当前位置:网站首页>How to use fortress remote server two types of Fortress
How to use fortress remote server two types of Fortress
2022-06-23 22:26:00 【User 8715145】
Nowadays, people can not live without the Internet , A lot of information will be saved directly to the Internet , It's easy to leak , Therefore, we must protect important personal information . Many companies protect this information , Will use the fortress machine to strengthen the protection of information , that How to use the fortress remote server ? Here is a brief introduction to this problem .
How to use the fortress remote server
It is believed that many technicians used the fortress machine for the first time , Will search on the Internet how to use the fortress machine remote server and other related issues . Generally speaking , Want to use the fortress remote server , They all need to log in to the enterprise account , Transfer documents in the fortress account of the enterprise . Then modify the remote management permission of the fortress machine to the server , After setting the permissions, you can log in to the server at the terminal for remote management .
Two categories of Fortress machines
Speaking of Fortress , At present, there are two categories , The first category is fortress machines , Used by many large companies , In particular, Internet companies have the highest utilization rate , After all, the Internet involves a lot of information . besides , There are also open source fortress machines , This kind of Fortress machine has not been fully popularized in the market , It is an emerging technology , Safer than a commercial fortress , It is likely to become a mainstream in the future , Therefore, it is also a good choice for enterprises to use fortress machines .
I'll share the introduction about how to use the fortress remote server here . It is recommended that you use the fortress machine , Be sure to use it roughly first , In this way, when the fortress meets with opportunities and problems , There is no need to be ignorant and do not know how to solve it . If you really encounter the problem of using , Be sure to consult with professional technicians .
边栏推荐
- Core features and technical implementation of FISCO bcos v3.0
- How to solve the problem that the GPU VNC has two mice with large deviation
- What should be done when the encryptor fails to authenticate in the new version of easycvr?
- After CVM is configured with IPv6, it cannot be accessed as IPv6 or cannot access IPv6 sites
- Ranking of high cost performance commercial endowment insurance products in 2022
- Redis function discarding Encyclopedia redis:: delete() is deprecated solution
- Using the provider to transform the shit like code, the amount of code is reduced by 2/3!
- 2008R2 CFS with NFS protocol
- Nanny level anti crawling teaching, JS reverse implementation of font anti crawling
- [log service CLS] one click to start the efficient operation and maintenance journey of Tencent E-Sign
猜你喜欢

SLSA: 成功SBOM的促进剂

Pourquoi une seule valeur apparaît - elle sur votre carte de données?

In the eyes of the universe, how to correctly care about counting East and West?

Code implementation of CAD drawing online web measurement tool (measuring distance, area, angle, etc.)

openGauss Developer Day 2022正式开启,与开发者共建开源数据库根社区
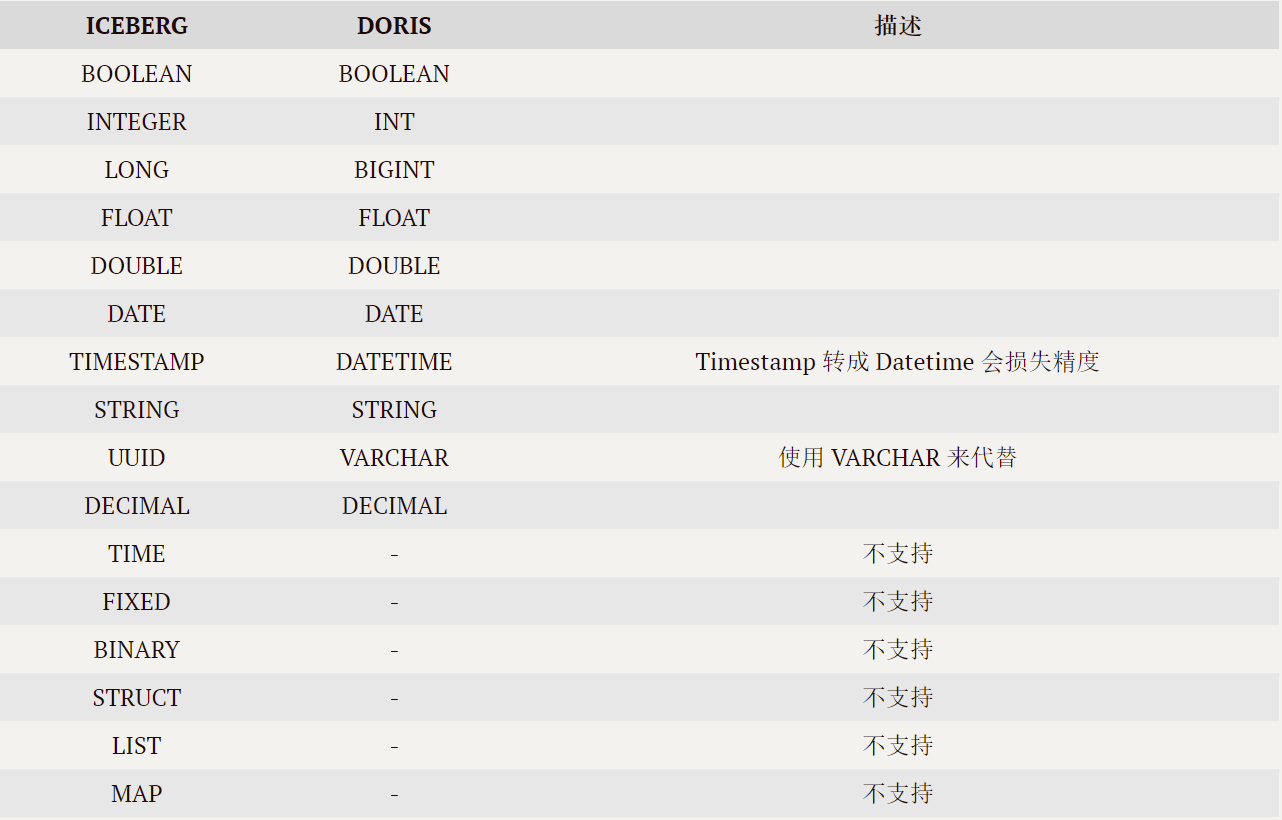
Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse

Beauty of script │ VBS introduction interactive practice

脚本之美│VBS 入门交互实战

Icml2022 | robust task representation for off-line meta reinforcement learning based on contrastive learning

Acl2022 | MVR: multi view document representation for open domain retrieval
随机推荐
What is the meaning of the two-way and one-way cn2 lines in Hong Kong, China?
Tencent News's practice based on Flink pipeline model
Command line enumeration, obtaining and modifying time zones
How to dynamically insert a picture into a QR code
Overall solution for digital transformation of medical supply chain management
Game security - call analysis - write code
Achieve scoring (Star scoring) effect through native JS
[emergency] log4j has released a new version of 2.17.0. Only by thoroughly understanding the cause of the vulnerability can we respond to changes with the same method
How to deploy API gateways and split services under multi services?
How to set the protective strip in the barcode
WordPress plugin WP guppy 1.1 - WP JSON API sensitive information disclosure
there can be only one auto column and it must be defined as a key
EDI mandatory manual
Pourquoi une seule valeur apparaît - elle sur votre carte de données?
How do fortress computers log in to the server? What is the role of the fortress machine?
WordPress plugin smart product review 1.0.4 - upload of any file
How to batch output EAN13 code to PDF
Recommend several idea plug-ins
Impala port
Dart series: smooth as silk, operating files and directories