当前位置:网站首页>How to select software dongle
How to select software dongle
2022-07-24 19:22:00 【senseshield】
Software generally needs encryption and authorization , It can be done in one way , That is encryption lock . Encryption lock is used with software , The encryption lock must be inserted when opening the software , Encryption lock can realize the use of software within a time limit , LAN network lock mode , Limitations of software module functions .
Chip type
At present, the common types of encryption locks in the market are divided into single-chip microcomputer type and smart card chip . Smart card chips also include domestic smart cards and imported smart cards . Considering the current safety factors , The best choice of smart card chip for encryption lock is CC EAL 5+ Certified . This kind of smart card is almost impossible to be broken in terms of hardware .
Built in security algorithm
Encryption lock usually has a built-in security algorithm . Commonly used encryption lock algorithms are :
- RSA1024/RSA2048
- ECC192/ECC256/ECC384
- AES128/AES192/AES256
- DES/TDES
- SHA1/SHA256
Storage space
At present, the maximum storage space of encryption lock can reach 512K.
Interface standards
USB2.0 Full speed equipment
encryption : Shelling tools
The shelling tool can quickly encrypt and protect the code , No need to change the code , High security encryption can be completed in a few minutes .
边栏推荐
- Sequences, time series and prediction in tessorflow quizs on coursera (II)
- Summary of articles in 2020
- Convolutional Neural Networks in TensorFlow quizs on Coursera
- matplotlib
- Jedi survive and eat chicken F12 screenshot save path reference
- TCL programming style guide
- MySQL8.0学习记录20 - Trigger
- Nezha monitoring - server status monitoring, SSL certificate change expiration, Ping monitoring and scheduled task reminder
- He has been in charge of the British Society of engineering and technology for 13 years, and van nugget officially retired
- Analysis of dropout principle in deep learning
猜你喜欢

