当前位置:网站首页>Penetration test basis | attached test points and test scenarios
Penetration test basis | attached test points and test scenarios
2022-06-23 05:17:00 【Lao Xiao of Buddhism】
List of articles
Penetration testing is the process of identifying security vulnerabilities in applications by evaluating systems or networks with various malicious technologies . In the process , Exploit system vulnerabilities through authorized mock attacks .
The purpose of this test is to protect important data from external personnel ( Such as hackers ) The attack of , These hackers can access the system without authorization . Once the vulnerability is identified , It will be used to use the system to gain access to sensitive information .
Penetration testing is also called penetration testing , Penetration testers are also known as ethical hackers .
What is penetration testing ?
We can find out the computer system through penetration test ,Web Application or network vulnerabilities .
The penetration test will determine whether the existing defense measures adopted on the system are strong enough , To prevent any security vulnerabilities . The penetration test report also puts forward the countermeasures that can be taken , To reduce the risk that the system is invaded by hackers .
Causes of the vulnerability
- Design and development errors : Hardware and software design may be defective . These errors may expose your business critical data .
- Improper system configuration : This is another reason for the vulnerability . If the system is not configured properly , Then it may introduce loopholes , Attackers can enter the system and steal information through these vulnerabilities .
- Human error : Human factors , For example, improper document handling , Leave the document unattended , Coding errors , Internal threats , Sharing passwords through phishing sites may lead to security vulnerabilities .
- connectivity : If the system is connected to an insecure network ( Open connection ), Then hackers can attack it .
- complexity : Security vulnerabilities rise in proportion to system complexity . The more functions the system has , The more likely the system is to be attacked .
- password : Passwords are used to prevent unauthorized access . They should be strong enough , No one can guess your password . Passwords should not be shared with anyone at all costs , Passwords should be changed periodically . Despite these instructions , But sometimes people reveal their passwords to others , Write it down , And keep the simple password you can guess .
- User input : You must have heard of SQL Inject , Buffer overflow, etc . The data received electronically by these methods can be used to attack the receiving system .
- management : Safety management is difficult and expensive . Sometimes , The organization lacks proper risk management , Therefore, a vulnerability is induced in the system .
- Lack of staff training : This can lead to human error and other vulnerabilities .
- signal communication : The mobile network , Internet , Telephone and other channels have opened up the scope of security theft .
Penetration testing tools and companies
Criteria for selecting the best penetration tool :
- It should be easy to deploy 、 Configure and use .
- It should be easy to scan your system .
- It should classify vulnerabilities according to the severity that needs to be fixed immediately .
- It should be able to automatically verify vulnerabilities .
- It should revalidate previously discovered vulnerabilities .
- It should generate detailed vulnerability reports and logs .
Once you know what tests you need to perform , You can train your internal testing resources , Or hire an expert consultant to complete the infiltration task for you .
Recommended penetration testing tools
(1) Acunetix
Acunetix WVS It provides a series of amazing functions for security professionals and software engineers , Simple use , Direct and very powerful software packages .
Official website :Automate Penetration Testing For Your Web Application | Acunetix

