当前位置:网站首页>HNU network counting experiment: experiment I application protocol and packet analysis experiment (using Wireshark)
HNU network counting experiment: experiment I application protocol and packet analysis experiment (using Wireshark)
2022-06-25 21:43:00 【HNU Yuelu mountain lady】
First words
The first experiment was simple , I don't really remember what I did at that time …
Why don't you refer to other people's ???
The experiment purpose
Through this experiment , Have a good command of Wireshark Operation and use of , Learning is right HTTP Protocol analysis .
Experimental content
1.HTTP Protocol Brief
HTTP It's the hypertext transfer protocol (Hyper Text Transfer Protocol) Abbreviation , be used for WWW service .
(1)HTTP How it works
HTTP Is a transaction oriented client server protocol . Even though HTTP Use TCP As the underlying transport protocol , but HTTP Protocol is stateless . in other words , Each transaction is handled independently . When a transaction begins , Just stay web Establish a TCP Connect , And release the connection when the transaction ends . Besides , customer Users can use multiple ports and servers (80 port ) Establish multiple connections between . Its working process includes the following stages .
① Server listening TCP port 80, To find out if there's a browser ( Customer process ) Make a connection request to it ;
② Once a connection request is detected , Connect now .
③ The browser sends a request to the server to browse a certain page , The server then returns the requested page in response .
④ Release TCP Connect .
Interaction of requests and responses between browser and server , Must follow HTTP The prescribed forms and rules .
When the user enters the address field of the browser to access HTTP Server address , Browser and access HTTP clothing The working process of the server is as follows :
① The browser analyzes the URL And to the local DNS Server request IP To analyze ;
② DNS The server resolves that HTTP Server's IP Address and will IP Address back to browser ;
③ Browser and HTTP Server setup TCP Connect , If the connection is successful , Then go to the next step ;
④ Browser direction HTTP The server sends a request message ( contain GET Information ), Request access to the specified page of the server ;
⑤ The server responds , Send the page the browser is going to visit to the browser , During page transfer , The browser will open multiple ports , Establish multiple connections with the server ;
⑥ Release TCP Connect ;
⑦ The browser receives the page and displays it to the user .
2)HTTP Message format
HTTP There are two types of messages : Request message from client to server and response message from server to client .
In the figure 1.1 in , There are spaces between each field , There is a carriage return at the end of each line . The meaning of each field is as follows :
① The request line consists of three fields :
· Method fields , The most common method is “GET”, Indicates a request to read a web page . The common method is “HEAD( Refers to reading the first part of the page )” and “POST( Request to accept additional information );
·URL The field is the file name on the host , Because it's building TCP You already have a host name when you connect ;
· The version field describes the HTTP Version of protocol , It's usually “HTTP/1.1”.
② The status line also has three fields :
· The first field is equivalent to the third field of the request line ;
· The second field is generally “200”, It means that everything is normal , The status codes have 41 Kind of , Commonly used :301 ( The website has been transferred ),400( The server could not understand the request message ),404( The server does not have the object for the lock request ) etc. ;
· The third field interprets the phrase of the status code .
③ As the case may be , The number of rows in the first row is variable . The first part of the request has Accept Field , Its value represents the browser What type of media is acceptable ;Accept-language, Its value represents the language used by the browser ;User-agent Indicates the type of browser available . In the first part of the response Date、Server、Content-Type、Content-Length Etc . There are... In both the request header and the response header Connection Field , Its value is Keep-Alive or Close, Indicates that the server keeps the connection or closes the connection after delivering the requested object .
④ If... Is used in the request message “GET” Method , There is no entity body behind the first line , When using “POST” The method is , Additional information is filled in the body of the entity . In response message , The entity body part is the object sent by the server to the customer .
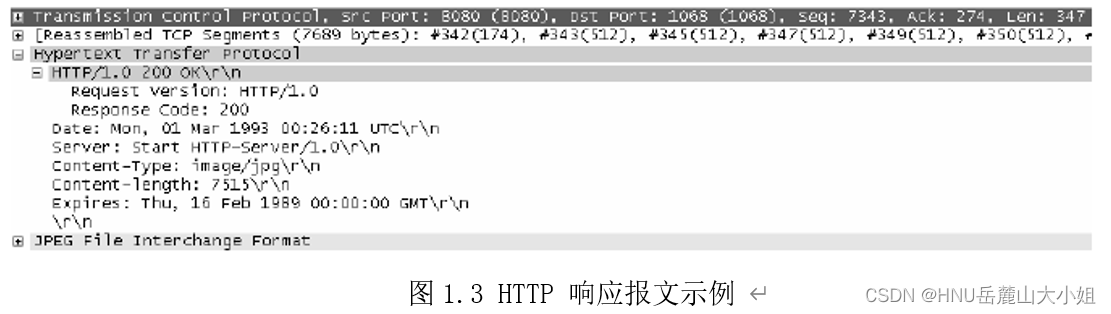
chart 1.2 Sum graph 1.3 Shows the captured HTTP Request and response messages , Combined with the above introduction , Please analyze and experience by yourself .
2. Experimental environment and description
(1) The experiment purpose
stay PC On board access Web page , Intercepted message , analysis HTTP The message format and HTTP
The working process of the agreement .
(2) Experimental equipment and connections
Local laboratory environment , No equipment connection required ;
Be careful : Please visit the that can be connected WWW Site or use IIS Set up local WWW Server to experiment .
(3) Experimental groups
Every four students form a group , Each person has a computer to complete the experiment independently .
3. The experimental steps
step 1: stay PC On board operation Wireshark, Start intercepting messages ;
stay cmd Enter command in ping csee.hnu.edu.cn Check out ip Address 
Select the packet capturing method as wlan
step 2: Access... From a browser Web Interface , Such as http://csee.hnu.edu.cn Open the web page , Wait for the browser's status bar to appear “ complete ” Close web page after message .
By input http && ip.addr == 10.62.102.203 To filter the intercepted message
step 3: Stop intercepting messages , Name the intercepted message http- Save student ID .
Via shortcut key ctrl+s The message can be saved
Analyze the intercepted message , Answer the following questions :
1) Comprehensive analysis of intercepted messages , Check out a few HTTP message ?
There are two kinds of HTTP message .
The first is HTTP Request message for :558 4.300131 It is a request message sent from the client to the server , among Source Of 10.72.33.14 It's client's ip,Destination Of 10.62.102.203 It's server's ip
The second is HTTP Response message of :560 4.310638 It is the response message sent from the server to the client , among Source Of 10.62.102.203 It's server's ip,Destination Of 10.72.33.14 It's client's ip
2) In the interception of HTTP In the message , Choose any one HTTP Request message and corresponding HTTP Reply message , carefully
Analyze their format , Fill in the form 1.1 And table 1.2.
3) Analysis in the intercepted message , The client has several connections to the server ? The server and the client use
Which port numbers have been ?
Three connections have been established : The first connection is 80 and 57448 The connection of , Back to Bad request; The second connection is 80 and 57496 The connection of , Three handshakes ; The third connection is 80 and 57447 The connection of , Is the transmission of information .
The port number used by the server :80
The port number used by the client :57448、57496、57447
4 ) Comprehensive analysis of intercepted messages , understand HTTP The working process of the agreement , Fill in the results in the table 1.3 in .
边栏推荐
- [nailing scenario capability package] video conference (official conference system)
- Presto中Limit算子的处理过程
- Canoe learning notes (2)
- What is DNS (domain name server)? (Powercert animated videos)
- OSI notes sorting
- Illustration tcp/ip - Chapter 3 and 4 notes
- PHP Chinese word segmentation API, Harbin Institute of technology ltpcloud, naturallanguageprocessing, free, best practices!
- 【Proteus仿真】ArduinoUNO+数码管循环显示0~9
- Summary of several methods for FPS calculation
- 05 configuring network parameters
猜你喜欢

