当前位置:网站首页>System safety and Application
System safety and Application
2022-07-24 06:36:00 【Walking Di five flowers】
Catalog
One 、 Account security control
Two 、 Password security control
3、 ... and 、 Historical command restrictions
One 、 Reduce the number of commands in history
Two 、 Automatically clear history when logging out
3、 ... and 、 How long will idle automatically exit the terminal
Four 、 adopt PAM Module to prevent brute force cracking ssh
5、 ... and 、 Limit su Command the user
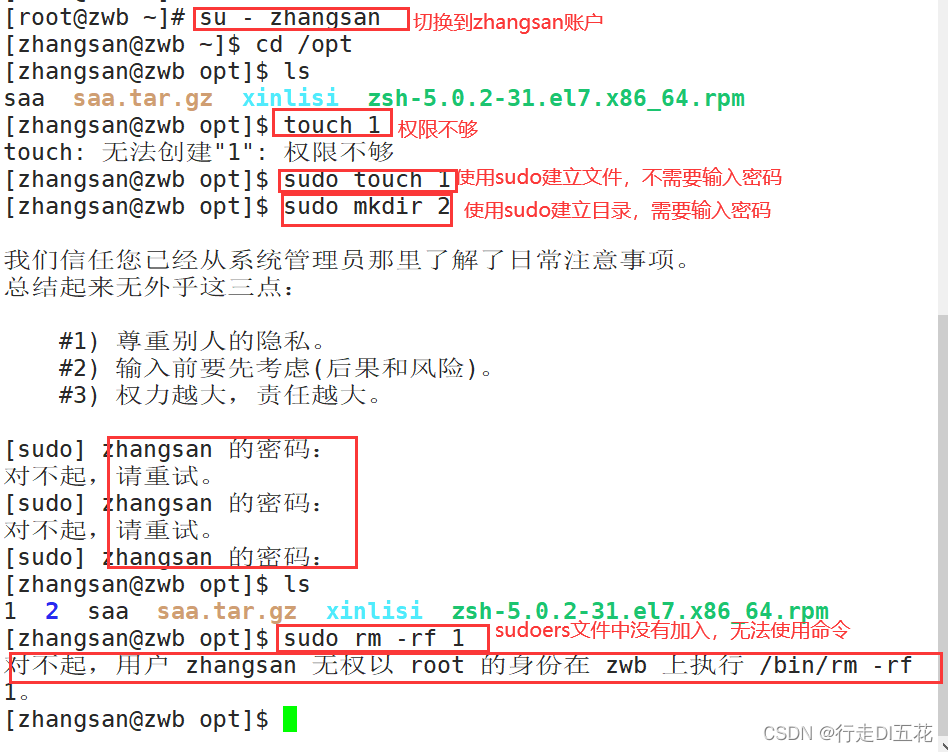
6、 ... and 、sudo Mechanism to enhance permissions
One 、 Account security control
Basic measures to control account security :
① Will not be the login user's Shell Set to /sbin/nologin
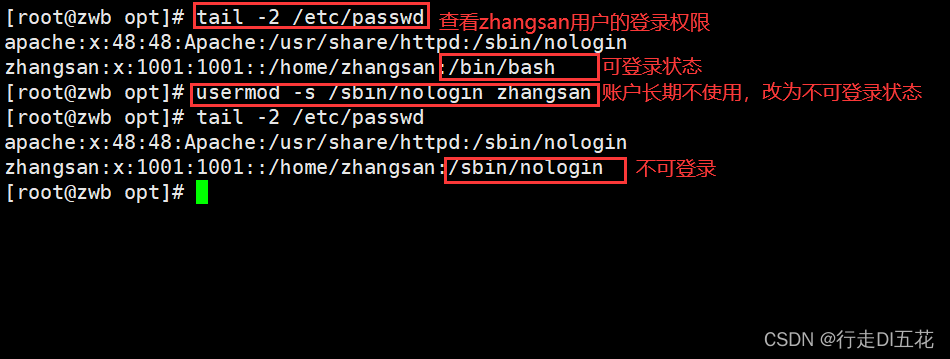
② Lock accounts that you don't use for a long time

passwd -l Account name Lock account
passwd -u Account name Unlock the account
③ Delete useless accounts

