当前位置:网站首页>A record of "from scratch" in college student accounts
A record of "from scratch" in college student accounts
2022-06-23 07:59:00 【Hetian network security laboratory】

This record , It is intended to show the power of information collection and arouse the attention of colleges and universities to network security ! See how to get student accounts from scratch …
After understanding the idea , You may be blown away by your masters …
The dog's head lives ~~~~
0x01: Look at this window first

If you find your password, you can either retrieve it by email , Or the cell phone is retrieved ….

0x02
Up to now , Probably
1. The mobile phone verification code exploded , Premise : Know the student number + cell-phone number + Resetting the password is to send a verification code, not to connect
2. Mailbox verification code burst , Premise : Know the student number + mailbox + Resetting the password is to send a verification code, not to connect
The above two ideas , Mostly hanging ….
( Because I dug the hole first , Just wrote the article ,
So I know the student number in advance + cell-phone number ….)

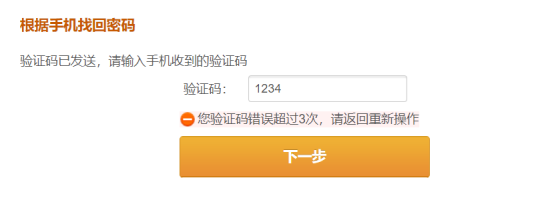
The verification code is verified …. The road is blocked ….
0x03: See how to do information gathering …..
( The process of collecting information , Be sure to learn the common excel To clean the data …., Find our useful accounts …)
Google Dafa …



After half an hour of searching , I found such an announcement , Yes, this is the announcement , Let me have a breakthrough direction …
【---- Help network security learn , All the following learning materials are free ! Add vx:yj009991, remarks “ csdn ” obtain !】
① Thinking map of the growth path of Network Security Learning
② 60+ Network security classic common toolkit
③ 100+SRC Vulnerability analysis report
④ 150+ Network security attack and defense technology ebook
⑤ The most authoritative CISSP Certification test guide + Question bank
⑥ super 1800 page CTF Practical skills manual
⑦ A collection of the latest interview questions from Wangan factory ( With answers )
⑧ APP Client security detection guide ( Android +IOS)
3、 The email user name is : Student number @xxx.xxx.xxx.cn, The initial password is :xxxx+ Birthday on the ID card 8 position ( Specific date ).Xxxx.xxx..xxx.
4、 The email in the account information of the online service hall has been bound to the student's email account by default

It is not necessary to find the user's password to obtain the account , Changing the password is also a way of thinking , As long as you can log in , Then there is nothing to say …
From seeing this announcement , Our general idea has been established ….

Specific ideas :
Look for sensitive information --- Then reset her password by email --- Finally get the account with unified identity
continue google, Found a sensitive information leak …. Number of leaks 100 Bar or so

Here is a reminder : Many students may change the password of unified identity authentication , But many students will never change the password of their email , Often used to use the mobile phone number to obtain the verification code and change the password …
And we changed her password Use email to change password ….
Find its mailbox , Log in, good guy , Login successful ….

0x04:
Unified identity authentication ….





Then we went into unified identity authentication ….
therefore
summary :
1. in general , The method is still the original method , The difference is , Be careful …
2. Don't underestimate the harm of an account , Even low privileged accounts , It can also collect all its hair …, Such as this ….
3. There are many ways to change your password , But it is recommended to use the mobile phone number to change the password , Never publish the password rules , Who knows what will happen ?
4. information gathering yyds, From a master, he set up such a view : The process of penetration testing , It's the process of collecting information to fight . Intranet is no exception !! If you collect the account passwords of many hosts , The horizontal process becomes the process of constantly entering the account password … And the movement is very small …
More range experiments 、 Network security learning materials , Please click here >> https://www.hetianlab.com
https://www.hetianlab.com
边栏推荐
- js中的同步和异步
- 某年某月某公司的面试题(1)
- openvino系列 18. 通过OpenVINO和OpenCV实现实时的物体识别(RTSP,USB视频读取以及视频文件读取)
- Hcip Road
- View the file once a second and send the result of the last line of the file to the syslog server
- Apache Solr 任意文件读取复现
- MIT CMS.300 Session 12 – IDENTITY CONSTRUCTION 虚拟世界中身份认同的建立 part 2
- Interview questions of a company in a certain month of a certain year (1)
- Qt 使用QDomDocument读取xml文件
- Gif verification code analysis
猜你喜欢

VTK. Le bouton gauche de la souris JS glisse pour changer le niveau et la largeur de la fenêtre

MIT CMS.300 Session 12 – IDENTITY CONSTRUCTION 虚拟世界中身份认同的建立 part 2

MIT CMS. 300 session 12 – identity construction Part 2

1278_ FreeRTOS_ Understand the delayed task with the prvaddcurrenttasktodelayedlist interface

Detailed explanation of redis persistence, master-slave and sentry architecture
Talk about routing design in service governance

Commonly used bypass methods for SQL injection -ctf

转盘式视觉筛选机及其图像识别系统

Eureka service registration and discovery

1278_FreeRTOS_借助prvAddCurrentTaskToDelayedList接口理解delayed task
随机推荐
MIT CMS.300 Session 12 – IDENTITY CONSTRUCTION 虚拟世界中身份认同的建立 part 2
船长阿布的灵魂拷问
C Scrollview scroll up or scroll down
socket编程(多进程)
Ignore overlength parameter violation
5本财富自由好书的精华
配置ASMX无法访问
Using jetpack datastore for data storage
Socket socket programming
Guava Cache 使用小结
firewalld 配置文件的位置
mysql中多表视图性能疑惑
深度学习------卷积(conv2D)底层
Pseudocode specification, pseudocode online editor,
@Controller和@RestController的区别?
图像分割-改进网络结构
快速删除代码里面的node_modules
Playwirght深度入门
记一次高校学生账户的“从无到有”
Eureka service registration and discovery