当前位置:网站首页>There are some limitations in cluster expansion and contraction
There are some limitations in cluster expansion and contraction
2022-06-23 08:13:00 【User 7737280】
such as : A server node is down , The calculation formula starts from hash(key)% 3 Turned into hash(key)% 2, The results will change , At this point, you want to access a key, This key Open selection The approximate cache location rate will change , So before caching key The data will also lose its function and significance .
A large number of caches fail at the same time , Avalanche causing cache , This leads to the unavailability of the whole cache system , This is basically unacceptable , In order to solve and optimize the above situation , Uniformity hash The algorithm came into being ~ that , How does the consistent hash algorithm solve the above problems ?
The server maps to hash Ring At this time, the calculation formula starts from hash(key)% N Turned into **hash( The server ip)% 232**, Use the server IP address hash Calculation , Use the hash result to 232 modulus , The result must be a 0 To 2^32-1 Integer between , And this integer is mapped to hash The position on the ring represents a server , In turn node0、node1、node2 Open selection Three cache servers are mapped to hash On the ring . How does it optimize the addition and reduction of nodes in the cluster ,http://www.gongxuanwang.com Cache service caused by common modulo algorithm , The problem of large area unavailability ?
Let's take a look at the scenario of capacity expansion , If business volume surges , The system needs to be expanded to add a server node-4, just node-4 Mapped to node-1 and node-2 Between , Object mapping nodes in a clockwise direction , Found originally cached in node-2 On the object key-4、key-5 Is remapped to node-4 On , Open selection However, during the whole expansion process, only node-4 and node-1 A small amount of data between nodes . Uniformity Hash The algorithm introduces a Virtual node Mechanism , That is, calculate multiple for each server node hash value , They all map to hash On the ring , Objects mapped to these virtual nodes key, It will eventually be cached on the real node .
Virtual node hash The calculation can usually adopt , Of the corresponding node IP Address plus number suffix hash(10.24.23.227#1) The way , for instance ,node-1 node IP by 10.24.23.227, Normal calculation node-1http://www.gongxuanwang.com Of hash value .
hash(10.24.23.227#1)% 2^32Suppose we give node-1 Set up three virtual nodes ,node-1#1、node-1#2、node-1#3, Carry them on hash Take the mold after .
边栏推荐
- firewalld 配置文件的位置
- Deep learning ----- different methods to realize vgg16
- INT 104_LEC 06
- Does huangrong really exist?
- 5本财富自由好书的精华
- C# scrollView 向上滚动还是向下滚动
- 2 corrections de bogues dans l'outil aquatone
- Imperva- method of finding regular match timeout
- vtk. JS left mouse button sliding to change window level and window width
- Configuration asmx not accessible
猜你喜欢
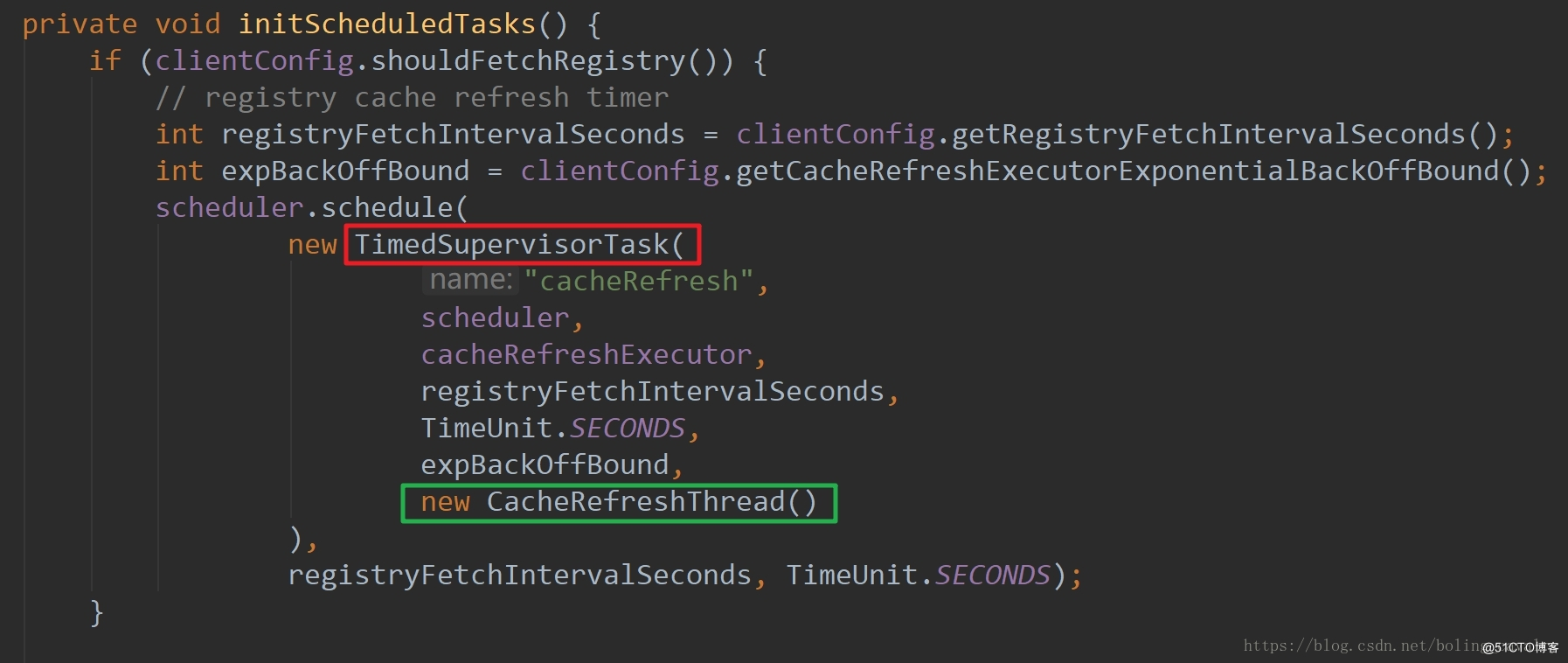
实战监听Eureka client的缓存更新

ThreadPoolExecutor线程池实现原理与源码解析
![Vulnhub | dc: 3 | [actual combat]](/img/97/e5ba86f2694fe1705c13c60484cff6.png)
Vulnhub | dc: 3 | [actual combat]

Deep learning ----- different methods to implement lenet-5 model

数据资产为王,解析企业数字化转型与数据资产管理的关系
套接字socket编程

81 sentences worth repeating
INT 104_ LEC 06

Imperva- method of finding regular match timeout

Socket programming (multi process)
随机推荐
5本财富自由好书的精华
华为云服务器弹性公网IP无法ping
Distributed ID generation
@What is the difference between controller and @restcontroller?
google常用语法
domain controller
PHP file contains -ctf
Markdown学习
Vulnhub | DC: 4 |【实战】
2 corrections de bogues dans l'outil aquatone
Quickly delete the node in the code_ modules
Vulnhub | dc: 3 | [actual combat]
生产环境服务器环境搭建+项目发布流程
Display proportion of sail soft accumulation diagram
Deep learning ----- convolution (conv2d) bottom layer
Decomposition - command injection
aquatone工具 中的2个bug修复
9 ways in which network security may change in 2022
11 string function
正则表达式使用案例