④ Lock account file passwd、shadow( Freeze the creation of new users )
Lock account file ( Or ordinary documents ) No modification 、 write in 、 Delete
chattr -i /etc/passwd /etc/shadow
Unlock the account file ( Or ordinary documents )
lsattr /etc/passwd /etc/shadow
for example : Lock account files , It is forbidden to create new users

Unlock the account file

for example 2:
hold opt In the catalog ceshi file locking , Verify whether it can be deleted and modified 、 see

result : After locking, you can only view , Cannot modify or delete
Two 、 Password security control
measures ① Set password expiration date
Change the validity of the account :chage -M 30 wangwu
② Ask users to change their password the next time they log in
Force password change at next login : chage -d 0 wangwu
For example, one : Old users zhangsan The validity of the account is changed to 30 God

adopt chage -l see 
For example, two : New account , Change its password to be valid for 30 God
“/etc/login.defs” Files are some plans when creating a user , For example, when creating a user , Do you need a home directory ,UID and GID The scope of and the duration of users , This document is available through root To define the
![]()
The contents of the document :
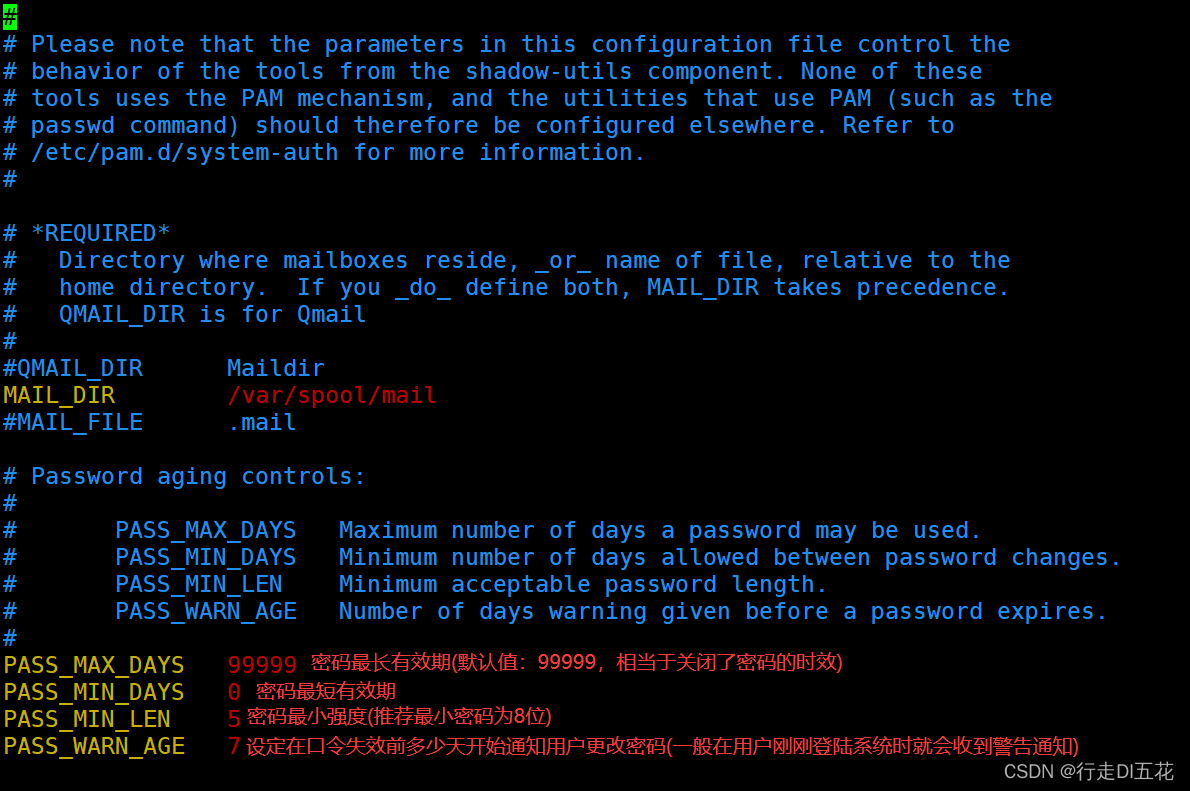 hold PASS_MAX_DAYS: Maximum password validity 99999 Change it to 30 when , The validity period of the new account password changes to 30 God .
hold PASS_MAX_DAYS: Maximum password validity 99999 Change it to 30 when , The validity period of the new account password changes to 30 God .
3、 ... and 、 Historical command restrictions
Want to reduce the number of commands in history , We can go in first /etc/profile Set in the environment variable configuration file , Set it to take effect after saving and exiting , The order is : source /etc/profile, Or restart it directly .
One 、 Reduce the number of commands in history
Ⅰ 、 Modify the global history configuration , Effective with all users and terminals vim /etc/profile
source /etc/profile Reload the file until its changes take effect

