当前位置:网站首页>Intra domain information collection for intranet penetration
Intra domain information collection for intranet penetration
2022-06-25 20:19:00 【Bypass--】
When you get a computer in the domain Windows Server permissions , We need to collect as much information about the domain as we can , The more domain information is collected , The higher the success rate of domain control .
01、 Determine whether there is a domain
(1) Generally, we are collecting local information , Inquire about IP Network or system information , It's easy to find domain control .
ipconfig /all command 
systeminfo command 
(2) View the current login domain and domain users
net config workstation
(3) All domain servers will act as time servers at the same time , So use the following command to determine the primary domain .
function net time /domain After the order , There are generally three situations as follows :
1. Domain of existence , But the current user is not a domain user , The prompt indicates that the permission is not enough
C:\Users>bypass>net time /domain
A system error occurred 5
Access denied .
2. Domain of existence , And the current user is a domain user
C:\Users\Administrator>net time /domain
\\dc.test.com The current time of is 2020/10/23 21:18:37
Command completed successfully .
3. The current network environment is workgroup , No domain exists
C:\Users\Administrator>net time /domain
Domain not found WORKGROUP Domain controller for .02、 Find a domain controller
(1) Generally speaking , Domain control server IP The address is DNS Server address , find DNS The server address can locate the domain controller .
nslookup/ping domain name , Resolve to domain control server IP Address 
(2) View the machine name of the domain controller
nltest /DCLIST:test.com
(3) View domain controllers
net group "Domain Controllers" /domain
3、 Get users and administrators in the domain
(1) Query the list of all user groups in the domain
net group /domain
(2) Query the list of domain Administrators
net group "Domain Admins" /domain
(3) Get a list of all domain users
net user /domain
(4) Get the specified domain user bypass Details of
net user bypass /domain
(5) Query the users of the built-in local administrator group in the domain
net localgroup administrators /domain
04、 Locate the domain administrator
If we can find which servers the domain administrator logged in to , You can attack these servers and try to take advantage of , To gain domain administrator privileges .
(1)PowerView
PowerView.ps1 Integrated into the PowerSploit In the frame , The script relies entirely on PowerShell and WMI Inquire about .
Domain user permissions , The information that can be obtained is related to user rights , Local administrator user cannot query .
Download address :
https://github.com/PowerShellEmpire/PowerToolsGet the login location information of all domain Administrators :
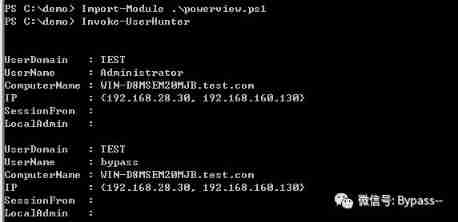
(2)PsLoggedOn
PsLoggedOn yes PSTools A small program in the toolkit , It shows the users who log in locally and the users who log in through the resources of the local computer or the remote computer .
Domain user permissions , The local administrator cannot query .
Download address :
https://docs.microsoft.com/en-us/sysinternals/downloads/psloggedonView the currently logged in user of domain controller :

(3)PVEFindADUser
Download address :
https://github.com/chrisdee/Tools/tree/master/AD/ADFindUsersLoggedOnUse domain users to perform , View the logged in users of all computers in the domain :

05、 Find domain management process
Compare with local processes and process users through the list of domain administrators , You can find the process run by the domain administrator .
net group "domain admins" /domain // Get the list of domain Administrators
tasklist /v // List all local processes and process users 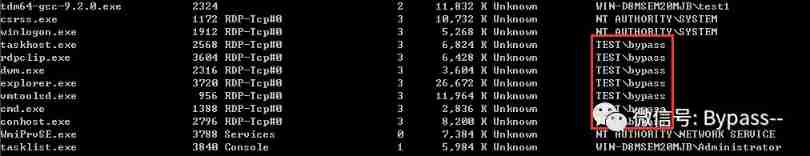
边栏推荐
- SQL statement select summary
- 5 minutes to learn how to install MySQL
- Leetcode daily question - 27 Remove element (simple)
- 2.16([Usaco2005 Nov]Ant Counting)
- TypeError: __ init__ () takes 1 positional argument but 5 were given
- JS forest leaf node non recursive depth first postorder traversal
- Redis practice: smart use of data types to achieve 100 million level data statistics
- Expand and check the specified node when loading ztree
- JS canvas drawing an arrow with two hearts
- Measurement index SSMI
猜你喜欢

Wechat applet cloud function does not have dependency option installed

Li-rads lesion classification reading notes

Verification code native JS canvas

Log in to Huawei game with a minor account, and pop up anti addiction prompt after startup

Interface automation -md5 password encryption

E-commerce project environment construction

Pcl+vs2019+opencv environment configuration
Determine whether it is a web page opened on wechat

Bindgetuserinfo will not pop up
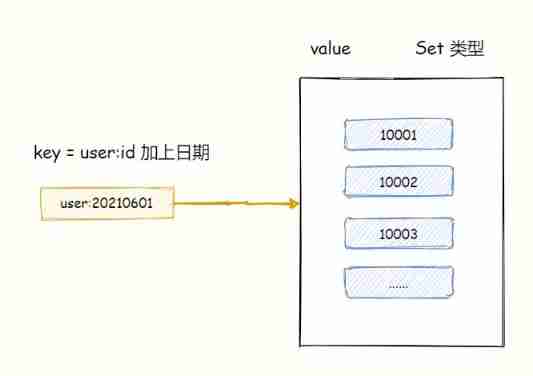
Redis practice: smart use of data types to achieve 100 million level data statistics
随机推荐
Is it safe to open a new bond? Is low commission reliable
Appearance of object attributes
Browser performance optimization (19)
2.15(Multiple of 3 Or 5)
Profile path and name
Pat b1054 average (20 points)
PAT B1096
Connect the local browser to the laboratory server through mobaxterm
2.16([Usaco2005 Nov]Ant Counting)
[harmonyos] [arkui] how can Hongmeng ETS call pa
NMS reduction box
Web container basic configuration
Pcl+vs2019 configuration and some source code test cases and demos
JQ implements tab switching
Huawei fast application access advertising service development guide
2.6 finding the sum of the first n terms of factorial sequence
String since I can perform performance tuning, I can call an expert directly
Curtain down and departure
5 minutes to learn how to install MySQL
Mqtt+ardunio+esp8266 development (excluding mqtt server deployment)