当前位置:网站首页>Only 187 bytes of desktop dream code
Only 187 bytes of desktop dream code
2022-06-23 08:30:00 【Khan security team】
<body onload='setInterval(f=_=>{for(t++,o=i=0,w=35;i<384;o+=i++%+w?(f+f+f)[i].fontcolor(g==9?"#FFF":[0,g,0]):"\n")g=0|(i/w-t/((i%w)**5%w+3)+w*t)%w;p.innerHTML=o},t=9)'bgcolor=X><pre id=p>
<!-- used for sharing only -->
</pre>
<title>MATRIX QUINE - 187 Bytes of HTML and JavaScript</title>
<meta name="viewport" content="width=300, initial-scale=1" />
<meta name="description" content="An animated quine by Martin Kleppe (aka @aemkei) that renders its own source code." />
<meta name="twitter:card" content="summary_large_image">
<meta name="twitter:title" content="Matrix Quine">
<meta name="twitter:description" content="An animated quine by Martin Kleppe (aka @aemkei) that renders its own source code.">
<meta name="twitter:image" content="https://aem1k.com/matrix/quine/preview.png">边栏推荐
- 给你的win10装一个wget
- Vulnhub | DC: 4 |【实战】
- 词性家族
- Go data types (II) overview of data types supported by go and Boolean types
- aquatone工具 中的2個bug修複
- Idea true permanent activation method and permanent activation code tutorial
- Data assets are king, analyzing the relationship between enterprise digital transformation and data asset management
- Map接口及其子实现类
- Interpretation of the most dirty technology in history, I can understand 60 it terms in seconds
- Cloud computing "half peak"
猜你喜欢

The most commonly used 5-stream ETL mode
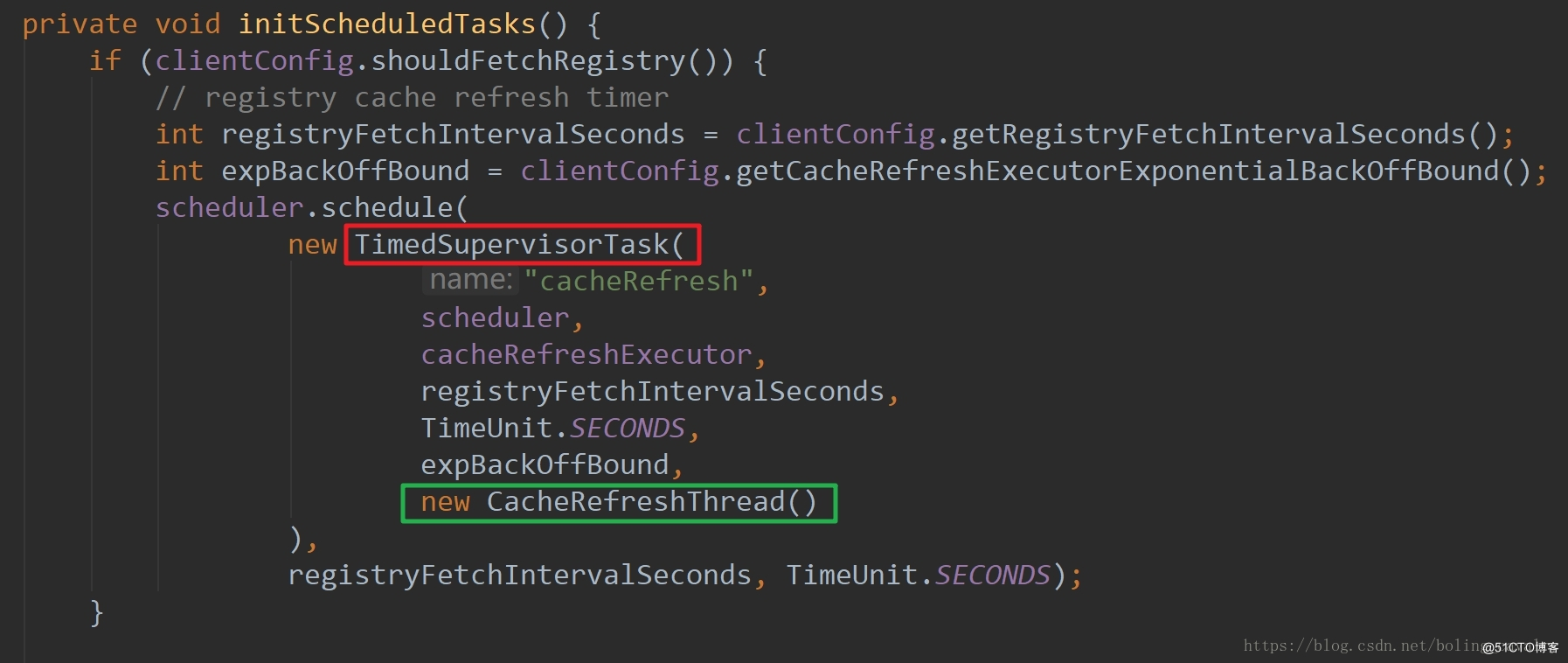
实战监听Eureka client的缓存更新

Implementation principle and source code analysis of ThreadPoolExecutor thread pool

点云库pcl从入门到精通 第十章

Introduction to typescript and basic types of variable definitions

jmeter压测结果分析

Monitor the cache update of Eureka client

Image segmentation - improved network structure
渲染效果图哪家好?2022最新实测(四)

鸿蒙读取资源文件
随机推荐
USB peripheral driver - debug
Dongyuhui, the "square face teacher", responded that the popularity was declining: do a good job of live broadcasting of agricultural products to benefit farmers and consider supporting education
Deep learning ----- convolution (conv2d) bottom layer
单编内核驱动模块
Azure Active Directory brute force attack
Openvino series 18 Real time object recognition through openvino and opencv (RTSP, USB video reading and video file reading)
Focus! Ten minutes to master Newton convex optimization
观察者模式
kibana 重建index后,如何恢复Visualizations和 Dashboards
Multi-scale feature combination in target detection
ThreadPoolExecutor线程池实现原理与源码解析
usb peripheral 驱动 - configfs
Moodle e-learning platform fixes the session hijacking error that leads to pre authorized rce
Vulnhub | DC: 4 |【实战】
Set interface and set sub implementation classes
PHP serialization and deserialization CTF
How to migrate x86 architecture applications to arm architecture at low cost
Generate code 39 extension code in batch through Excel file
Explanation on webrtc's stun/turn service in tsingsee green rhino video
2- use line segments to form graphics and coordinate conversion