Reload takes effect

verification :

Ⅱ 、 modify ROOT User's history configuration information , Only right ROOT User effective
cd ~
ls -a
vim .bash_profile
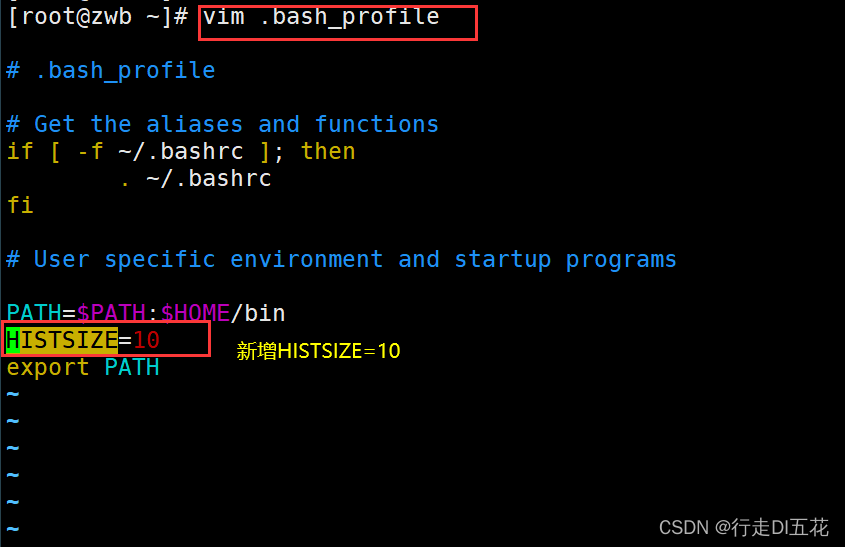
source .bash_profile Reload file

Two 、 Automatically clear history when logging out
① First empty the home directory .bash_history Everything in

② edit .bash_logout

③ reboot 
3、 ... and 、 How long will idle automatically exit the terminal
① Get into /etc/profile file , Check whether there is a set time , If not, add an entry
![]()
add to 、 preservation , sign out .

② Reload
source /etc/profile
![]()
expand :
root There are four hidden files in your home directory :.bash_profile 、.bash_logout 、.bash_history 、.bashrc
1、.bash_profile : user Use this file to enter your own shell Information , When the user logs in , The file is only executed once . By default , He sets some environment variables , Will point to and execute the user's .bashrc file .
In the system /etc/profile. It defines a global environment variable ; and .bashrc What is defined is the user's environment variable .

2、.bashrc : Current user's own environment variables . The file also includes the promotion of executing global environment variables .

3、 .bash_logout: The command that will be executed when the user logs out , Such as clearing traces and other operations
4、.bash_history: Record the commands executed by this user
Read order of environment variables : The user login 》》 load ~/.bash_profile (.bash_profile The first thing to be carried out is to put .bashrc Entry into force of documents )》》.bash_profile(.bashrc” The commands in the file will be loaded every time “/bin/bash (Shell Interpreter )》》 .bash_logout In the exit shell Is read when
Four 、 adopt PAM Module to prevent brute force cracking ssh
① Configuration method : file location /etc/pam.d/sshd
Add... On the next line auth required pam.tally2.so deny=3 unlock=600 even_deny_root root_unlock_time=1200 ( Login attempt failed for more than 3 Time , Ordinary users 600 Seconds to unlock ,root user 1200 Seconds to unlock )

