当前位置:网站首页>About information disclosure and defense
About information disclosure and defense
2022-06-23 05:25:00 【Johnny, me】
Information disclosure
- Strictly speaking, information disclosure is not a security vulnerability , It is the general name of a kind of phenomenon
- Whether it's web Both developers and users should pay attention to information disclosure
- Specific information breaches include
- Disclose sensitive information of the system ( Server configuration , Password etc. )
- Divulge user sensitive information ( The user registers at a station , Information is sold or stolen )
- Divulging user passwords ( Obvious security vulnerabilities )
- Ways of information disclosure
- Error message out of control ( Error messages are exposed because they are not handled well )
- SQL Inject ( The website exposes a lot of database information under unexpected circumstances )
- Improper horizontal authority control ( What users can see , Whether users with the same rights have overstepped their authority )
- XSS/CSRF( Direct disclosure of information )
- …
- Information leakage will lead to the rise of social engineering
social engineering
- Social engineering is a rigorous science
- But in the increasingly complex security environment, social engineering tends to social engineering fraud
- for instance , It will dig out your information through some channels
- nickname
- real name
- mailbox
- cell-phone number
- ID number
- password
- …
- This information , More and more can be done after a variety of combinations and information mining
- For example, get your Alipay password through the above information , Because it may need a cell phone number , ID number and mobile phone number
- When there is more and more information , The image of this person can be established in a three-dimensional way
- At this time, the secret protection is invalid , You can pretend to be yourself
- This is a very terrible thing
- Your identity is determined by the information you have
- Others have your information , Can pretend to be your identity
- Then you can use your identity to do bad things
- So information leakage can cause serious consequences
- web Development must try its best to ensure that the user's data is not leaked
Common cases of information leakage
- telecommunication fraud
- Camouflage public security law
- QQ Video borrowing
- Wechat disguises friends
OAuth thought
- These hazards and cases startle us
- We can learn from some mature schemes in the industry :OAuth
- OAuth Participants involving three parties
- QQ: Master the user information, password and other information
- Broken website : There are safety risks
- user
- OAuth Under the authorization of the user , from QQ Where to get information
- This can be very good defense QQ Data leakage
- The specific process is as follows
- The user requests a third party to log in on the broken website
- The broken website redirects to QQ
- The user is in QQ Enter the password on the website to confirm the right to log in
- After successful login , from QQ The website jumps back to the broken website
- Broken websites will request accessToken( User credentials )
- QQ return accessToken
- Broken website through accessToken towards QQ Get user information
- Among them the accessToken You can only obtain the user data when the user is authorized and cannot obtain other user information
- The key idea is
- All actions are authorized by the user
- Authorization does not disclose sensitive information
- Authorization will expire
- We can also use this idea to prevent the leakage of user information when developing our website
utilize OAuth Protect user data
- There are also three party objects
- Sensitive information : Identity information, etc
- Business : Publish articles and other functions
- user
- After this split , Our website will be like this
- The user logs in to the sensitive data party through the account and password
- Login successful , Sensitive information is distributed to users token
- At this time, the user brings the ticket token Request business
- User data is involved in business processing , For example, send email notification, etc
- The bill brought by the user is used for business operation
- Exchange sensitive data for user information through bills
- Business continues
- The characteristics of this process
- The user is authorized to read the data
- Unauthorized data cannot be read
- Batch data acquisition is not allowed
- The data interface can be used for risk control audit
- Do you know whose business it is
- What did you check
- When did you query it
- Through this process, users can effectively prevent unlimited leakage
- At this time, the data of a single user may be leaked
- Through the audit process, the problem of batch data leakage is effectively prevented
- The architecture will be a little complicated , Mainly to build sensitive data objects
- We can change the sensitive information into another nice name : User center
- If such a user center layer is built , You can avoid sql Attacks brought by injection
- because sql Not in the business , Just call the interface to the user center to retrieve user data , No, sql Unable to inject
- Even if it is injected from other businesses , The information is no longer here , Unable to obtain user sensitive data
- If some dishonest employees in the enterprise want to sell user data , You can't query user data without a ticket
- Sensitive information ( User center ) Only oneortwo employees to maintain , Do not allow a wide range of employees to access , Relatively safer
边栏推荐
- Seata四大模式之XA模式详解及代码实现
- Zygote process
- Baidu PaddlePaddle's "universal gravitation" first stop in 2022 landed in Suzhou, comprehensively launching the SME empowerment plan
- The propeller framework v2.3 releases the highly reusable operator library Phi! Restructure development paradigm to reduce cost and increase efficiency
- 数据库连接异常:create connection error, url: jdbc:mysql://ip/数据库名, errorCode 0, state 08S01问题处理
- Ams:startactivity desktop launch application
- 李宏毅《机器学习》丨5. Tips for neural network design(神经网络设计技巧)
- 弱者易怒如虎,强者平静如水,真正厉害的人早已戒掉了情绪
- Drama asking Huamen restaurant Weng
- 【Leetcode】最长递增子序列问题及应用
猜你喜欢

【微服务|Nacos】Nacos实现多环境和多租户的数据隔离

The tiobe programming language ranking is an indicator of the popular trend of programming languages
VMware network connection error unit network service not found

