当前位置:网站首页>CTF steganography
CTF steganography
2022-06-24 01:11:00 【ruochen】
#ctf Some personal summaries of steganography
One 、 File separation
1.binwalk binwalk -e sim.jpg Separate files
2.foremost foremost file name -o Output directory name
3.dd dd if= Source file of= Destination filename bs=1 count= A few pieces skip= Number of bytes to begin separation Parameter description : if=file Output file name of=file Output file name bs=bytes At the same time, set the read-write block size to bytes, May replace ibs and obs skip-blocks Skip from the beginning of the input file blocks Start copying after blocks
4. File merge : cat gif01 gif02 gif03 > 1.gif md5sum 1.gif see 1.gif Of MD5 Check value
Two 、 Picture steganography
1.zsteg xxx.png testing lsb Steganography
2.wbstego encryption bmp
3.TwwakPNG testing crc Check value
4.bftools stay Windows Of cmd Next , Decrypt the encrypted picture file
Format : bftools.exe decode braincopter The name of the picture to decrypt -output Output file name
5.stegdetect The tool detects the encryption method Mainly used to analyze peg file
stegdetect xxx.jpg
stegdetect -s Sensitivity xxx.jpgex
6.<img src="https://img-blog.csdnimg.cn/20200828231104472.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L3RhbnN0eV96aA==,size_16,color_FFFFFF,t_70#pic_center" alt=" Insert picture description here "> 7.<img src="https://img-blog.csdnimg.cn/20200828231122421.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L3RhbnN0eV96aA==,size_16,color_FFFFFF,t_70#pic_center" alt=" Insert picture description here ">
3、 ... and 、 Pseudo encryption of compressed files
I won't say the principle , Just use the simplest way Use ZipCenOp.jar Directly crack the pseudo encryption
1. java -jar ZipCenOp.jar e xxx.zip encryption 2. java -jar ZipCenOp.jar r xxx.zip Decrypt 3. java -jar ZipCenOp.jar r LOL.zip
rar File pseudo encryption : The first 24 individual 16 The mantissa of the hexadecimal number is changed to 0
Four 、 Traffic Forensics
wireshark Filter command :
1. Filter IP, Ruyuan IP Or the goal x.x.x.x ip.src eq x.x.x.x or ip.dst eq x.x.x.x 2. Filter port tcp.port eq 80 or udp.port eq 80 tcp.dstport ==80 Display only tcp The target port of the protocol is 80‘ tcp.srcport ==80 Display only tcp The source port of the protocol is 80 tcp.port >=1 and tvp.port <=80 3.http Mode filtering
<img src="https://img-blog.csdnimg.cn/20200828231341468.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L3RhbnN0eV96aA==,size_16,color_FFFFFF,t_70#pic_center" alt=" Insert picture description here "> Tracking flow
common HTTP Stream key content : 1、HTML Contains important information directly 2、 Upload or download file content , Usually contains the file name 、hash Value and other key information , Commonly used POST Request upload 3、 In a word, Trojans ,POST request , It contains eval, Content to use base64 encryption
wireshark Data Extraction file – Export object
Wireless traffic packet :
1.aircrack-ng Check cap package : aircrack-ng xxx.cap 2. use aircrack-ng Run the dictionary to crack the handshake package aircrack-ng xxx.cap -w pass.txt
边栏推荐
- 应用配置管理,基础原理分析
- [applet] when compiling the preview applet, a -80063 error prompt appears
- Part of the problem solution of unctf2020
- C language: structure array implementation to find the lowest student record
- Google Earth engine (GEE) - verification results used by NDVI, NDWI and NDBI to increase classification accuracy (random forest and cart classification)
- SQL database: summary of knowledge points, no suspension at the end of the period
- CVPR2022 | 可精简域适应
- MIP nerf: anti aliasing multiscale neural radiation field iccv2021
- 【CVPR 2022】高分辨率小目标检测:Cascaded Sparse Query for Accelerating High-Resolution Smal Object Detection
- 机器学习中 TP FP TN FN的概念
猜你喜欢

WinSCP和PuTTY的安装和使用
![2022 postgraduate entrance examination experience sharing [preliminary examination, school selection, re examination, adjustment, school recruitment and social recruitment]](/img/05/e204f526e2f3e90ed9a7ad0361a72e.png)
2022 postgraduate entrance examination experience sharing [preliminary examination, school selection, re examination, adjustment, school recruitment and social recruitment]

Perhaps the greatest romance of programmers is to commemorate their dead mother with a software

【ICPR 2021】遥感图中的密集小目标检测:Tiny Object Detection in Aerial Images

Zhongshanshan: engineers after being blasted will take off | ONEFLOW u
Shengdun technology joined dragon lizard community to build a new open source ecosystem

一次 MySQL 误操作导致的事故,「高可用」都顶不住了!

Error reported using worker: uncaught domexception: failed to construct 'worker': script at***

Cross domain and jsonp
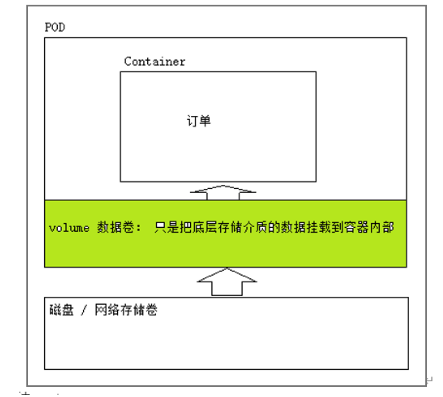
Common core resource objects of kubernetes
随机推荐
CVPR2022 | 可精简域适应
[planting grass by technology] 13 years' record of the prince of wool collecting on the cloud moving to Tencent cloud
Is it safe to open a stock account online now? Select a state-owned securities firm, and the fastest time to open an account is 8 minutes
LSF打开Job idle information以看job的cpu time/elapse time使用情况
Niu Xuechang's anniversary celebration: software promotion, limited time and free registration code!
If you want to open an account for stock trading, is it safe to open an account online-
13 `bs_duixiang.tag标签`得到一个tag对象
Common core resource objects of kubernetes
阿里巴巴面试题:多线程相关
Local cache selection (guava/caffeine/ohc) and performance comparison
Pure JS implementation determines whether the IP is pinged
ShardingSphere-proxy-5.0.0容量范围分片的实现(五)
Social recruitment interview is indispensable -- 1000 interview questions for Android engineers from Internet companies
JS input / output statements, variables
实时计算框架:Flink集群搭建与运行机制
CODING CD
C language: sorting with custom functions
Thread safety and lock optimization
Echo framework: automatically add requestid
How to write peer-reviewed papers
