当前位置:网站首页>Get and post are nothing more than TCP links in nature?
Get and post are nothing more than TCP links in nature?
2022-06-23 22:27:00 【Novice front end enthusiast】
Warm up chapter want to master thoroughly h Some knowledge points that must be understood .
browser | Length limit |
|---|---|
chrome( Google ) | url The length limit exceeds 8182 Characters return the errors listed at the beginning of this article . |
Microsoft Internet Explorer(IE browser ) | url The length limit is 2083(2K+53), Beyond that limit , Then automatically cut off ( if form Submit does not work ) |
firefox( Firefox ) | url The length is limited to 65 536 character , But it works URL The maximum length is not less than 100,000 Characters . |
Safari | Length limit is at least 80 000 character . |
Opera browser | Of url The length is limited to 190 000 character .Opera 9 Enter... In the address field 190 000 Characters can still be edited normally . |
Status Status code
Status code | explain |
|---|---|
200 | OK The request is successful , Commonly used in GET And request status |
300 | If the server itself already has the preferred feedback option , So in Location The URI; The browser may Location Value as the address for automatic redirection . Besides , Unless otherwise specified , Otherwise, the response is also cacheable . |
301 | The requested resource has been permanently moved to a new location , Be careful : For some uses HTTP/1.0 Browser for protocol , When they send POST The request got a 301 Response , The next redirection request will be GET The way . |
302 | The requested resources are temporarily from different URI Response request . Because such redirection is temporary , The client should continue to send future requests to the original address . Only in Cache-Control or Expires When specified in , This response is cacheable . |
400 | Bad Request Syntax error in client request , Server does not understand |
401 | Unauthorized The customer requires the user's identity authentication |
402 | Payment RequIred Retain , Future use |
403 | Forbidden The server understands the request from the requesting client , But refused to execute the request |
404 | Not Found The server could not find the field according to the client's request ( Webpage ). By this code , Website |
405 | Method Not Allowed Method in client request is forbidden |
415 | For the currently requested method and requested resource , The entity submitted in the request is not a supported format in the server , So the request was rejected . |
500 | Internal Sarver Error Server internal error , Unable to complete request |
501 | Internal Implemented The server does not support the requested feature , Unable to complete request |
502 | Bad Gateay When a server working as a gateway or proxy attempts to execute a request , An invalid response was received from the remote server |
504 | Gateway Time-out Server acting as gateway or proxy , Get the request from the remote server in case of crisis |
505 | HTTPVersion not supprted The server does not support the requested HTTP Version of protocol , Unable to complete processing |
There's no time to explain. Go straight to the hard goods ~~~
When we conduct joint debugging between the company and the back-end ,POST and GET This is our most commonly used request method .
But you really know POST and GET Request ?
GET | POST | |
|---|---|---|
Record the cache | Requested parameters / The record will be retained by the browser ,GET It is harmless when the browser is backout | POST It's not saved, it's safer , Back off POST The request will be made again |
Memory limit | because GET The request parameters will be in URL On display , It also says URL There are certain restrictions , So it will also affect GET It's a kind of reference | POST Requests are theoretically unlimited , It is mainly restricted by the background server , For example Tomcat Next cancel POST Size limit (Tomcat Default 2M) |
Security | GET The request mode message cannot contain entity content ,, therefore GET When requesting, you can expose the parameters in URL above , If some private data is not secure enough | POST Request we can use Form Form method and JSON Pass on the reference |
Bookmark collection | Can collect | Will not be collected |
visibility | Parameters can be visible to everyone | Will not be shown in URL in |
beautiful | GET If there are too many request parameters, it will be messy and difficult to understand | POST You can customize format fields and other information to make it easier to read |
Parameter type | GET We only accept ASCII character | and POST There is no limit to . |
high energy alert summary Please note that please pick up the paper towel ~~~
HTTP/HTTPS The agreement is based on IP/TCP, and POST and GET So is the bottom floor TCP/IP, You could say GET and POST All are TCP link , and GET and POST Everything you can do is the same , Do you want to GET add Request Body and POST close URL Parameters are technically feasible ~
summary :
GETAndPOSTEach has its own semantics , You can't mix them .GETWill produce a TCP Data packets ,POST Produce two TCP Data packets- about
GETMode request , The browser will http Request and Data Send it together , Server response 200( Status code ) - and
POST, Browser sends back first Header, Server response 100 Content, Browser sending Data, Server response200( Status code ). Not all browsers will POST Send two packets in ,Firefox Just send it once . - According to research , In a good network environment , The difference between the time to send a packet and the time to send two packets is negligible . And in the case of bad network environment , The two packages
TCPOn verifying packet integrity , It has great advantages .
边栏推荐
- What happened when the fortress remote login server was blocked? What can be done to solve it?
- WordPress preview email for wocomerce 1.6.8 cross site scripting
- there can be only one auto column and it must be defined as a key
- How to wrap QR code data
- Trident tutorial
- WordPress plugin WP guppy 1.1 - WP JSON API sensitive information disclosure
- 0day1- (cve-2021-44228) log4j2 rce recurrence
- Detailed explanation of lkadoc interface tool
- What if the fortress remote access server fails? What are the reasons why the fortress computer fails to connect to the server?
- Opengauss Developer Day 2022 was officially launched to build an open source database root community with developers
猜你喜欢

Opengauss Developer Day 2022 was officially launched to build an open source database root community with developers

In the eyes of the universe, how to correctly care about counting East and West?

