当前位置:网站首页>3-7sql injection website instance step 3: attack type and attack strategy
3-7sql injection website instance step 3: attack type and attack strategy
2022-06-25 06:06:00 【Mountain Rabbit 1】
We have completed the test and discovery of the injection point , Give full play to the injection point , This is SQL Injection essence , To what extent does that need to be played , We need to analyze his characteristics
Let's go on , To learn sql The type of Injection , Depending on the type , What is his attack strategy , This is our article , What to discuss
1.SQL Injection type
Sort by output mechanism :
Blind note : The contents of the output database are not displayed in the web page , Only logical judgments can be made , True or false
Blind injection is that we can't see , We can only guess
An error injection : Make full use of the program 、 Help for database error reporting , Foolishly tell us all the information
In the second part , It was said that a man blew himself up , How to set the library table , Even user names and passwords are exposed to us
Explicit note : Inject SQL The content of the query statement is displayed in the web page .
Is that we can see
Other :email,ftp,samba Such agreement
Of course, this is a vulnerability penetration attack , We are sql This protocol is not involved in injection
Next , We will give you a simple demonstration through the page
2. Blind note
The characteristic is that we can't see , We don't see the results
1. The output is not found or temporarily not found in the web page
2. Confirm that the input variable can perform logical judgment , Only get right or wrong , True or false , Two results
We open a web page of our example

In the test and discovery of the injection point , We already know that this is an injection point , Let's enter a true here ,and true, The result of our execution should be unchanged

We still see two pages , There is no change , If input and false, Let's see

We see that the display in the web page is abnormal , Test is empty , So this is where we haven't found the display bit yet , So here we need to judge whether it is true or false
As long as it is true , The results shown here are invariant , As long as it is false , The resulting page is empty , But the framework is still there , So we use this feature , We can judge whether it is true or false , To judge something
such as , We need to determine the length of the user name , If it is greater than 10 It's true , The display result is normal ,and (select length(user()))>10

So this result , In the second part , How to guess that the user name has been partially touched , This is how to guess users , At the same time, we can also guess what the database is , such as database, Let's look at his length first , Let's see if he is larger than 10,and (select length(database()))>10

We see that he is certainly not larger than 10 Of , Then we are bigger than 8 have a look ,and (select length(database()))>=8

We see greater than or equal to 8 That's right. , That means he is 8、9、10 Between , Let's try 8,and (select length(database()))=8

This is the time , It means that he is equal to 8, We know that the database has 8 Characters , What's the first thing , Let's take one , Guess , for instance , He is equal to z, Let's see if it's right ,and (select left(database(),1))=‘z’

We see that the last letter of the database is z, We use it subtring The way to , Take one from the second , We take a,and (select substring(database(),2,1))=‘a’

We'll find that the second letter is a, It looks like , Let's speculate , This is a blind guess
Similar to this , We can only make logical judgments , You can only get right or wrong , It is characterized by blindness , We can't see , occasionally , We input more results to test , To get out
3. Blind injection difficulty , Sometimes it is necessary to carry out blind injection attack with the help of tools , But it takes longer , Need to have enough patience , Can only be
3. An error injection
Make full use of the information provided by database error reporting and program error reporting , Let database engines and programs , Foolishly , Be obedient and expose all the information you need
select count(*),concat((select (select (SELECT schema_name FROM information_schema.schemata limit 0,1)) as a_col from information_schema.tables limit 0,1),floor(rand(0)*2)) x_col from information_schema.tables group by x_col
That is, the self exploding family background function we learned earlier , This is an example method , Because there are no mistakes reported here , I won't show you a specific example of error reporting injection
4. An illustrative example
Find the location in the web page where the injected information can be displayed , Or replace the information of the injector with the information of the normal program ( Usually , We call the third party superior )
Information from a third party , We need to get through union The way to show
union Need to be at the injection point union,union The result is a few characters , always union down , Always get , How many fields do we need for program injection , Let's judge him ,union select 1,2,3

