当前位置:网站首页>[network security] sharing of experience and ideas of an emergency battle
[network security] sharing of experience and ideas of an emergency battle
2022-06-25 06:14:00 【It old culvert】

Preface
The following data have been desensitized , Chat records will not be screenshot , Just share experiences and ideas , This is a very interesting investigation
Confirm the situation , Gather information
Read the chat records , The customer's network is through EOC Device management terminal , About one or two thousand . Then in the early morning every day, hundreds of machines are out of control , Resume after restart , The address remains the same . Suspected of being attacked , There are a lot of in the inclusion arp package , My colleagues suspect that arp Deceptive attack .
There are four traffic packets , The volume is not small . I asked where I got it , The customer replied : Caught on a port .

Confirm the information
Open the four bags and see what happens , All the good guys are yellow , All are arp package .

With some other bags ,LLDP、DHCPv4,IGMPv3,ssdp,ICMP v6

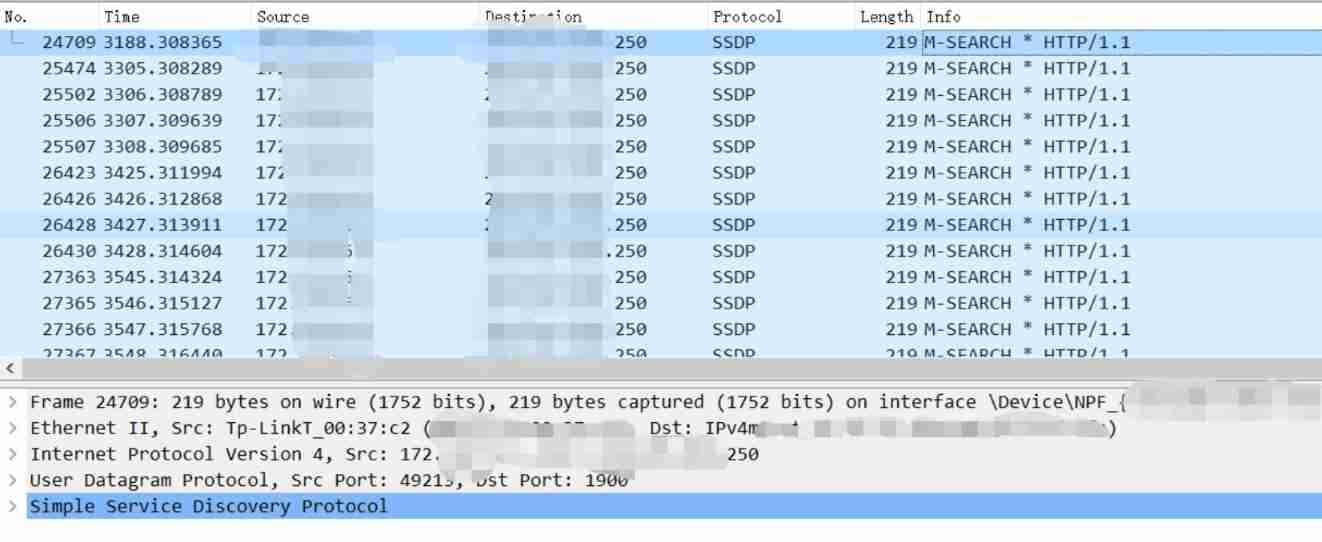
Some strange messages have been found here , Namely dhcp and arp Of . There are some problems with the structure of the two .

Protocol analysis
The investigation is still difficult , Because the customer only gave this thing , In addition, I propose that in order to prevent proliferation hazards, it is not allowed to temporarily cut off the network of the off-line host . Then we can only analyze whether there is a problem with the message structure .
Extract keywords : Capture packets from a certain port , a large number of arp package , Anomalous dhcp package ,netbios agreement ,ssdp Fields in the package .
Network topology analysis
Asked the customer for a topology map , For analysis , The customer gave a very simple hand painting , For the sake of secrecy, I simplified it a little more .

