当前位置:网站首页>[mrctf2020] thousand layer routine
[mrctf2020] thousand layer routine
2022-06-24 07:24:00 【[mzq]】
[MRCTF2020] Thousand layer routine
Title address : https://buuoj.cn/challenges#[MRCTF2020]%E5%8D%83%E5%B1%82%E5%A5%97%E8%B7%AF
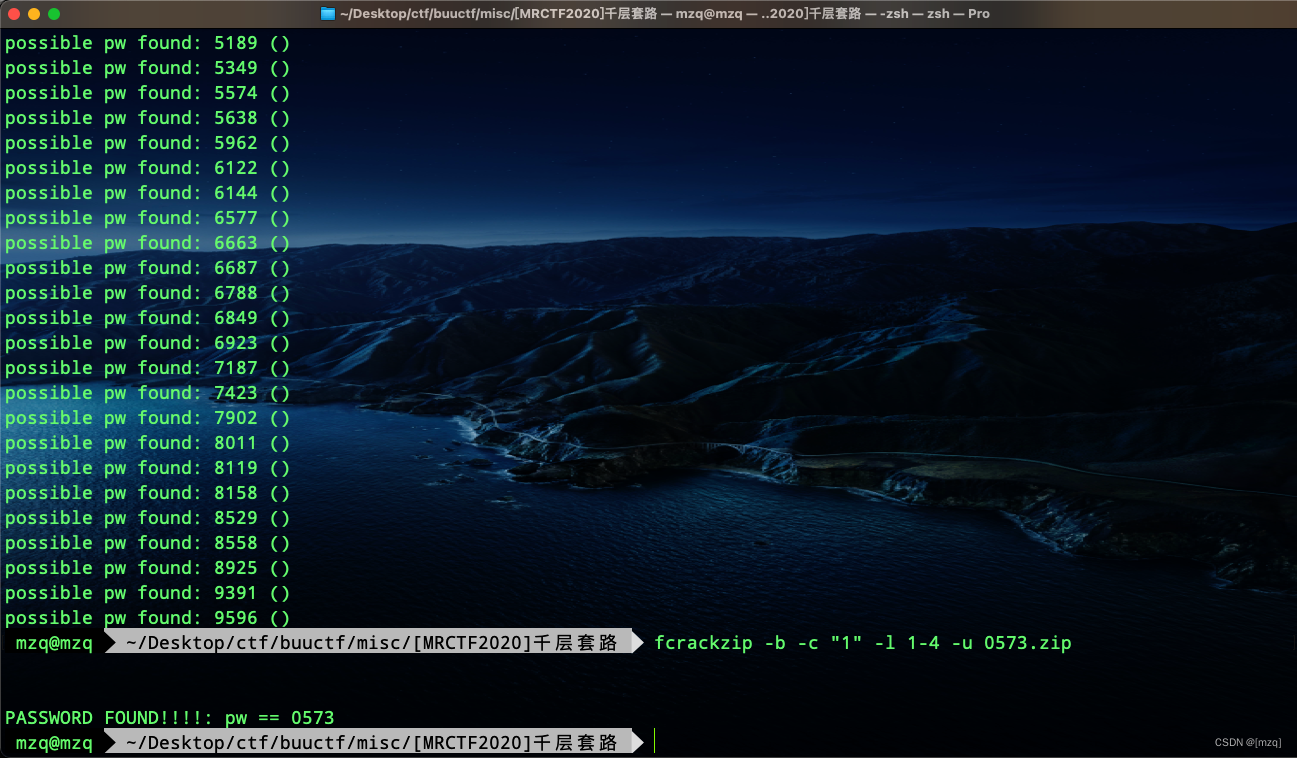
Decompress the package , It is found that the password is actually the name of the compressed package , Then according to the topic ,tnnd It's a doll problem again
import zipfile
file_path = input('path : ')# Compress package path
path = "/Users/mzq/Desktop/ctf/buuctf/misc/[MRCTF2020] Thousand layer routine /"
# path = file_path[0:len(file_path)-len(file_path.split('//')[-1])]
print(path)
n = 0
s2 = ""
def extract():
i = file_path.split('\\')[-1]# Recursive decompression package name
print(i)
str1 = ''
for x in range(1000):
ss = i[:i.find(".")]
print(ss)
zpf = zipfile.ZipFile( path+ss + ".zip")
list = zpf.namelist()
#print(list)
print(x + 1)
for f in list:
#print(f)
passwd = ss
#passwd = f.split('.')[0]# Zip code
#print(passwd)
zpf.extract(f, path, bytes(passwd.encode('utf-8')))
if 'zip' in f:
print(path, passwd)
i = str(f)
extract()