We see here is empty , Obviously it's not three fields , This requires us to have some patience , Try how many fields there are , Let's enter here , In fact, we make enough input , Of course , We also use tools , Let me show you , How to use tools , To speed up the testing between us , Here we need to constantly test , Test until 36 individual , Let's have a look then , Later, we enter –, Enter two –, For this purpose , Comment out the following , Comment out , Let's take a look at the results ,union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 –
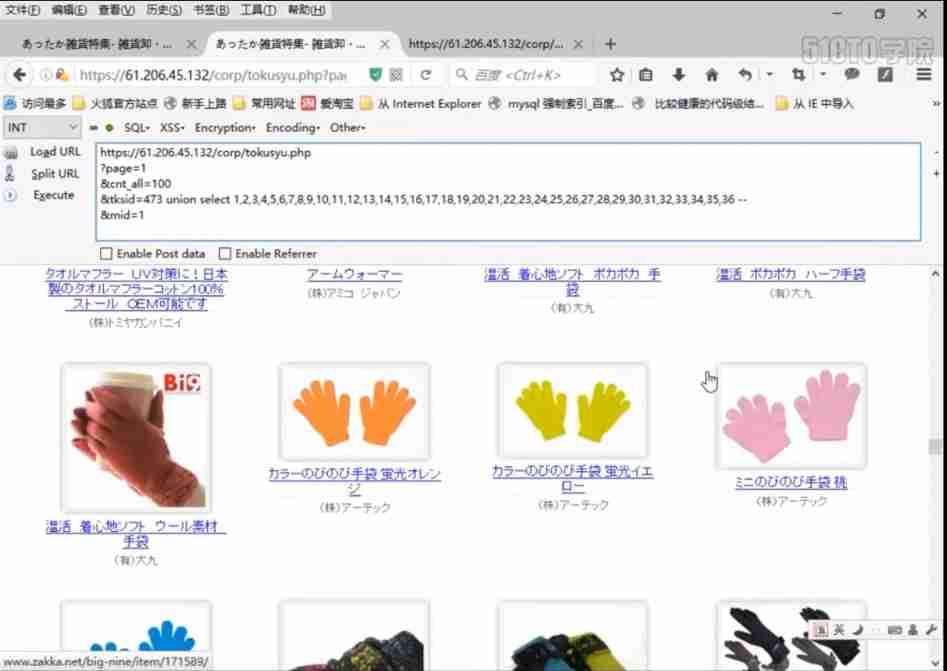
We see that the results have come out , Describe the number of fields processed above , Yes 36 A field ,36 Fields for our goal , The goal is not to get how many characters , Of course, for us , It doesn't mean much
What we need is the logic of the superior , The third party is superior , Just go to the front , First give him an empty set logic ,0=9,0=9, Is equal to empty set logic , Then what is shown is our logic ,
and 0=9 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36 –

I got it at this time , That's when we found out 10 Bit is the upper point of the third party , Next , We will use the 10th place to give full play , This is the task of explicit annotation
therefore , Explicit annotation directly obtains plaintext information , There is no need to guess , Access to sensitive information is very easy and fast , Usually , We sql Inject the most important , Is to find the location of the annotation , This is the upper point of the third party
5. Summary
1.SQL Injection type and characteristics
2. Blind note
3. Misinjection
4. Explicit note
边栏推荐
- What is the use of the subprocess module
- An easy problem
- You can't specify target table for update in from clause error in MySQL
- Try with resource close resource flow
- Day22 send request and parameterization using JMeter
- Interviewer: what is an iterator? What is the relationship between async await and iterators?
- Some common errors and solutions of using SAP ui5 to consume OData services
- How the sap ui5 framework performs single step debugging of batch requests
- SAP ui5 Application Development Tutorial Part 30 - parameter transfer in the routing process of SAP ui5
- How often should you refactor- How often should you refactor?
猜你喜欢
Configuration file ui5 local in SAP ui5 tools Configuration points of yaml

The simplest way to tell you is to hash and not hash
Go quiz: considerations for function naming return value from the go interview question (more than 80% of people answered wrong)
Some common errors and solutions of using SAP ui5 to consume OData services

C simple operation mongodb

MySQL tuning --01--- optimization steps and system performance parameters

The elephant turns around and starts the whole body. Ali pushes Maoxiang not only to Jingdong
SAP Fiori tools and corresponding cli (command line interface)
Technology Review: what is the evolution route of container technology? What imagination space is there in the future?

Soft exam information system project manager_ Management Science (Operations Research) -- senior information system project manager of soft test 033
随机推荐
How SAP ui5 device type detection device API works
PIP connects to Tsinghua source by default
Notes on dashboard & kuboard installation in kubernetes cluster
Three tier architecture experiment
SAP ui5 date type sap ui. model. type. Analysis of date parsing format
SAP ui5 application development tutorial XXIX - Introduction to routing and navigation functions of SAP ui5 trial version
Use of arrays tool class
Distributed solar photovoltaic inverter monitoring
DF command – displays disk space usage
What changes have taken place in the project file after SAP ui5 tools ran the Fiori add deploy config command
Getting started with mongodb
What is the use of the subprocess module
Soft exam information system project manager_ Information system security management - Senior Information System Project Manager of soft test 026
The sum problem
Echo command – output a string or extract the value of a shell variable
What happens when redis runs out of memory
Understanding of process, thread, task queue, event loop, macro task, micro task, execution stack and other concepts in JS
John
Technology inventory: past, present and future of Message Oriented Middleware
How the sap ui5 framework performs single step debugging of batch requests




