当前位置:网站首页>What are the steps required for TFTP to log in to the server through the fortress machine? Operation guide for novice
What are the steps required for TFTP to log in to the server through the fortress machine? Operation guide for novice
2022-06-23 22:25:00 【User 8715145】
Now many large Internet enterprises will build fortress machines to protect the internal data security of enterprises , But the fortress machine is more flexible , Different from firewall , Therefore, in the process of operation, it is inevitable to encounter some incomprehensible places . Because the fortress machine needs several protocols to connect to the server , and tftp Is one of the simple file transfer protocols , that tftp Log in to the server through the fortress machine What are the steps of transmission ? Next, I will give you a simple answer .
Log in to the fortress machine
tftp If you log in to the server for transmission through the fortress machine, you need to log in to the fortress machine first to obtain administrator privileges , Open the transport protocol , Can copy the files of the local computer to the fortress machine . After copying the file to the fortress machine , Need to land fortress , User name and password are required during login , Authentication , After verification, you can view the target file on the fortress machine .
The fortress machine transfers files to the server
tftp It is not troublesome to log in to the server and transfer files through the fortress machine , Then transfer the file to the fortress machine , You need to log out of the fortress machine and log in to the server first , In the process of logging in to the server , Need to enter IP User name and password , After authentication, you can log in to the server . After logging in to the server, you can view the target files transmitted through the fortress machine .
About tftp The specific steps of logging in to the server to transfer files through the fortress machine have been answered for you , This operation is not difficult for novices , If you really don't have this talent , Unfamiliar with operation , You can find a professional to help with the operation , By the way, you can learn the specific operation .
边栏推荐
- The latest research progress of domain generalization from CVPR 2022
- Detailed explanation of bitmap optimization
- How to control the quality of omics research—— Mosein
- Why don't people like PHP?
- Statistics of clinical trials - Calculation of tumor trial endpoint
- Achieve scoring (Star scoring) effect through native JS
- EDI mandatory manual
- WordPress plugin wpschoolpress 2.1.16 -'multiple'cross site scripting (XSS)
- Freiburg University, Hildesheim University and other universities in Germany jointly | zero shot automl with pre trained models (zero sample automl based on pre training model)
- Flutter Utils
猜你喜欢

為什麼你的數據圖譜分析圖上只顯示一個值?

使用 Provider 改造屎一样的代码,代码量降低了2/3!

In the eyes of the universe, how to correctly care about counting East and West?

北大、加州伯克利大學等聯合| Domain-Adaptive Text Classification with Structured Knowledge from Unlabeled Data(基於未標記數據的結構化知識的領域自適應文本分類)

在宇宙的眼眸下,如何正确地关心东数西算?

Peking University, University of California Berkeley and others jointly | domain adaptive text classification with structured knowledge from unlabeled data (Domain Adaptive Text Classification Based o
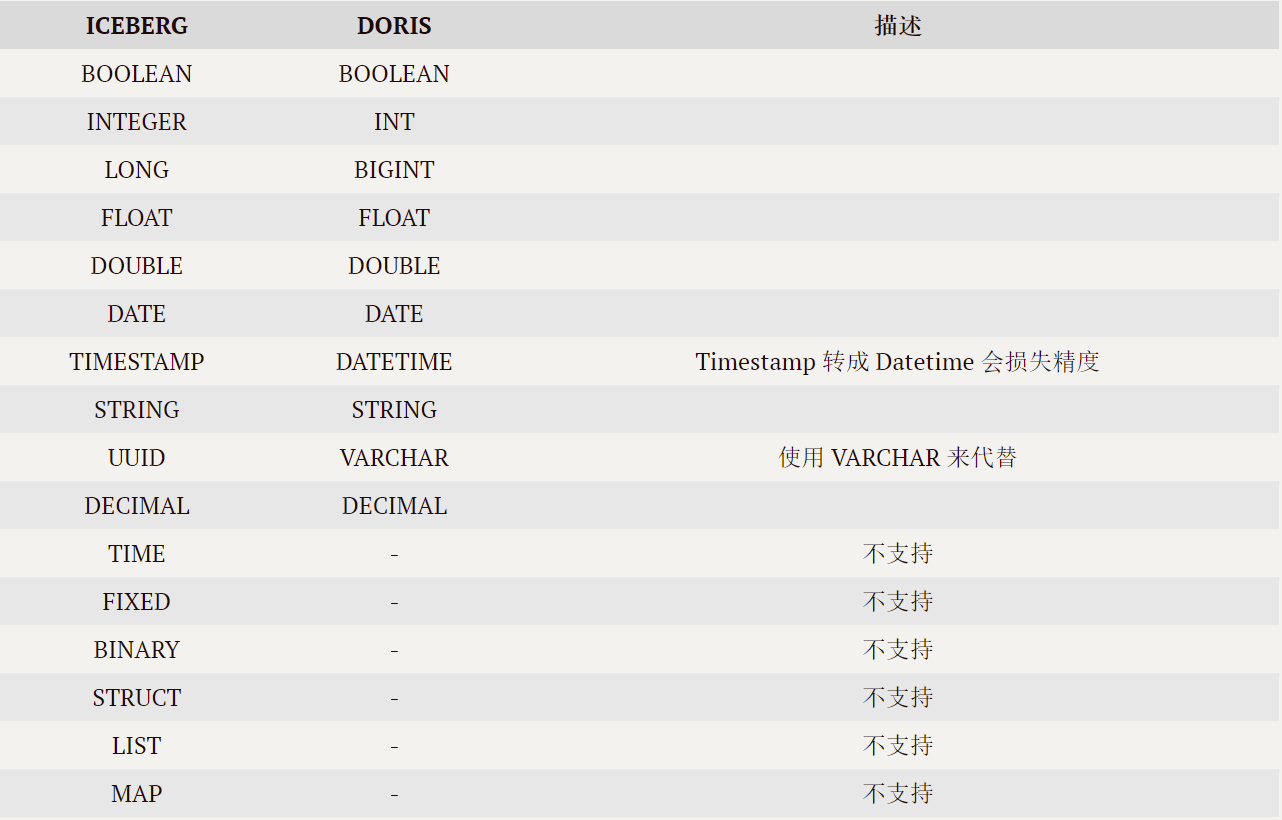
Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse

Icml2022 | robust task representation for off-line meta reinforcement learning based on contrastive learning

从CVPR 2022看域泛化(Domain Generalization)最新研究进展

Pourquoi une seule valeur apparaît - elle sur votre carte de données?
随机推荐
Knowda: all in one knowledge mixture model for data augmentation in feed shot NLP
CMU博士论文 | 通过记忆的元强化学习,118页pdf
Tencent cloud server ubuntu18 installs MySQL and logs in remotely
Teach you how to write a delay queue
Deep understanding of leakcanary
[tcapulusdb knowledge base] reading data example (TDR table)
Why is easycvr cascaded to the parent platform not displayed?
Summary of redis Functions PHP version
Detailed explanation of flutter exception capture
University of North China, Berkeley University of California, etc. | Domain Adaptive Text Classification with structural Knowledge from unlabeled data
Pourquoi une seule valeur apparaît - elle sur votre carte de données?
脚本之美│VBS 入门交互实战
Assembly deployment process
Intelligent storage | high speed HD media processing capability
WordPress preview email for wocomerce 1.6.8 cross site scripting
Low code technology
Redis function discarding Encyclopedia redis:: delete() is deprecated solution
Using the provider to transform the shit like code, the amount of code is reduced by 2/3!
游戏安全丨喊话CALL分析-写代码
Huawei hardware configuration command, recommended collection