当前位置:网站首页>joda.time获取日期总结
joda.time获取日期总结
2022-06-25 06:32:00 【飞翔的佩奇】
1、获取当前日期和昨天的日期 (格式yyyy-MM-dd)
@Test
public void testJodaTime(){
LocalDate localDate = new LocalDate();
System.out.println(localDate.toString());//获取当前日期 2022-06-23
LocalDate yesterday = localDate.plusDays(-1);// 往前推一天,得到昨天的日期
System.out.println(yesterday.toString());// 2022-06-22
}

2、获取具体年、月、日
@Test
public void testJodaTime(){
DateTime dateTime = new DateTime();
int day = dateTime.getDayOfMonth();
int month = dateTime.getMonthOfYear();
int year = dateTime.getYear();
System.out.println("今天是"+ day +"号");
System.out.println("现在是"+ month +"月");
System.out.println("现在是"+ year +"年");
}

边栏推荐
- Research Report on marketing channel analysis and competitive strategy of China's polycarbonate industry 2022
- Introduction to sap ui5 tools
- Large funds support ecological construction, and Plato farm builds a real meta universe with Dao as its governance
- Curl command – file transfer tool
- Detailed explanation of @jsoninclude annotation in Jackson
- Optimal Parking
- TFTP command – uploading and downloading files
- Ping command – test network connectivity between hosts
- [network security] sharing of experience and ideas of an emergency battle
- Cannot activate inspection type when SAP retail uses transaction code mm41 to create commodity master data?
猜你喜欢

Cve-2022-23131 - bypass SAML SSO authentication

BGP - basic concept

How to deploy locally developed SAP ui5 applications to ABAP servers

cos(a+b)=cosa*cosb-sina*sinb的推导过程
![[speech discrimination] discrimination of speech signals based on MATLAB double threshold method [including Matlab source code 1720]](/img/36/ad86f403b47731670879f01299b416.jpg)
[speech discrimination] discrimination of speech signals based on MATLAB double threshold method [including Matlab source code 1720]

Query process of MySQL secondary index

Self adjustment process of MySQL index tree when adding data

After unplugging the network cable, does the original TCP connection still exist?
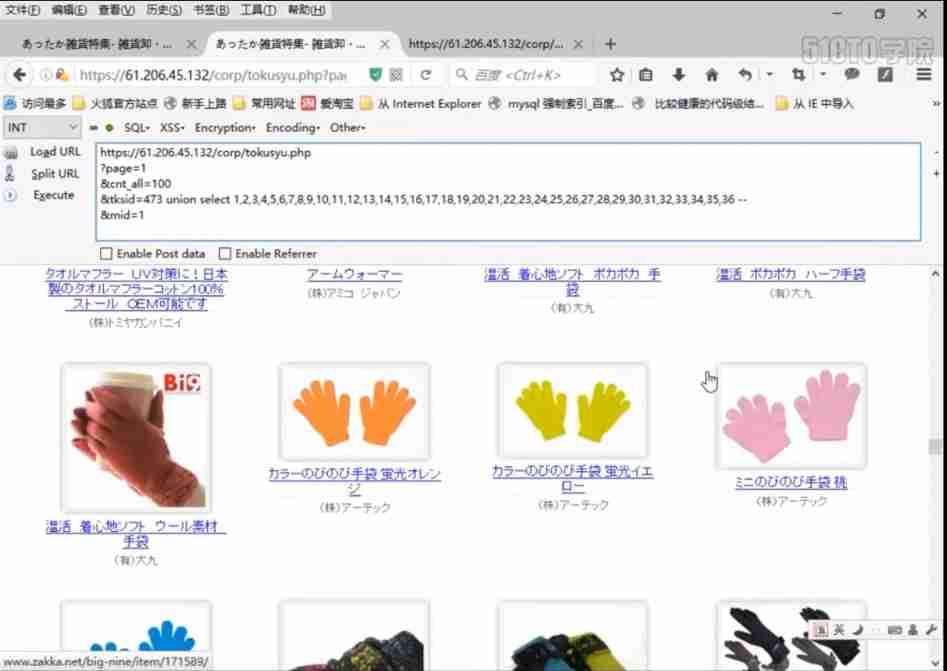
3-7sql injection website instance step 3: attack type and attack strategy

How two hosts in different network segments directly connected communicate
随机推荐
[no title] dream notes 2022-02-20
Arm register (cortex-a), coprocessor and pipeline
Ht8513 single lithium battery power supply with built-in Dynamic Synchronous Boost 5W mono audio power amplifier IC solution
From file system to distributed file system
[network security] sharing of experience and ideas of an emergency battle
Sword finger offer II 095 Longest common subsequence
Arm instructions and others
Understand what MTU is
Large funds support ecological construction, and Plato farm builds a real meta universe with Dao as its governance
cos(a+b)=cosa*cosb-sina*sinb的推导过程
Mount command - file system mount
How to deploy locally developed SAP ui5 applications to ABAP servers
[Suanli network] technological innovation of Suanli Network -- Key Technologies of green and security
Wechat applet simply realizes chat room function
The sum problem
Global and Chinese medical protective clothing market supply and demand research and investment value proposal report 2022-2028
A + B Again
[short time average zero crossing rate] short time average zero crossing rate of speech signal based on MATLAB [including Matlab source code 1721]
BGP - basic concept
Pre knowledge of asynchronous operation