Slsa: accelerator for successful SBOM

The latest research progress of domain generalization from CVPR 2022

SLSA: 成功SBOM的促进剂

Why is only one value displayed on your data graph?
Performance optimization of database 5- database, table and data migration

为什么你的数据图谱分析图上只显示一个值?
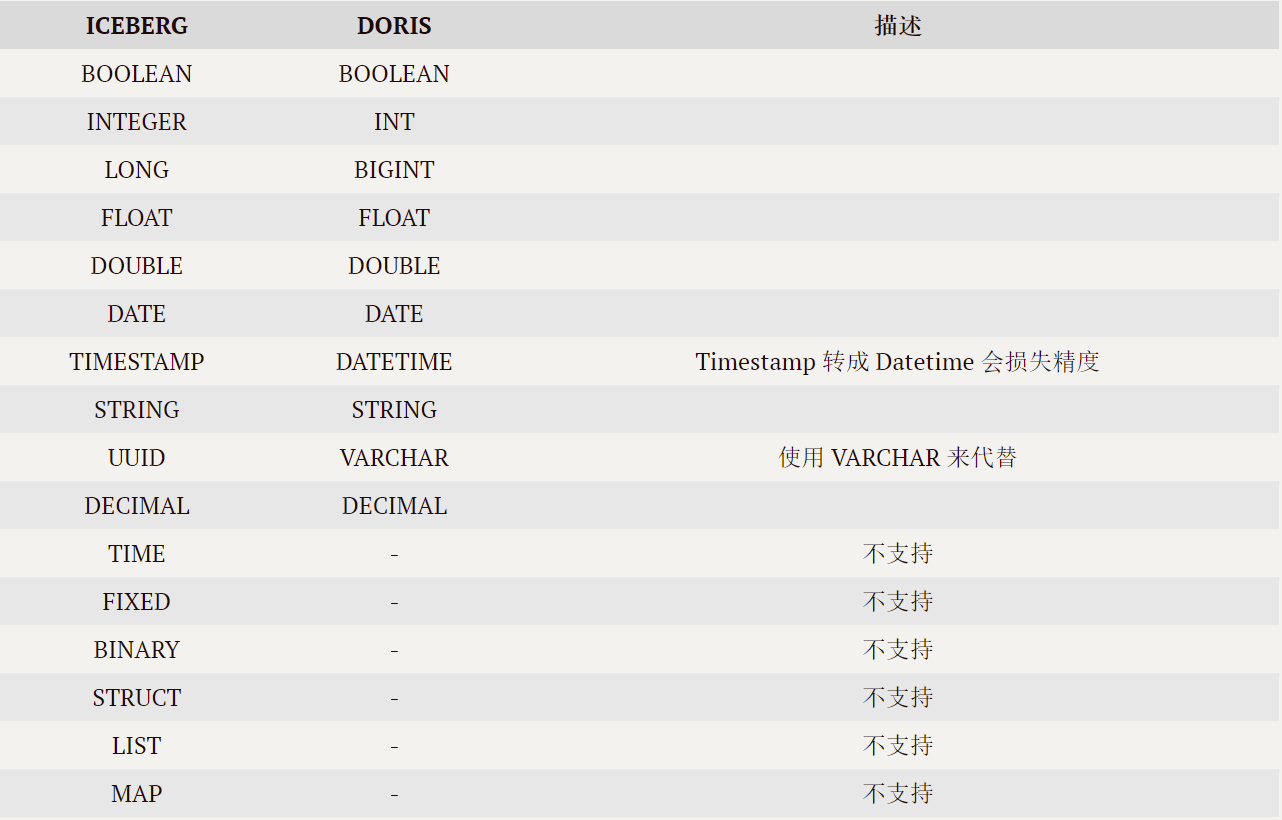
应用实践 | Apache Doris 整合 Iceberg + Flink CDC 构建实时湖仓一体的联邦查询分析架构
Hackinglab penetration test question 8:key can't find it again
随机推荐
Trident tutorial
How to provide value for banks through customer value Bi analysis
2021-12-19: find the missing numbers in all arrays. Give you an n
Environment construction of go language foundation
Service API version design and Practice
2008R2 CFS with NFS protocol
This article takes you to understand the JVM class loading mechanism
5 minutes to explain what is redis?
Server classification of hardware knowledge (2)
What is the difference between RosettaNet, EDI ANSI X12 and EDIFACT
Icml2022 | robust task representation for off-line meta reinforcement learning based on contrastive learning
2021-12-18: find all letter ectopic words in the string. Given two characters
What are the steps required for TFTP to log in to the server through the fortress machine? Operation guide for novice
Low code helps live e-commerce bring goods into the manufacturing industry, impacting the traditional supply chain model of the factory
Assembly deployment process
[tcapulusdb knowledge base] update data example (TDR table)
Tcapulusdb Jun · industry news collection
What is dynamic registration? What is static registration?
How to shut down the server in the fortress machine? What other operations can the fortress machine perform?
Targeted, real-time audio and video optimization in remote control
