当前位置:网站首页>Introduction to web security SSH testing and defense
Introduction to web security SSH testing and defense
2022-07-23 19:53:00 【51CTO】
SSH brief introduction :
SSH by Secure Shell Abbreviation , from IETF Network group of (Network Working Group) Established by ;SSH For the security protocol based on the application layer .SSH It's more reliable , A protocol designed to provide security for remote login sessions and other network services .

SSH Blast
If you are setting SSH The service , The administrator sets the user name and password that are easy to guess ( Weak password ), Then the ECS is easy for hackers to use the corresponding password tools to violently explode weak passwords . After blasting, you can log in to the system with the corresponding user name and password . So remind everyone : The login password of ECS must not be set to weak password .
Defensive skills
1、 The most important thing is to modify SSH Default login port , The modification method is mainly to modify ssh The configuration file
2、 Use a password with high complexity
3、 Use key pair ( The key file ) land
Caught analysis
Use kali Medium hydra Tools

Create a user name dictionary

Create account information

I found that I had been trying ssh land
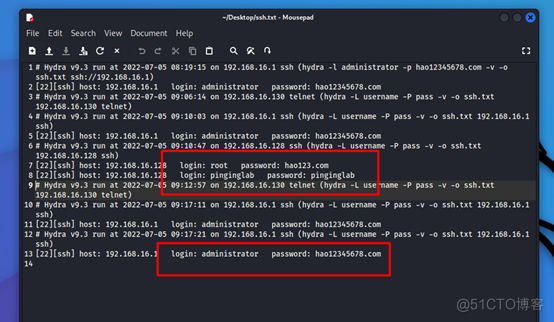
Log in the recorded information successfully .
边栏推荐
- 安全停止nodeos
- socat 使用「建议收藏」
- Redux求和案例详解版教程
- 梅科尔工作室-华为14天鸿蒙设备开发实战笔记五
- R语言ggplot2可视化:使用ggplot2可视化散点图、使用ggpubr包的theme_classic2函数设置可视化图像为经典主题(classic theme with axis lines)
- Ggarrange function of R language ggpubr package combines and annotates multiple images_ Figure add annotation, annotation, annotation information to the combined image, and add annotation information
- R language uses dwilcox function to generate Wilcoxon rank sum statistical distribution density function data, and uses plot function to visualize Wilcoxon rank sum statistical distribution density fu
- 3D point cloud course (VII) -- feature point description
- 虹科干货 | 教您如何解析MODBUS中的浮点型数据
- 能量原理与变分法笔记19:最小余能原理+可能功原理
猜你喜欢

Robot decision-making system based on self-learning (daki technology, Zhao kaiyong)

Redux summation case explanation version tutorial

Redux求和案例详解版教程

将本地镜像发布到阿里云仓库

基于自学习的机器人决策系统(达闼科技赵开勇)

PowerCLi 将虚拟机从Host01主机移动到Host02主机

干货!神经网络中的隐性稀疏正则效应

Codeforces Round #809 (Div. 2)【VP记录】

AtCoder Regular Contest 144【VP记录】

Codeforces Round #805-#808【部分题解】
随机推荐
Attack and defense world web question Fakebook
Eight common SQL misuses in MySQL
R language uses the ggarrange function of ggpubr package to combine multiple images, and uses the ggexport function to save the visual images in BMP format (width parameter specifies width, height par
redis过期key的删除策略[通俗易懂]
ACM MM 2022 Oral | DIG: 自监督文字识别的新框架,刷新11个公开场景文字数据集的识别性能,平均提升5%...
Powercli moves virtual machines from host01 host to host02 host
攻防世界web题-fakebook
Decryption: PTP clock synchronization in intelligent substation (Beidou clock server)
R language uses dwilcox function to generate Wilcoxon rank sum statistical distribution density function data, and uses plot function to visualize Wilcoxon rank sum statistical distribution density fu
为啥一问 JVM 就 懵B ?
能量原理与变分法笔记18:虚力原理
Educational codeforces round 132 (rated for Div. 2) [competition record]
能量原理与变分法笔记15:微元法的求解
Why do you get confused when you ask JVM?
简历上写的电商,那请问Redis 如何实现库存扣减操作和防止被超卖?
Canvas draw text and clear draw
Calculation of structure size (structure memory alignment)
Energy principle and variational method note 17: generalized variational principle (identification factor method)
Leetcode - the nearest sum of three numbers
R language uses the quantile function to calculate the quantile (percentile) of vector data or dataframe to specify the data column