(2) The invaders
Intruder Is a powerful vulnerability scanner , Network security vulnerabilities in digital assets can be found , Explain risks and help remedy violations before they occur . It is the perfect tool to help automate penetration testing .
Official website :Intruder | An Effortless Vulnerability Scanner
The main features :
- Throughout IT More than... In the infrastructure 9,000 Automatic check .
- Infrastructure and Web Layer inspection , for example SQL Injection and cross site scripting .
- Automatically scan the system when new threats are found .
- Multiple integrations :AWS,Azure,Google Cloud,API,Jira,Teams etc. .
- Intruders provide their Pro Planned 30 Days free trial .
(3) Astra · Panst
Astra Pentest Is a security testing solution , Compatible with any business from all walks of life . They have an intelligent vulnerability scanner and a team of experienced and highly driven penetration testers , Ensure that each vulnerability is detected , And suggest the most effective repair method .
Official website :Astra Pentest
The main features :
- Interactive dashboard
- adopt CI/CD Integrated for continuous scanning
- Detect business logic errors 、 Price manipulation and privilege escalation loopholes .
- adopt Astra The login logger extension for scan after the login page
- Scan line by line Web application (PWA) And single page apps
- Real time compliance reporting
- Zero false alarm
Use the intelligent scanner to find the loopholes in front of hackers , And pass CXO A developer friendly dashboard manages your entire security . Choose a plan according to your needs .
Recommended penetration testing company
(1) software security
Software Secured help SaaS The company's development team through penetration testing as a service (PTaaS) Deliver security software . Their services provide more frequent testing for teams that roll out code more frequently , And proved to be discovered within a year bug More than twice the number of one-time penetration tests .
The main features :
- Combine manual and automated testing with regular team rotation , To provide a new perspective .
- Comprehensive testing with major releases several times a year .
- Continuous reporting and unlimited retesting of new features and patches throughout the year .
- Continuous access to safety expertise and advisory services .
- Including advanced threat modeling 、 Business logic testing and infrastructure testing .
Other free tools :
Business services :
Why choose penetration testing ?
You must have heard of 2017 year 5 At the beginning of the month WannaCry Blackmail software attacks . It has locked the world in more than 20 Ten thousand computers , And ask for ransom payment from bitcoin cryptocurrency . This attack has affected many large organizations around the world .
With such a large and dangerous cyber attack happening these days , It is inevitable to conduct regular penetration tests to protect information systems from security vulnerabilities .
Penetration testing is mainly used for :
- When transferring financial or critical data between different systems or over the network , It must be protected .
- Many customers require penetration testing as part of the software release cycle .
- Protect user data .
- Find security vulnerabilities in your application .
- Discover vulnerabilities in the system .
- Assess the impact of a successful attack on the business .
- Meet information security compliance in the organization .
- Implement effective security policies within the organization .
Any organization needs to identify security issues in its internal networks and computers . Use this information , Organizations can plan to defend against any hacker attack attempt . User privacy and data security are the biggest problems today .
Imagine , If any hacker tries to get something like Facebook User details of such social networking sites . Due to the small loopholes left in the software system , The organization may face legal issues . therefore , Before doing any business with third party customers , Large organizations are looking for PCI( Payment card industry ) Compliance certification .
What should a penetration test test test ?
- Software ( operating system 、 service 、 Applications )
- Hardware
- The Internet
- The process
- End user behavior
#1) Social engineering testing : In this test , Try to get someone to divulge sensitive information , Such as password , Key business data, etc . These tests are mainly done by telephone or Internet , It is for certain help desks , Staff and process .
Human error is the main cause of security vulnerabilities . All personnel shall comply with safety standards and policies , To avoid attempts to infiltrate social engineering . Examples of these standards include not mentioning any sensitive information in email or telephone communications . Safety audits can be conducted to identify and correct process deficiencies .
#2)Web Application testing : Using software methods , It can verify whether the application is exposed to security vulnerabilities . It checks for... In the target environment Web Security vulnerabilities in applications and software programs .
#3) Physical penetration testing : Adopt powerful physical security methods to protect sensitive data . This is usually used for military and government facilities . All physical network devices and access points have been tested , In case of any security vulnerability . This test is not very relevant to the scope of software testing .
#4) Network service test : This is one of the most commonly performed penetration tests , The opening in the network is identified by which entry in the system on the network , To check what kind of vulnerability exists . This can be done locally or remotely .
#5) Client side test : It aims to search and exploit vulnerabilities in client software programs .
#6) Remote dialing : It searches the environment for modems , And try to login to the system connected through these modems through password guessing or brute force cracking .
#7) Wireless security test : It finds openness , Unauthorized and less secure Hotspots or Wi-Fi The Internet , And connect through them .
What we see above 7 A category is a way to classify the types of penetration tests .
We can also organize the types of penetration tests into three parts , As shown below :

Let's discuss these test methods one by one :
- Black box penetration test : In this way , The tester evaluates the target system without knowing its details , Network or process . They just have a very high level of input , for example URL Or company name , They use these inputs to penetrate the target environment . No code is checked in this method .
- White box penetration test : In this way , The tester is equipped with complete details about the target environment - System , The Internet , operating system ,IP Address , Source code , Architecture, etc . It examines the code and finds design and development errors . It is a simulation of an internal security attack .
- Ash box penetration test : In this way , Testers have limited detail about the target environment . It is a simulation of an external security attack .
Penetration testing technology
- Manual penetration test
- Use automated penetration testing tools .
- A combination of manual and automated processes .
The third process, which is more common, is to identify various vulnerabilities .
Manual penetration test :
It is difficult to find all the vulnerabilities using automated tools . Some vulnerabilities can only be identified by manual scanning . Penetration testers can perform better attacks on applications based on their skills and knowledge of the penetrated system .
Methods like social engineering can be done by humans . Manual inspection includes design 、 Business logic and code validation .
Penetration testing process :
Let's discuss the actual process followed by the testing agency or penetration tester . Identifying vulnerabilities in the system is the first important step in this process . Take corrective action for this vulnerability , And repeat the same penetration test , Until the system is negative for all these tests .
We can classify this process in the following ways :

