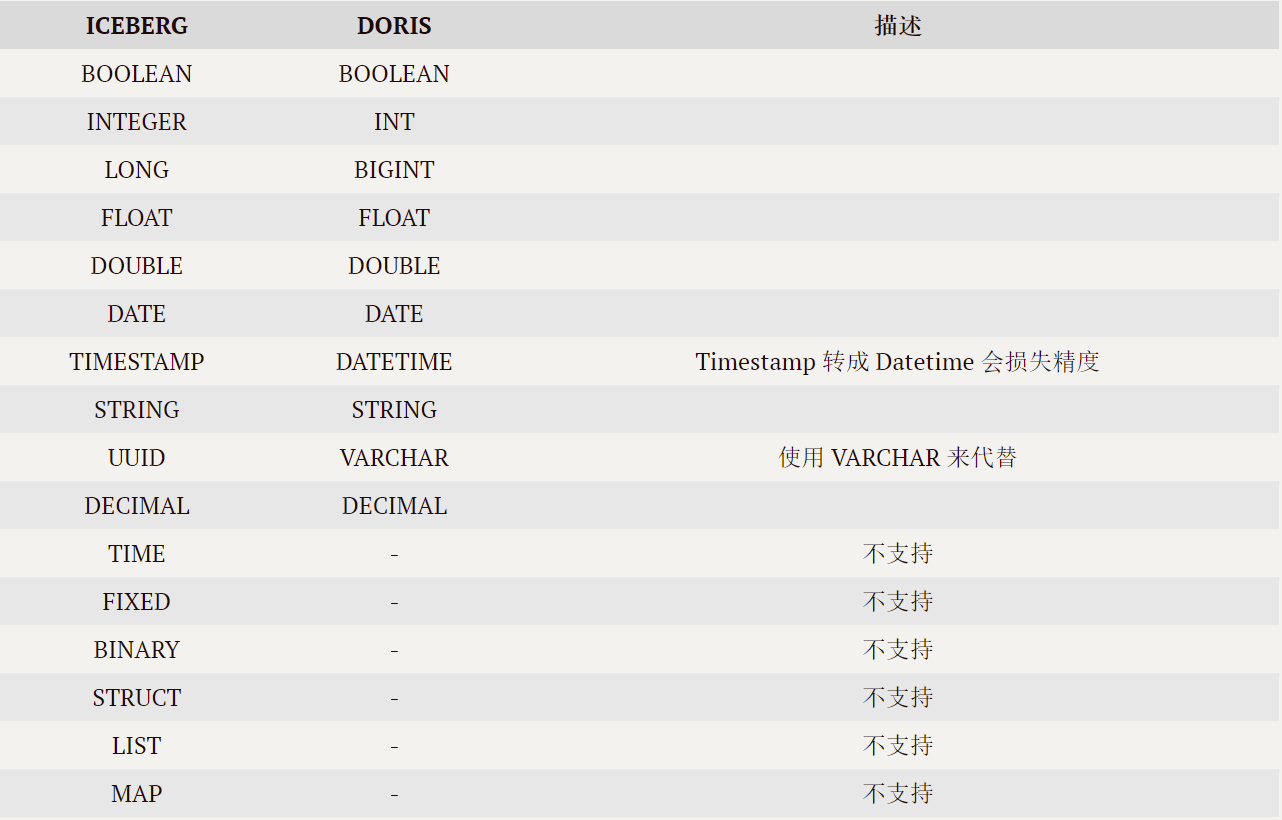
Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse
随机推荐
Problem solving: inittramfs unpacking failed:decoding failed
如何利用数仓创建时序表
openGauss Developer Day 2022正式开启,与开发者共建开源数据库根社区
How to use fortress remote server two types of Fortress
C#/VB.NET Word转Text
What is the difference between RosettaNet, EDI ANSI X12 and EDIFACT
Build the first security defense line for enterprises to go to the cloud Tencent's new generation cloud firewall product launch is about to open
How to set up links for website construction how to build a website
Understand the data consistency between MySQL and redis
API gateway monitoring function the importance of API gateway
The old CVM of Tencent cloud is migrated to the new CVM, and the IP remains unchanged
How to solve the problem that the GPU VNC has two mice with large deviation
Flush cache clear
Notes to nodejs (III)
Save: software analysis, verification and test platform
反序列化——php反序列化
专业“搬砖”老司机总结的 12 条 SQL 优化方案,非常实用!
新股民怎样炒股票开户?在线开户安全么?
First talk about the necessary skills of Architecture
Three ways to enable IPv6 on Tencent cloud