【hnu暑学期】数据库系统设计 准备阶段

STM32 self balancing robot project, with code, circuit diagram and other data attached at the end (learning materials and learning group at the end)

Win11录屏数据保存在哪里?Win11录屏数据保存的位置

ASP. Net core uses function switches to control Route Access (Continued) yyds dry inventory
![[nailing scenario capability package] manage the on-the-job / off-the-job situation of employees](/img/ec/c2f342a54ab69d8b834a8a1c8f8a01.jpg)
[nailing scenario capability package] manage the on-the-job / off-the-job situation of employees

HNU数据库系统概论 ODBC

Free your hands and automatically brush Tiktok

QT method of exiting application (exe)

Circular structure and circular keywords

Tcapulusdb Jun · industry news collection (VI)
随机推荐
“No bean named ‘UserController‘ available“
Tcapulusdb Jun · industry news collection (VI)
What is DNS (domain name server)? (Powercert animated videos)
Shell syntax
CANoe. Diva operation guide TP layer test
Jmeter- (IV) regular expression for interface testing
[nail scenario capability package] hospital visitor verification
OSI notes sorting
Apache uses setenvif to identify and release the CDN traffic according to the request header, intercept the DDoS traffic, pay attention to the security issues during CDN deployment, and bypass the CDN
JVM Foundation
HNU计网实验:实验五 网络层与链路层协议分析(PacketTracer)
Simulate ATM system (account opening, login, account query, withdrawal, deposit, transfer, password modification, account cancellation)
Canoe learning notes (4)
The robotframework executes JS commands to move the mouse from X to y
Jmeter- (II) basic interface and common components for interface testing
实验三的各种特效案例
[nailing scenario capability package] ranking of enterprise employees' points
Build the first website with idea
Free your hands and automatically brush Tiktok
Canoe learning notes (1)