day 3

High speed ASIC packaging trends: integration, SKU and 25g+

【JVM学习04】JMM内存模型

PostgreSQL weekly news - July 13, 2022
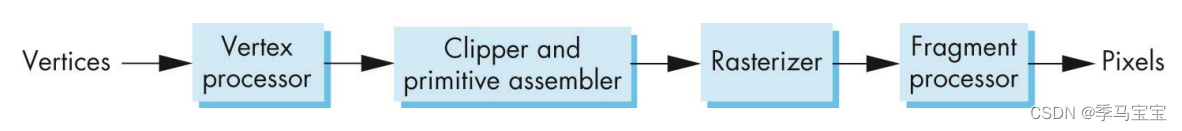
OPENGL学习(二)OPENGL渲染管线
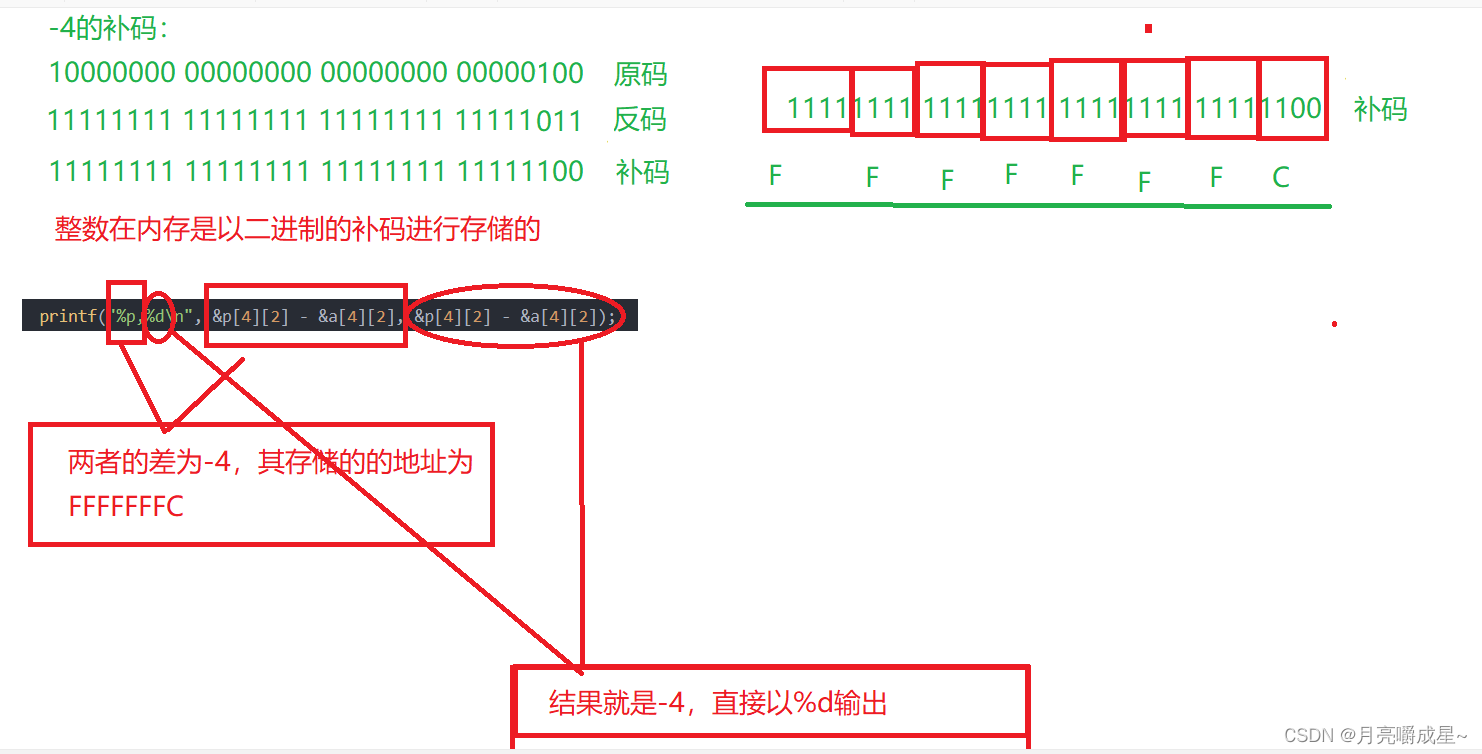
【校招面经】8道指针面试真题,快来检测自己掌握了几道。
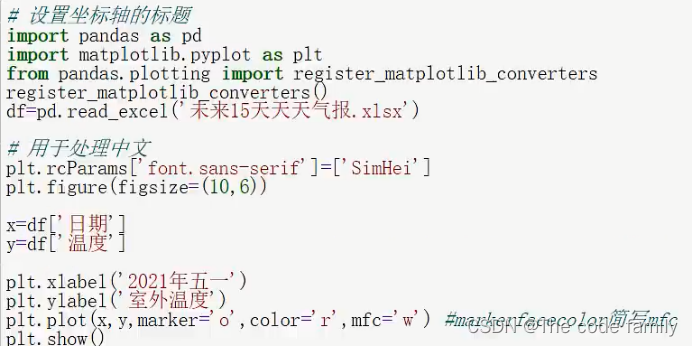
matplotlib

Convolutional neural network CNN

Hucang integrated release of full data value, sequoiadb V5.2 online conference heavy attack

Literature reading: gopose 3D human pose estimation using WiFi
随机推荐
Get module handle / base address
Tencent Browser service TBS usage
Implement a proxy pool from 0
Tupu software digital twin civil aviation flight networking, building a new business form of smart Civil Aviation
Channel state information (CSI) conjugate multiplication denoising method
Biopharmaceutical safety, power supply and production guarantee
Profile environment switching
[JVM learning 03] class loading and bytecode Technology
Getaverse,走向Web3的远方桥梁
MySQL version 5.7.9 SQL_ mode=only_ full_ group_ By question
day 2
Nezha monitoring - server status monitoring, SSL certificate change expiration, Ping monitoring and scheduled task reminder
MySQL8.0学习记录20 - Trigger
[JVM learning 04] JMM memory model
Convolutional Neural Networks in TensorFlow quizs on Coursera
On July 31, 2022, the dama-cdga/cdgp data governance certification class was opened!
Serial vector format (SVF) file format
Database index: index is not a panacea
He has been in charge of the British Society of engineering and technology for 13 years, and van nugget officially retired
Clion configuring WSL tool chain