#1) data collection : Use includes Google Search and other methods to obtain the target system data . People can also use web page source code analysis technology to obtain information about the system , More information about software and plug-in versions .
There are many free tools and services on the market , Can provide you with the database or table name , Database version , Software version , The hardware used and various third-party plug-ins used in the target system .
#2) Vulnerability assessment : According to the data collected in the first step , Security vulnerabilities of the target system can be found . This helps penetration testers launch attacks using identified entry points in the system .
#3) The actual use of : This is a key step . It requires special skills and techniques to attack the target system . Experienced penetration testers can use their skills to attack the system .
#4) Analysis and report preparation results : After completing the penetration test , Prepare detailed reports to take corrective actions . These reports list all identified vulnerabilities and recommended corrective actions . You can customize the vulnerability report format according to your organization's needs (HTML、XML、MS Word or PDF).
Penetration test example test case ( Test point / Test scenarios )
please remember , This is not a functional test . stay Pentest in , Your goal is to find security holes in the system .
Here are some common test cases , Not necessarily for all applications .
- Check Web Whether the application can identify spam attacks on contact forms used on the website .
- proxy server – Check whether the agent device monitors network traffic . Proxy servers make it difficult for hackers to obtain internal details of the network , So as to protect the system from external attacks .
- Spam filter – Verify that incoming and outgoing e-mail traffic is filtered , And whether unsolicited emails are blocked .
- Many email clients come with built-in spam filters , It needs to be configured according to your needs . These configuration rules can be applied to email headers 、 Subject or body .
- A firewall – Ensure that the entire network or computer is protected by a firewall . A firewall can be software or hardware that blocks unauthorized access to a system . Firewalls prevent data from being sent outside the network without your permission .
- Try to leverage all servers 、 Desktop system 、 Printers and network devices .
- Verify that all user names and passwords are encrypted and securely connected ( Such as https) transmission .
- Validation is stored in Website Cookie Information in . It should not be in a readable format .
- Verify previously discovered vulnerabilities , To see if the fix is working .
- Verify that there are no open ports on the network .
- Verify all telephone devices .
- verification WiFi Network security .
- Verify that all HTTP Method . It should not be in Web Enable... On the server PUT and Delete Method .
- Verify that the password meets the required standards . Password length should be at least 8 Characters , At least one number and one special character .
- User name should not be “ Administrators ” or “ Administrators ”.
- The application login page should be locked when several login attempts fail .
- The error message should be general information , Specific error details should not be mentioned , Such as “ Invalid user name ” or “ Invalid password ”.
- Verify special characters 、HTML Whether tags and scripts are properly handled as input values .
- Internal system details should not be displayed in any error or alarm messages .
- In the event of a web page crash , A custom error message should be displayed to the end user .
- Verify registry key usage . Sensitive information should not be retained in the registry .
- Before uploading files to the server , All files must be scanned .
- With the Web When different internal modules of the application communicate , Sensitive data should not be passed to URL.
- There should be no hard coded user name or password in the system .
- Verify that all have long input strings ( With and without spaces ) The input field of .
- Verify that the reset password function is secure .
- Verify that the application is used for SQL Inject .
- Validation span Site script Applications for .
- Important input validation should be done on the server side , Not on the client side JavaScript Check .
- Key resources in the system shall only be used by authorized personnel and services .
- All access logs should be maintained with appropriate access rights .
- Verify that the user session ends at logoff .
- Verify that directory browsing is disabled on the server .
- Verify that all application and database versions are up to date .
- verification URL Operate to check Web Does the application not display any unwanted information .
- Verify memory leaks and buffer overflows .
- Verify that incoming network traffic is scanned for Trojan horse attacks .
- Verify that the system is safe from violent attacks - A trial and error method for finding sensitive information such as passwords .
- Verify that the system or network is protected , Free from DoS( Denial of service ) attack . Hackers can target a network or a single computer with continuous requests , Because the resources on the target system are overloaded , This leads to a denial of service for legitimate requests .
- Verify that the application exists HTML Script injection attack .
- verification COM and ActiveX attack .
- Verify whether there are spoofing attacks . Deception can be of many types - IP Address spoofing , E-mail ID cheating ,
- ARP cheating 、 Referral source website cheating 、 Caller ID spoofing 、 File sharing network poisoning 、GPS cheating .
- Check for uncontrolled format string attacks , This is a security attack , May cause the application to crash or execute harmful scripts on it .
- verification XML Injection attack – Used to change the expected logic of the application .
- Verify normalization attacks .
- Verify that the error page displays any information that helps hackers enter the system .
- Verify that there are any critical data ( Such as password ) Stored in confidential files on the system .
- Verify that the data returned by the application exceeds the required data .
边栏推荐
- UnityShader入门精要——Unity中的渲染优化技术(四)
- Economic development is driven by new technology
- Cookie-Session讲解
- JDBC call stored procedure, MySQL trigger
- 新晋职场人的 技术进击?之旅
- UI automation positioning edge -xpath actual combat
- Jetpack Compose 从开门到入门之 MenuBar桌面菜单(Desktop Menu)
- 使用teqcplot对teqc 质量分析结果进行可视化展示
- JSP入门级笔记
- Mongodb sharding principle
猜你喜欢