5、 ... and 、 Limit su Command the user
By default , Any user is allowed to use su command , So you have the opportunity to try other users again and again ( Such as root) Login password for , This brings security risks . stay /etc/pam.d/su The settings in the file prohibit users from using su command .
① To look at first /etc/pam.d/su The contents of the document , Mainly look at the second and sixth lines

The second line :2 auth sufficient pam_rootok.so
Sixth elements :6 #auth required pam_wheel.so use_uid
notes :1、 The above two lines are the default state ( That is, open the second line , Note line 6 ), In this state, all users are allowed to use su Command to switch ( No password is required for switching between users with the same permissions , High cut low also does not need a password , Low cut high requires password .

2、 Comments on both lines are also available to all users running su command , but root Next use su Switch to other ordinary users need to enter a password , If the second line doesn't explain ,root Use su You don't need to enter a password to switch to a common user .
① To configure /etc/pam.d/su file , Comment on the second and sixth lines

② verification
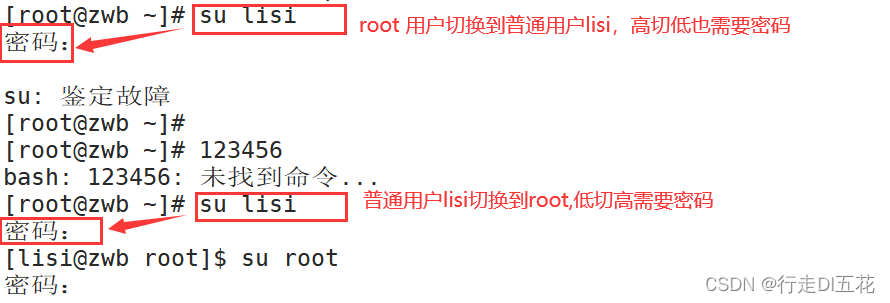
3、 Open the second and sixth lines , Only root Users and wheel Only users in the group can use su command
① Set up vim /etc/pam.d/su Open the second and sixth lines

② verification : at present lisi and wangwu stay wheel Within the group
hold wangwu Add to wheel
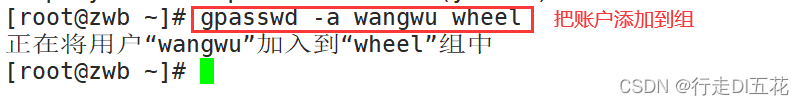
see wheel The group members

Switch verification Last input exit You can exit to the last environment variable .
4、 If you comment on the second line , Open the sixth line , Only whee1 Only users in the group can use su command ,root Users are also disabled su command .
① Note the second line , Open the sixth line

② verification : at present lisi and wangwu stay wheel Within the group
6、 ... and 、sudo Mechanism to enhance permissions
function : As other users ( Such as root) Execute the order of authorization
Get into vim /etc/sudoers File and edit : Or directly visudo
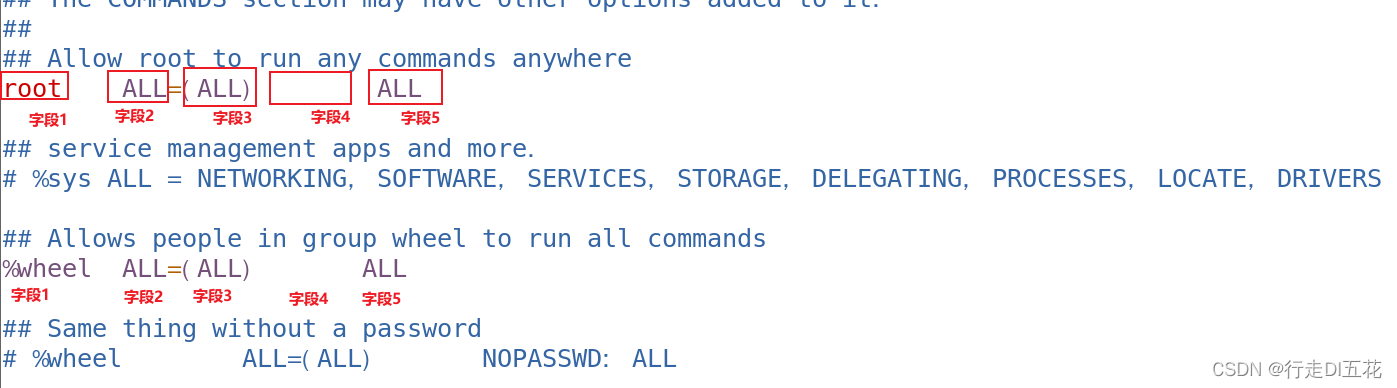
Field 1:
Don't to % Initial representation ” Users to be authorized “ by root
With % Initial representation ” The group to be authorized “ by wheel
Field 2: Indicates the hostname of the running login
ALL Express all ; If the field is not ALL, It means that authorized users can only log in on the specified machine to use sudo command
Field 3: If omitted , amount to (root:root), Means that it can be passed sudo It's up to root; If (ALL) perhaps (ALL:ALL), Means to be able to raise the right to ( Any user : Any user group )
Field 4: The possible value is NOPASSWD:. Please note that NOPASSWD With a colon at the back :. Indicates execution sudo You don't need to enter a password
Field 5: Operations authorized to users , The command line uses an absolute path
for example :


