当前位置:网站首页>网络安全——中间人攻击渗透测试
网络安全——中间人攻击渗透测试
2022-07-24 13:32:00 【Beluga】
中间人攻击渗透测试
第一步,打开网络拓扑,启动实验虚拟机,分别查看虚拟机IP地址:
Kali Linux

Linux

Windows XP

1.进入客户端Windows XP, 在CMD命令行中查看本地的arp缓存表的操作,并将该操作所使用的命令作为Flag值提交;

Flag:arp -a
2. 在客户端Windows XP的CMD命令行中清除本地的arp缓存表,并将该操作所使用的命令作为Flag值提交;

Flag:arp -d
3.通过渗透机Kali Linux对客户端Windows XP以及靶机Linux进行中间人攻击渗透测试,使用echo命令开启渗透机Kali Linux的路由转发功能,并将该配置文件的绝对路径作为Flag值提交;

Flag:/proc/sys/net/ipv4/ip_forward
4.通过渗透机Kali Linux对客户端Windows XP以及靶机Linux进行中间人攻击渗透测试,通过arpspoof命令对客户端(Windows XP)以及靶机(Linux)进行arp污染 ,并将该操作必须要用到的参数作为Flag值提交;

Flag:t
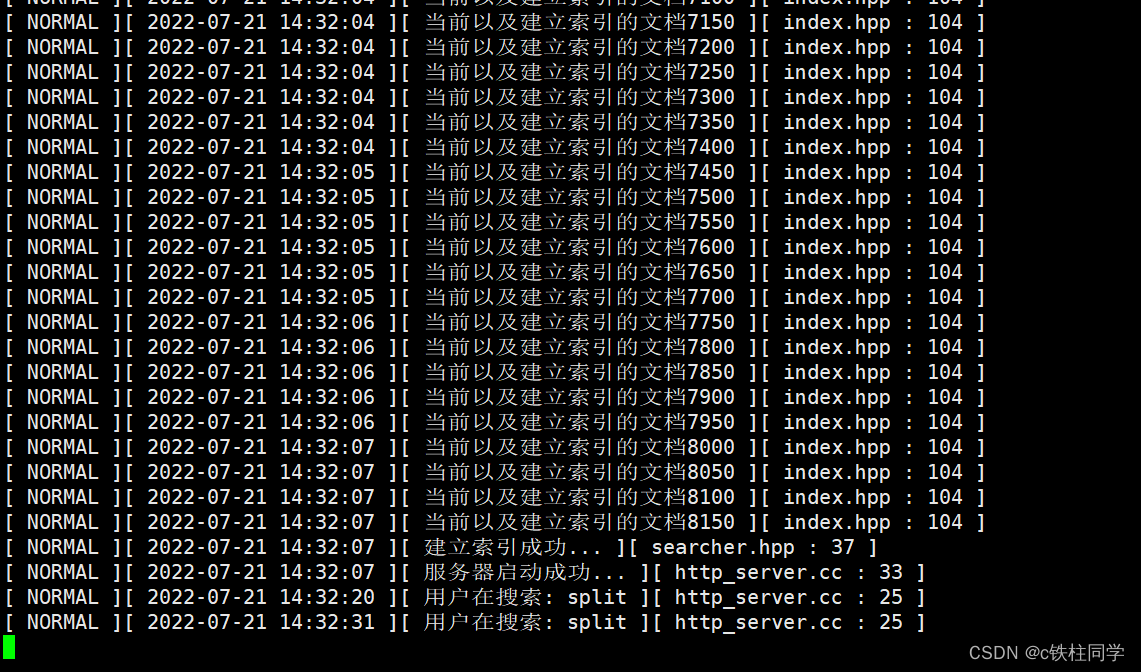
5.中间人渗透攻击成功后,渗透机Kali Linux能够监听到客户端Windows XP向靶机(Linux)中的login.php页面提交的登陆网站用户名、密码等信息。使用客户端Windows XP桌面上的Chrome浏览器访问Linux靶机的Web站点http://Linux靶机ip/login.php,使用已经保存好的用户名,密码直接登录,并在Kali Linux上使用抓包软件Wireshark进行抓包,设置Wireshark过滤规则,过滤所有请求方式为POST的HTTP请求包,将需要使用的过滤器表达式作为Flag值提交;(==符号前后不要加空格)
首先进入渗透机kali上,使用命令wireshark打开抓包软件,开启eth0网卡的监听

然后进入客户端打开桌面上的Chrome浏览器,访问http://172.16.1.200/login.php页面,用户名和密码已自动填充,点击Login登录即可

登录成功后回到渗透机,使用过滤规则进行过滤

Flag:http.request.method==POST
6.分析抓到的POST请求包,并将POST请求内容中客户端(Windows XP)向靶机(Linux)中的login.php页面提交的admin用户的密码作为Flag值提交;

Flag:iNDs1r3Q
边栏推荐
- 汉字风格迁移篇---无监督排版传输
- 从云原生到智能化,深度解读行业首个「视频直播技术最佳实践图谱」
- Selenium environment configuration and eight elements positioning
- About thread (3) thread synchronization
- Notes on Linear Algebra -- lesson 25 -- projection of vectors on axes
- EAS approval process related table
- Thread multithreading
- Atcoder beginer contest 261 f / / tree array
- Arduino框架下ESP32 EEPROM库函数实现对各数据类型保存示例
- 2022.07.21
猜你喜欢

指针进阶部分(1)
基于boost库的搜索引擎

Handler learning

Constraintlayout learn from 0 to 0.n
Experience sharing | how to use SaaS for enterprise knowledge management

Group knowledge map: distributed knowledge transfer and federated map reasoning

Make a fake! Science has exposed the academic misconduct of nature's heavy papers, which may mislead the world for 16 years
The core capability of accelerating enterprise data application innovation flexibility

Overview of multi view learning methods based on canonical correlation analysis

爱可可AI前沿推介(7.24)
随机推荐
Atcoder beginer contest 261e / / bitwise thinking + DP
Go deadlock problem
Search engine based on boost library
SSM online examination system including documents
The scroll bar in unity ugui is not displayed from the top when launching the interface in the game
LEADTOOLS 22 套件 LEADTOOLS 超级套
Unity UGUI中scroll bar在游戏中启动界面时没有从最上面显示
From cloud native to intelligent, in-depth interpretation of the industry's first "best practice map of live video technology"
Experience on how to improve the anti-interference of TTL (UART) communication
Common doc commands
Queue (stack)
Introduction to encryption technology
Relevant laws of animation movement (judge where to move according to parameters)
Is there any potential safety hazard for Xiaobai to open an account with Guotai Junan?
Sort method -- bubble sort (use an array to sort a string of numbers from large to small or from small to large)
Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation
基于社会媒体数据增强的交通态势感知研究及进展
Implementation of dynamic columns in EAS BOS doc list
户外广告牌不能“想挂就挂”!广州城管部门加强户外广告安全管理
How can flinksql run in perjob mode on yarn? I submit tasks on SqlClient