当前位置:网站首页>[Extension Program - cat scratch 1.0.15 _ online video and audio acquisition artifact _ installation tutorial plus acquisition]
[Extension Program - cat scratch 1.0.15 _ online video and audio acquisition artifact _ installation tutorial plus acquisition]
2022-07-24 20:08:00 【The king of scrolls is coming】
1. Cat scratch 1.0.15
1.1, download
Statement : What I use here is Google browser , Other browser installation steps are not clear ..
1.2, Cat scratch plug-in download link – Extraction code : 1111
1.3, open Google browser , Click the three dot expansion bar in the upper right corner of the page , Then click Settings .

1.4, Then click the extension program on the setup page .

1.5, Go to the extender page , Click developer mode , Then click load the extracted extension .
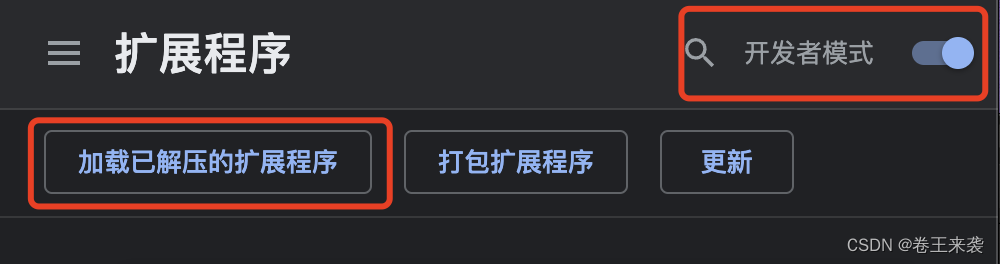
1.6, Then select the extracted file after downloading “ Clip cat scratch 1.0.15”, Click Select ,
边栏推荐
- [FreeRTOS] 10 event flag group
- About the largeheap attribute
- Analysis and Simulation of strlen function
- clip:learning transferable visual models from natural language supervision
- 【LeetCode】1184. 公交站间的距离
- Sword finger offer 47. the maximum value of gifts
- How to use the interface control telerik UI for WinForms development step progress bar?
- Working principle of envy of istio I
- How to integrate Kata in kubernetes cluster
- Hcip early summary
猜你喜欢

Duilib actual combat 1- imitate Baidu online disk login interface

Covid-19-20 - basic method of network segmentation based on vnet3d

BGP - border gateway protocol

Choose the appropriate container runtime for kubernetes

Leetcode 560 and the subarray of K (with negative numbers, one-time traversal prefix and), leetcode 438 find all alphabetic ectopic words in the string (optimized sliding window), leetcode 141 circula

Substr and substring function usage in SQL

【LeetCode】1184. 公交站间的距离

Maya coffee machine modeling

从码农转型大音乐家,你只差这些音乐处理工具
Leetcode 48 rotating image (horizontal + main diagonal), leetcode 221 maximum square (dynamic programming DP indicates the answer value with ij as the lower right corner), leetcode 240 searching two-d
随机推荐
Leetcode 48 rotating image (horizontal + main diagonal), leetcode 221 maximum square (dynamic programming DP indicates the answer value with ij as the lower right corner), leetcode 240 searching two-d
The ark compiler is coming. What about APK reinforcement
Introduction and advanced tutorial of Albert duilib
Detailed explanation of ELF format (I)
Machine learning job interview summary: five key points that resume should pay attention to
Maya coffee machine modeling
What is IDE (integrated development environment)
Getting started with COM programming 1- creating projects and writing interfaces
Software core data protection solution
Connect the smart WiFi remote control in the home assistant
英文翻译中文常见脏话
How to select software dongle
2019 Hangzhou Electric Multi School Game 9 6684 Rikka with game [game question]
纯C实现----------尼科彻斯定理
Microservice architecture | service monitoring and isolation - [sentinel] TBC
How to view the execution plan of a stored procedure in Youxuan database
The difference between delete, truncate and drop in MySQL
聊下自己转型测试开发的历程
Data transmission of different fragments in the same activity
Hide the middle digit of ID number