当前位置:网站首页>Huawei device remote login (Telnet, SSH) configuration
Huawei device remote login (Telnet, SSH) configuration
2022-07-25 08:22:00 【wespten】
One 、Telnet Login configuration
A switch can pass Telnet The conditions for login are :
The switch has been configured IP Address ;
The switch has been configured with a remote login password ;
The switch has been configured with a privileged password ;
The switch has been connected to the network and started to work ;
At this time , We can use a computer in the network , Type... On the command line “telnet Switch IP Address ” Log in to the switch to configure it .
If the logged in switch is not configured with a remote login password , Will be displayed “Password required, but none set” Error message for ; If the privileged password is not set , When entering privileged mode, it will display “%No password set” Error message for .
therefore , For a newly purchased switch , You must first configure the switch with the console IP Address and remote login password , In the future, you can use remote login to manage this switch .
1. Configuration example :
Configure the switch with the console IP Address 、 Remote login password and privileged password .
Switch>enable
Switch#configure terminal
Switch(config)#interface vlan 1
Switch(config-if)#ip address 192.168.1.5 255.255.255.0
Switch(config-if)#exit
Switch(config)#line vty 0 4
Switch(config-line)#login
Switch(config-line)#password 123
Switch(config-line)#exit
Switch(config)#enable secret 456
Switch(config)#end
Switch#After completing the above configuration , We can use a computer in the network , use telnet 192.168.1.5 Log in to the switch , The login password is 123. After logging in , The password to enter privileged mode is 456.
By default ,Telnet Server It's open , Anyone can use Telnet access switch , We can prohibit the use of Telnet access switch .
Pattern : Configure in global configuration mode .
close Telnet Server:
Switch(config)#no enable service telnet-serverTurn on Telnet Server:
Switch(config)#enable service telnet-serverexplain : close Telnet Access does not affect the use of the console 、Web and SNMP access switch .
2. Configuration example :
Turn off the remote login access of the switch .
Switch>enable
Switch#configure terminal
Switch(config)#no enable service telnet-serverWhen Telnet Server On , We can configure to allow remote login IP Address , such , You can restrict users to log in to the switch remotely only from the specified computer .
Pattern : Configure in global configuration mode .
Configuration command :
Switch(config)#service telnet host host-ipParameters host-ip For users who are allowed to log in remotely IP Address .
explain : You can use this command multiple times to set up multiple legal users who are allowed to log in remotely IP. If you do not configure this , By default, users are not restricted IP Address .
Delete configured Telnet Limit :
Switch(config)#no service telnet host host-ipThis command only deletes the specified IP.
Switch(config)#no service telnet hostThis command deletes all IP.
3. Configuration example :
Only IP The address is 192.168.1.10 and 192.168.1.30 For users of Telnet Log in to the switch .
Switch>enable
Switch#configure terminal
Switch(config)#service telnet host 192.168.1.10
Switch(config)#service telnet host 192.168.1.30When you use Telnet After logging in to the switch , If there is no input within the set timeout , The exchange will automatically disconnect the connection , Therefore, setting the timeout has a certain protective effect .
Telnet The default timeout is 5 minute , You can modify it with commands .
Pattern : Line configuration mode
Configuration command :
Switch(config-line)#exec-timeout timeParameters time Set the timeout for , The unit is in seconds , The value is 0~3600, If set to 0, Indicates unlimited timeout .
explain : You must first use line vty Command to enter the line mode of remote login and then configure the timeout .
Delete configured Telnet Timeout time :
Switch(config-line)#no exec-timeoutAfter deleting , The timeout is restored to the default 5 minute .
4. Configuration example :
Set the timeout of remote login to 10 minute (600 second ).
Switch>enable
Switch#configure terminal
Switch(config)#line vty
Switch(config-line)#exec-timeout 600In privileged mode , use show service Commands can be viewed Telnet Server Is it disabled .
5. Configuration example :
Check the switch Telnet Server The state of .
Switch>enable
Switch#show service
SSH-server : Enabled
Snmp-agent : Disabled
Telnet-server : Enabled
Web-server : Enabledshow service The command says SSH Server、SNMP Agent、Telnet Server and Web Server The enabling status of four management modes ,“Enabled” For opening ,“Disabled” To close .
Two 、SSH Login configuration
1. Turn on telnet service :
stelnet server enable2. aaa Create users under :
aaa
local-user test001 password irreversible-cipher [email protected]
local-user test001 service-type terminal ssh
local-user test001 level 153. Enable the user to log in to the device for the first time without checking the public key .
ssh client first-time enable When STelnet/SFTP The client logs in for the first time SSH Server time , Because at this time STelnet/SFTP The client has not been saved SSH The public key of the server . So in STelnet/SFTP The client logs in for the first time SSH Server time , incorrect SSH Check the validity of the public key of the server . After logging in , The system will automatically allocate and save the public key , Authenticate for next login .
4. vty The next configuration authentication mode is aaa, Supported by SSH Protocol login device
user-interface vty 0 9
authentication-mode aaa
protocol inbound ssh
user privilege level 32 The steps of the local-user test001 level 15 Prior to the 4 The steps of the user privilege level 3, When 2 Step is not configured local-user test001 level 15 when , Then use 4 The steps of the user privilege level 3
5. Features added in the new version .
ssh ipv6 server-source all-interfacessh server-source all-interface Appoint SSH The source interface of the server is all configurations on the device ip The interface of or ssh server-source -i interface xxxx, Appoint SSH The source interface of the server is an interface . If you configure , You'll have a preference for ssh server-source -i The interface specified by the command acts as ssh The source interface of the server , If the specified source interface cannot login successfully , Then the interface login will be selected from other valid interfaces .
After the above steps, you can use ssh Sign in .
6. establish ssh user
Whether to create ssh user Users depend on ssh authentication-type default password command . If the undo ssh authentication-type default password, I need to create ssh user .
If the ssh authentication-type default password No need to create ssh user To log in .
If the undo ssh authentication-type default password I need to create ssh user To log in .
ssh user test001
ssh user test001 authentication-type password
ssh user test001 service-type stelnetIf ssh authentication-type default password Created again ssh user, Then use ssh user Sign in , If not configured at this time ssh user test002 authentication-type or ssh user test002 service-type stelnet Can't log in .
7. To configure acl
acl ipv6 number 2001
description For SSH v6
rule 5 permit source 2409::/128
acl number 2000
description For STelnet
rule 5 permit source 1.1.1.0 0.0.0.255
ssh server acl 2000
ssh ipv6 server acl 2001
user-interface vty 0 9
acl ipv6 2001 inbound
acl 2000 inboundnotes :ssh server acl 2000 and acl 2000 inbound There is a refusal , The action is to refuse .
Of each business module ACL Default actions and ACL Processing mechanism :