Event log keyword: eventlogtags logtags

The propeller framework v2.3 releases the highly reusable operator library Phi! Restructure development paradigm to reduce cost and increase efficiency

(IntelliJ)插件一 Background Image Plus

Penetration test basis | attached test points and test scenarios
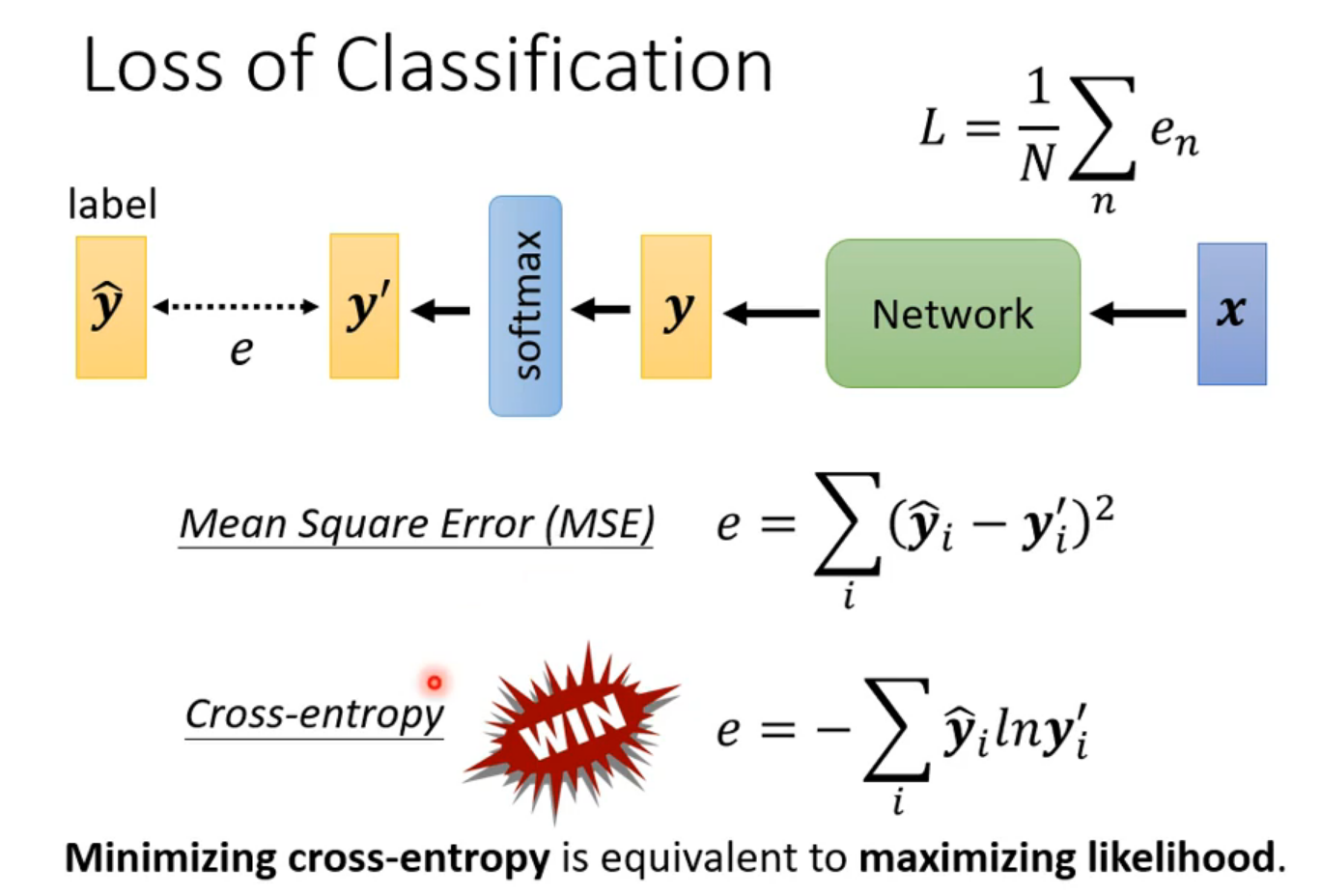
李宏毅《机器学习》丨5. Tips for neural network design(神经网络设计技巧)

Seata四大模式之XA模式详解及代码实现

架构师之路,从「存储选型」起步
随机推荐
九九乘法表.bat
JVM原理之完整的一次GC流程
渗透测试基础 | 附带测试点、测试场景
Missing essential plugin
Drag and drop拖放框架
Spark 离线开发框架设计与实现
Image noise reduction denoise AI
Jetpack compose menubar Desktop Menu from door opening to entry
(IntelliJ) plug in background image plus
Error related to synchronizing domestic AOSP code
H5 适配全面屏
H5 adaptive full screen
MySQL自定义序列数的实现
Mysql入门学习(三)之视图
618 how to break through the siege? Haier Zhijia: do a good job in digitalization of users
GO语言-包的使用
pygame音乐相关的功能实现
[laravel series 7.8] broadcasting system
Open source ecology 𞓜 super practical open source license basic knowledge literacy post (Part 2)
Missing essential plugin