In the end, we solved a qr.zip
qr.zip After unzipping, we get qr.txt , There are some pixel values , Or coordinate value
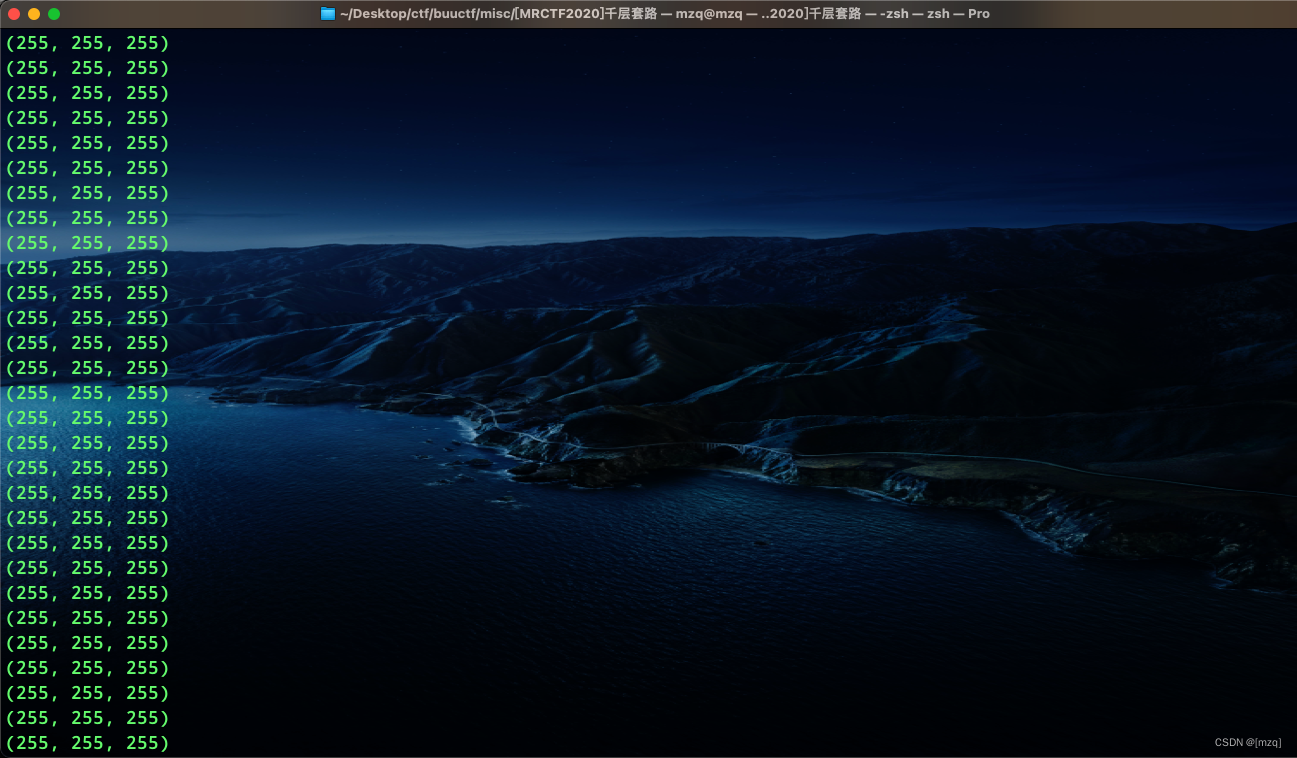
Use script puzzles
from PIL import Image
file=open('qr.txt')
MAX=200
picture=Image.new("RGB",(MAX,MAX))
for y in range(MAX):
for x in range(MAX):
string =file.readline()
picture.putpixel([x,y],eval(string)) # Use it directly eval() Can be converted to tuples
picture.show()

MRCTF{ta01uyout1nreet1n0usandtimes}
边栏推荐
- One year since joining Tencent
- Hyperledger fabric ledger snapshot - fast data synchronization
- 捏脸师: 炙手可热的元宇宙造型师
- The latest crawler tutorial in 2021: video demonstration of web crawling
- 2、 What is the principle of layer 3 and 4 switching technology? Recommended collection!
- Stop looking! The most complete data analysis strategy of the whole network is here
- Huawei Cloud Database Advanced Learning
- [机缘参悟-29]:鬼谷子-内揵篇-与上司交往的五种层次
- RDD基础知识点
- 电脑如何打开软键盘,教大家Win10如何打开软键盘的方法
猜你喜欢
随机推荐
Huawei cloud database advanced learning
超宽带脉冲定位方案,UWB精准定位技术,无线室内定位应用
How can genetic testing help patients fight disease?
使用SystemParametersInfo访问用户界面设置
What is a CC attack? How to judge whether a website is attacked by CC? How to defend against CC attacks?
Bjdctf 2020 Bar _ Babystack
get_started_3dsctf_2016
自动化测试是什么?什么软件项目适合自动化测试?
2022蓝队HW初级面试题总结
[从零开始学习FPGA编程-41]:视野篇 - 摩尔时代与摩尔定律以及后摩尔时代的到来
JVM debugging tool -jmap
Leetcode probability interview shock series 11~15
学会使用楼宇控制系统BACnet网关没那么难
二分专题训练
Deploy loglistener in tke container to collect logs to CLS
Software performance test analysis and tuning practice path - JMeter's performance pressure test analysis and tuning of RPC Services - manuscript excerpts
Can the small fire Chunfeng tea make its debut by "keeping fit"?
利用微搭低代码实现级联选择
Mysql---三张表(student,课程,分数) 查询课程为数学的学生姓名,编号,成绩
The latest crawler tutorial in 2021: video demonstration of web crawling
![[WUSTCTF2020]alison_likes_jojo](/img/a9/dcc6f524772cd0b8781289cbaef63f.png)


![[image segmentation] retinal vessel segmentation based on morphology with matlab code](/img/e3/0805df81a597346ea7c2d2da20ac96.png)