微信小程序:微信也可以发闪照了闪照制作生成微信小程序源码下载,自定义闪照时间
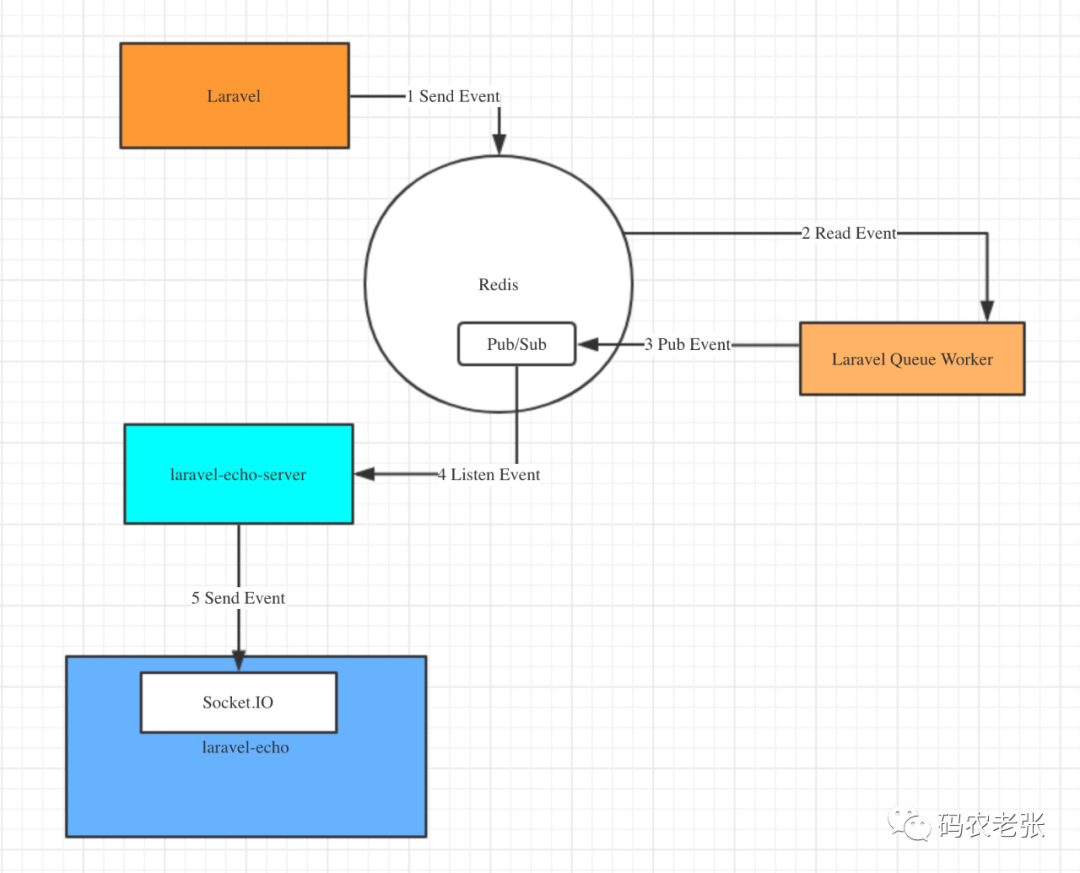
【Laravel系列7.8】广播系统
VMware network connection error unit network service not found

Unity中,如何在【编辑器】和【运行时】状态下读写一个ScriptableObject对象
Hcip reissue experiment

The propeller framework v2.3 releases the highly reusable operator library Phi! Restructure development paradigm to reduce cost and increase efficiency

飞桨框架v2.3发布高可复用算子库PHI!重构开发范式,降本增效

掌握 Shell,一篇就够了!

BGP实验

HCIP第五次作业
随机推荐
[C language] keyword
SwiftUI 2.0 课程笔记 Chapter 4
teqc进行GNSS数据质量分析时生成的s文件介绍
HCIP 交换机实验
Small problems in the spoole framework for TCP communication in PHP
直接插入排序——【常见排序法(1/8)】
三层架构实验
BGP experiment
Jetpack Compose 从开门到入门之 MenuBar桌面菜单(Desktop Menu)
图片降噪DeNoise AI
Hcip fifth operation
OSPF分流实验
[laravel series 7.8] broadcasting system
Zygote进程
Course design C for freshmen -- clothing management system
insert into... Where not exists insert to avoid repeated use
滑块视图的实现
Swiftui 2.0 course notes Chapter 4
JSP入门级笔记
MVC三层架构



