当前位置:网站首页>SSH Remote Access and control
SSH Remote Access and control
2022-07-24 06:36:00 【Walking Di five flowers】
Catalog
Two 、SSH Service configuration
1、sshd The service supports two authentication methods :
3、OpenSSH Server side /etc/ssh/sshd_config Profile parsing
3、 ... and 、SSH Remote login experiment
One 、SSH Remote management
1、SSH agreement
① It's a secure channel protocol ② The communication data is encrypted , For remote administration
The Internet
SSH client <----------------------------------------------------->SSH Server side
Data transmission is encrypted , Can prevent information leakage
Data transmission is compressed , Can improve transmission speed
SSH client :Putty 、Xshell 、CRT
SSH Server side :OpenSSH
2、OpenSSH
① The service name :sshd
② Server main program :/usr/sbin/sshd
③ Server profile :/etc/ssh/sshd_config( stay centos7 in , Default installed openssh Related packages , And will install sshd service )
④sshd The default port used by the service is 22
⑤ ssh_config and sshd_config All are ssh The configuration file for the server , The difference between the two is that the former is a configuration file for the client , The latter is for the configuration file of the server
3、OpenSSH The server
① User login control
Ban root user 、 Empty password users
Limit login verification time 、 Retry count
AllowUsers、DenyUsers
② Service listening options
Port number 、 Protocol version 、 monitor IP Address
Disable reverse parsing
③ Login authentication method
Password authentication : Check the user name 、 Does the password match
Password pair verification : Check the customer's private key 、 Whether the server public key matches
④ Create a key pair in the client
ssh-keygen command
Available encryption algorithms :RSA、ECDSA、 or DSA
Two 、SSH Service configuration
1、sshd The service supports two authentication methods :
① Password authentication : Login name of the local system user in the server 、 Password verification . This is the easiest way to use , But from a client perspective , The server you are connecting to may be impersonated ; From a server perspective , When encountering password exhaustion ( Brute force ) When attacking, the defense ability is relatively weak .
② Key pair validation : Matching key information is required to pass the verification . Usually create a pair of key files in the client first ( Public key 、 Private key ), Then put the public key file in the specified location in the server . When logging in remotely , The system will use the public key 、 The private key is encrypted / Decryption Association verification , Greatly enhance the security of remote management . This method is not easy to be counterfeited , No login and interaction , stay Shell Is widely used in .
There are two kinds of key pairs , One is symmetric key , One is asymmetric key ( The type of experiment in this chapter )
Asymmetric : RSA , Create a public key and a private key . If it's verified , The private key must match the public key , Before you can log in 、 Interaction , Otherwise, refuse , stay linux In the system, public key and private key , Just two files .
2、 Use scp Remote Replication
① Downlink replication : Copy the files in the remote host to this computer
scp root @ 192.168.159.68:/etc/passwd /opt/ceshi.txt

② Uplink replication : Will the machine /opt/ceshi.txt Directory copy to remote host
scp -r /opt/ ceshi.txt/ [email protected] : / mnt
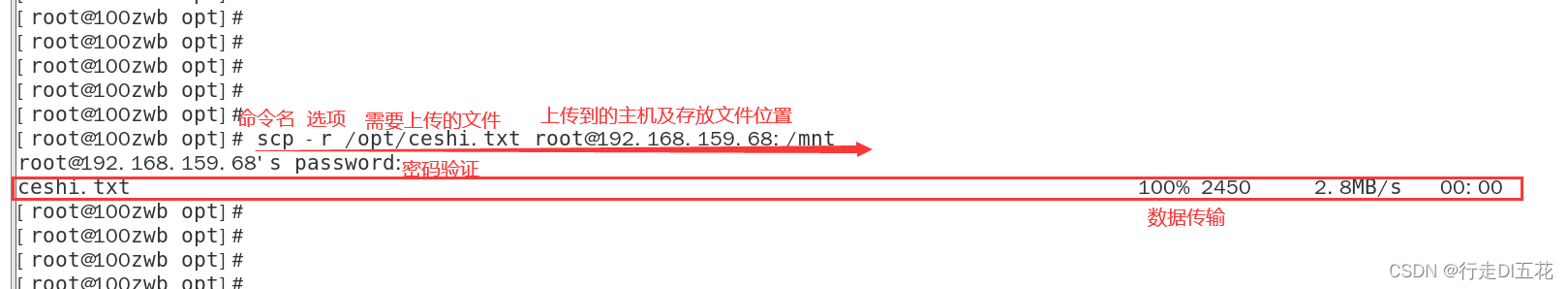
View the uploaded file

3、OpenSSH Server side /etc/ssh/sshd_config Profile parsing
The main parameters that need to be configured are modified as required .

3、 ... and 、SSH Remote login experiment
Login method : ssh [ Options ] user @ host IP Address -P Port number
Options -P Indicates that it is used to specify the login port . By default, it means that 22 Port login
① Subjects : Two virtual machines
by centos 7.6-1 The host address is 192.168.159.68
by centos 7.6-2 The host address is 192.168.159.100
Modify the configuration file , Other options default , Modify an option to prohibit reverse parsing DNS, Optimize it .




Verification one 、 No key pair verification configuration , General login
②192.168.159.100 Remote login 192.168.159.68

Verification II 、 Configure asymmetric key pairs
192.168.159.100 Remote login 192.168.159.68
① Create an asymmetric key

② View key

③ Push the key to 192.168.159.68

④ Remote login test

PS: The asymmetric key established in this way is one-way , Now? 192.168.159.100 Host login 192.168.159.68 No password required , but 192.168.159.68 Remote login 192.168.159.100 Or you need to enter a password to log in .( If you want to log in without secret , Need to be in 192.168.159.100 Configure the key on the host )
When the key and password login exist at the same time , The system will give priority to key login .
Conclusion :
To study the scp Remote Replication 、ssh Remote login , Know the method of remote login , And asymmetric key configuration , It is verified by experiments
边栏推荐
- Summary of ten common vulnerabilities (principle, harm, defense)
- 一批面试题及答案_20180403最新整理
- Modeling of XML
- Leetcode refers to offer jz5 to replace the space string
- Top 10 vulnerability assessment and penetration testing tools
- Use and principle of spark broadcast variable and accumulator
- PXE技术网络装机
- Flink function (2): checkpointedfunction
- RAID的配置实验
- FTP service and experiment
猜你喜欢

LVM与磁盘配额

Common commands and package management of go language

RESTful API介绍

进行挂载永久挂载后无法开机

Li Kou 986. Intersection of interval lists

RAID的配置实验

MySQL Index & execution plan

Top 10 vulnerability assessment and penetration testing tools

JSP tag 02

Do not rent servers, build your own personal business website (3)
随机推荐
PXE technology network installation
A batch of interview questions and answers_ 20180403 latest arrangement
Simple three-step fast intranet penetration
Playing RTSP video stream on webpage
LVM与磁盘配额
Server hardware and RAID configuration practice
go语言常用命令和包管理
使用自定义zabbix包(4.0.5版本)安装agent和proxy
Sword finger offer jz10 Fibonacci sequence
Process and planned task management
Flink checkpoint configuration details
Wasm vs EVM, Boca's choice predicts the future of the public chain
Solution of forgetting root password in mysql5.7 under Windows
General paging 01
Homework in the second week
LVM and disk quota
mysql 忘记退出直接关闭窗口现在要删除整个文件夹如何删除
[award issuance] the results of the first essay solicitation activity in oneos zone were announced
Customize ZABBIX agent RPM package
Public access intranet IIS website server [no public IP required]