stay telnet and stelnet When using , If all rule Did not match to the , Even if you don't deserve deny, The default action is deny. If acl There is no rule, The default is permit allow .
边栏推荐
- Learn when playing No 6 | the magic of document library lies in
- 牛客动态规划训练
- Literature learning (part101) -- converge clustering
- Chapter 3 business function development (realize the real-time response of the select all button)
- [5g NR] 3GPP common protocol sorting
- serialization and deserialization
- 一次简单的SQL注入靶场练习
- 【5G NR】UE注册拒绝原因
- Teach you to understand the computer optometry sheet
- Learn when playing No 4 | can you take an online exam in programming? Right here →
猜你喜欢

Advanced C language (11) - user defined data types

Redis学习

【着色器实现Shadow投影效果_Shader效果第八篇】

Redis learning

@Autowired注解的实现原理
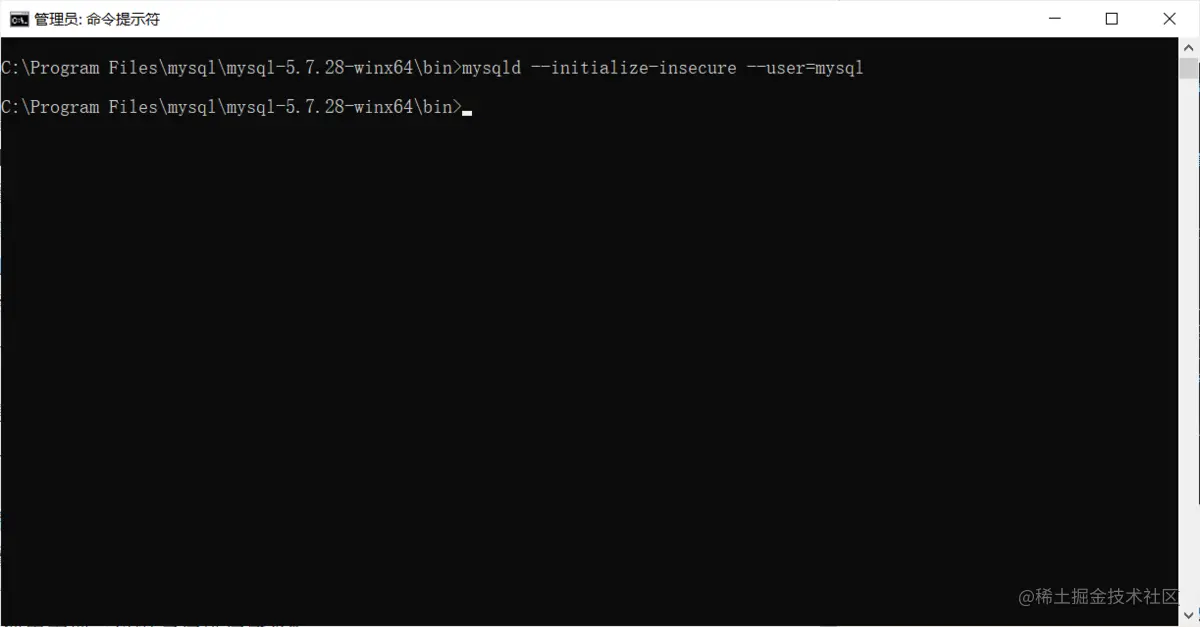
Mysql-5.7 installation

Data warehouse ODS, DWD floor, 220616, HM,

How to set up a personal website for free
Advanced C language (XIII) - Example Analysis of dynamic memory management

Rk3399 development board i2c4 attaching EEPROM instance
随机推荐
Brush the title "sword finger offer" day01
Learn when playing No 6 | the magic of document library lies in
Changes were made to tables that cannot be recreated or the prevent saving changes that require the table to be recreated option was enabled
【黑马程序员】Redis学习笔记002:持久化:RDB 和 AOF
JS pop up picture Lightbox light box plug-in spotlight.js
Didi - dispatching
[dark horse programmer] redis learning notes 003: redis transactions
How to obtain the intersection / subtraction / Union of two sets by MySQL
Redis学习
第3章业务功能开发(修改线索,数据回显并修改数据)
Node+js build time server
Redis最佳实践
Codeforces Round #809 Editorial(A,B,C)
Raspberry Pie 3 connected to WiFi
牛客动态规划训练
My creation anniversary
【FFmpeg】mp4转yuv
[5g NR] 3GPP common protocol sorting
Learn when playing No 4 | can you take an online exam in programming? Right here →
Eureka forced offline service