In Topology , You can know , In fact, the network is not complicated , The attacker should not directly take down the core switch or domain controller . And because the network is huge , Thousands of hosts , It is impossible for O & m not to write sniffing function .
DHCP Sniffing can effectively prevent dhcp offer message , To prevent forgery DHCP The purpose of the server to provide false services to the terminal . Once enabled, you need to manually specify the trust port .
Actually , I guess the customer just wants to express how they manage the following host groups .
Exception field analysis
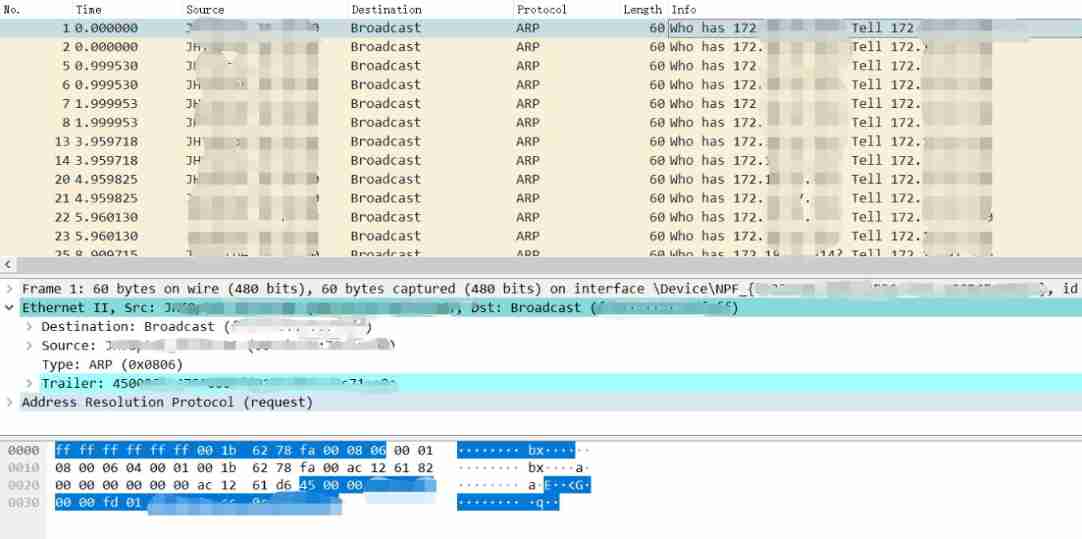
1.arp message
Let's take a look at normal arp The structure of the message :

ARP The structure of the message is simple , There are only request and response packets .
ARP The principle of deception : The attacker sniffs first ARP package , Then steal a host's mac Address , Stream data to the attacker's host .

Let's look at the... In the bag arp message :
There are three main equipment reissues H equipment 、J equipment 、TP equipment .

The only exception is J On the device ARP message , It is very simple , We use the dialogue of the little shark to filter , Filter out all about J equipment ARP message .

The exception is Trailer On this field , Because it's normal ARP The message uses Padding Field instead of all 0 fill .
trailer Field is used when the bytes are excessive , Carrying excess bytes , Non zero filling occurs .
however , After a long time of screening , No obvious signs of attack : Are meaningless bytes . It's not like arp Deceptive attack , Thought no entrance had been broken through .



2.dhcp message
The message with problems in the traffic packet is dhcp discover message , This message is used to request the address , Because it doesn't know dhcp sever So use the full address 0 To request .
Here is a prompt for a moment little endian code , This situation is caused by the disorder of high and low potentials .

So this is actually where , I have told my colleagues , this 7 It's a network problem , As for what the network problem is, I can't say it for a while . Next, I will analyze what I am not sure 3 Where is Cheng .
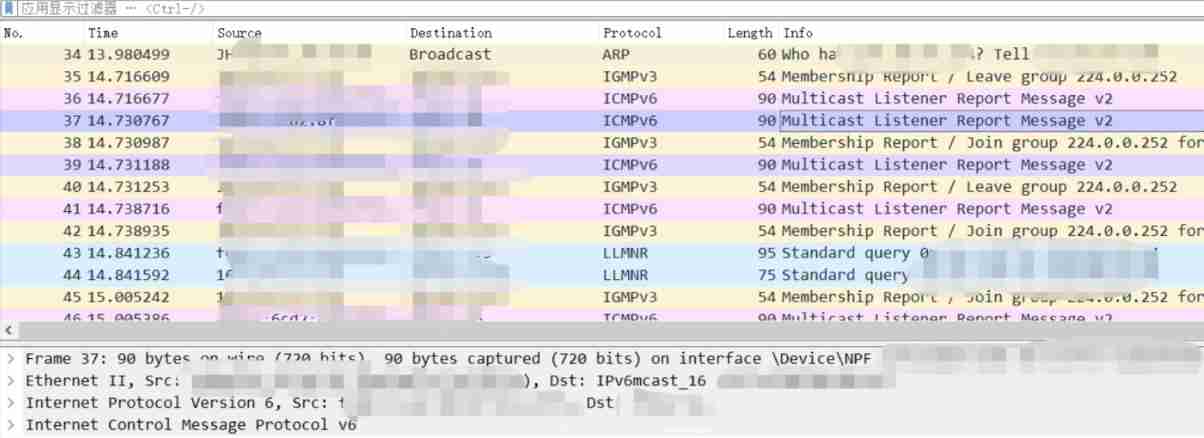
3. Messages of other protocols
It was also later , I'm going to write a report , Then the customer 1 A few more bags came at halfpastten , It is a package captured in a short time after restart and recovery . I got up and analyzed again .
Take a look at other findings , These findings were bounced back by the customer , It's OK .
stay SSDP In the message , Found fields that seem to be connected to the outside :