verification :
7、 ... and 、nmap
function : have access to NMAP Scan target host , The main output is the port 、 agreement 、 host ip、 Whether to survive the action scenario :
1、 Scan the specified protocol (TCP/UDP) Target of port IP、 Host name 、 Whether the network number is turned on
2、 Scan which hosts in the specified network segment are alive / Open
8、 ... and 、 netstat
function : Used to display network status
Common options :
-a:--all, Show all links and listening ports
-l:--listening, Display all listening ports
-u: be-all udp Protocol port
-t: be-all tcp Protocol port
-p:--programs, Link related program name and process PID
-n: Use the domain name resolution function

summary :
Learned system security , Through account number 、 password 、 Historical command record 、 Anti violent cracking ssh, And restrictions su Switch and pass sudo Assign the specified command to the specified user root jurisdiction .
边栏推荐
- Configure a fixed remote desktop address [intranet penetration, no need for public IP]
- How to build a website full of ritual sense and publish it on the public website 1-2
- API process and code structure
- OpenSSL version upgrade
- RAID的配置实验
- 【218】CS架构和BS架构以及数据放在服务端和客户端的利与弊?
- LVM and disk quota
- 联合国农产品数据分析
- IP notes (7)
- Write blog at leisure ~ briefly talk about let, VaR and Const
猜你喜欢

项目上复盘引导问题清单

Data set and pre training model
![Remote connection to Qunhui NAS at home [no public IP, free intranet penetration]](/img/bf/cda5a28f0aabb28b2fc56a79480347.png)
Remote connection to Qunhui NAS at home [no public IP, free intranet penetration]

【214】什么是自动化框架
![Map the intranet to the public network [no public IP required]](/img/d0/b391bcfcaeb4c7ad439e241334361b.png)
Map the intranet to the public network [no public IP required]
Custom MVC 2.0
Yiwen node installation, download and configuration

Li Kou 986. Intersection of interval lists

Maximum value of jz47 gifts (dynamic planning ideas)
![[no need for public IP] configure a fixed public TCP port address for remote desktop raspberry pie](/img/85/dec6a66dd10c35e2519bd240c05de1.png)
[no need for public IP] configure a fixed public TCP port address for remote desktop raspberry pie
随机推荐
Do not rent a server, build your own personal business website (how to buy a domain name)
一批面试题及答案_20180403最新整理
Work summary of a test Manager / Test Supervisor / test director
Leetcode sword finger offer JZ9 dual stack implementation queue
go语言的快速上手
Leetcode sword finger offer jz42 maximum sum of continuous subarrays
Custom MVC 2.0
Crud of MySQL
Life warning Maxim
Process and planned task management
IP notes (12)
自定义zabbix agent rpm包
LVM与磁盘配额
一个测试经理/测试主管/测试总监的工作总结
Function application of MySQL
Install Apache manually
Public access intranet IIS website server [no public IP required]
sed命令
Login page + summary
Flex layout