Then the host name and the domain controller are found in other messages , Spicy is frightening me , Domain control is k It fell off ???
Customer : That's a machine for grabbing bags , Don't worry .



Conclusion
This is not really a problem of cyber attacks , The above is what I wrote after sorting out my thoughts , In case of emergency, I think with the idea of network security , In fact, from the perspective of network workers , The answer is obvious .
First, let's review the topology :

classical OLT Building networks , Drag it down ONU Equipment management .ONU The device is an optical network unit device , Generally, the installation includes Optical receiver 、 Uplink optical transmitter 、 Multiple The bridge The device monitored by the amplifier network is called an optical node .PON Use a single fiber to connect to OLT, then OLT Connect to ONU.
And then look at it DHCP message , There is a short time little endian code ; At the same time ARP In the message , Meaningless extra byte padding occurs .
There's only one conclusion ONU There's something wrong with the equipment , The optical fiber or optical module is damaged , Cause data transfer failure . From the above analysis ,dhcp discover The package is unresponsive ,arp The package construct is also complete . Appear many times at the same time igmp The application message of adding and leaving groups is not responded . The conclusion is : Because there is a problem with optical signal transmission , This led to the disconnection of one of the following mainframes , Not a cyber attack .
边栏推荐
- Digitalization, transformation?
- Summary of 6 common methods of visual deep learning model architecture
- Getting started with Silverlight development 1
- Various errors and solutions encountered when deploying SAP ui5 application to ABAP server with SAP Fiori tools
- Ifconfig command – displays or sets network devices
- Pat 1045 quick sort
- Click to send text messages without response is a common problem for many users in building the elegant grass Dragonfly Q system - solve the problem of clicking to send text messages without response
- BGP - basic concept
- Research Report on marketing channel analysis and competitive strategy of China's polycarbonate industry 2022
- Global and Chinese medical protective clothing market supply and demand research and investment value proposal report 2022-2028
猜你喜欢
![[Suanli network] problems and challenges faced by the development of Suanli network](/img/90/1d537de057113e2b4754e76746f256.jpg)
[Suanli network] problems and challenges faced by the development of Suanli network

RT thread i/o device model and layering
The locally developed SAP ui5 application is deployed to the ABAP server to perform error analysis
![[data visualization application] draw spatial map (with R language code)](/img/2d/04e5015573d10bdd6325ae497bfeb3.jpg)
[data visualization application] draw spatial map (with R language code)
Mongodb delete data
MySQL transaction learning notes (I) first encounter

MySQL tuning --01--- optimization steps and system performance parameters

Soft exam information system project manager_ Management Science (Operations Research) -- senior information system project manager of soft test 033
The e-book "action guide for large organizations to further promote zero code application platform" was officially released!

Create a complete binary tree in array order
随机推荐
[kicad image] download and installation
Mongodb basic concept learning - Documentation
Invalid bound statement (not found)
How the sap ui5 framework performs single step debugging of batch requests
Configuration file ui5 local in SAP ui5 tools Configuration points of yaml
Soft exam information system project manager_ Management Science (Operations Research) 2--- senior information system project manager of soft test 034
DF command – displays disk space usage
Laravel8 fill data
What happens when redis runs out of memory
Noi Mathematics: Dirichlet convolution
The elephant turns around and starts the whole body. Ali pushes Maoxiang not only to Jingdong
Websocket in the promotion of vegetable farmers
Research Report on brand strategic management and marketing trends in the global and Chinese preserved fruit market 2022
Echo command – output a string or extract the value of a shell variable
Introduction to sap ui5 tools
Leetcode sword finger offer question brushing - day 27
Some common errors and solutions of using SAP ui5 to consume OData services
Location object
Soft exam information system project manager_ Management Science (Operations Research) -- senior information system project manager of soft test 033
Tencent and China Mobile continued to buy back with large sums of money, and the leading Hong Kong stocks "led" the market to rebound?


