当前位置:网站首页>Network security database penetration of secondary vocational group in 2022
Network security database penetration of secondary vocational group in 2022
2022-06-24 18:23:00 【ruihack】
First, let's take a general look at the topic :
The first topic :

To find the web Infiltration interface of :
Let's not hurry , First use nmap Scan it. :

Found to have 80 port , Now let's visit the website :

Find this interface , If you do more, you will know , The appearance of this interface indicates that the background directory is hidden , We got a dictionary here :

Using this dictionary, we can explode its background directory :

You can see that there are two directories :

Through the interview, we found that index2.php Is a suspicious Directory :

Submit successfully .
Let's take a look at the second topic :

Ask to view the name of the database , Most people now think definitely using sqlmap For a meal output , But now if you use sqlmap Will collapse . So now we must try to inject manually . Therefore, the secondary vocational group must also learn about manual injection .

Through judgment, it is found that it is an injection of a string .
Next, we determine how many fields there are :

It is found that an error is reported , Description there are three fields , Now we can look at the topic :
The title requires the name of the database :
Let's first look at which field can be used :

Find out 1 and 2 Both can be used. :
So let's start injecting :

The database is successfully injected :

Submit successfully .
Now let's look at the third question :

The number of fields required to enter and exit the database :
We've just injected it , So we submit directly :

Submit successfully .
Look at question 4 :
Ask for the table name of the user :
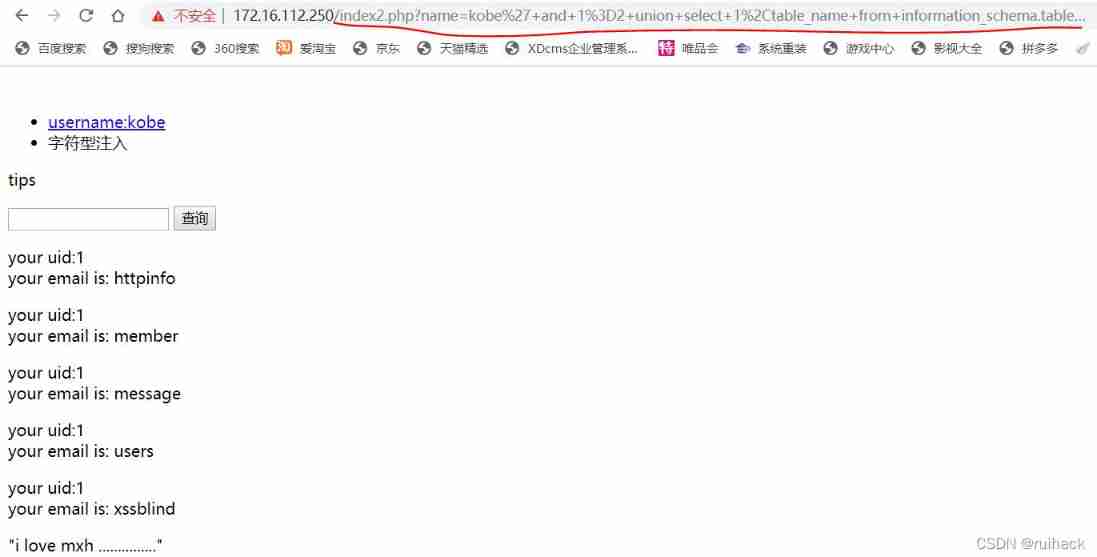
The table name is successfully injected , The name of the table where the user exists is users:

Submit successfully .
Let's move on to the next topic
:
5. Via local PC Penetration test platform in KALI2020 Test the target SQL Injection attack , Get the database information of the target , Will be used to store WEB Landing user admin The user's ciphertext password is used as FLAG Submit .
requirement admin Of md5 password :
We are operating on the basis of the table name :

Inject fields based on the table :

Admin The password of the ciphertext will come out :
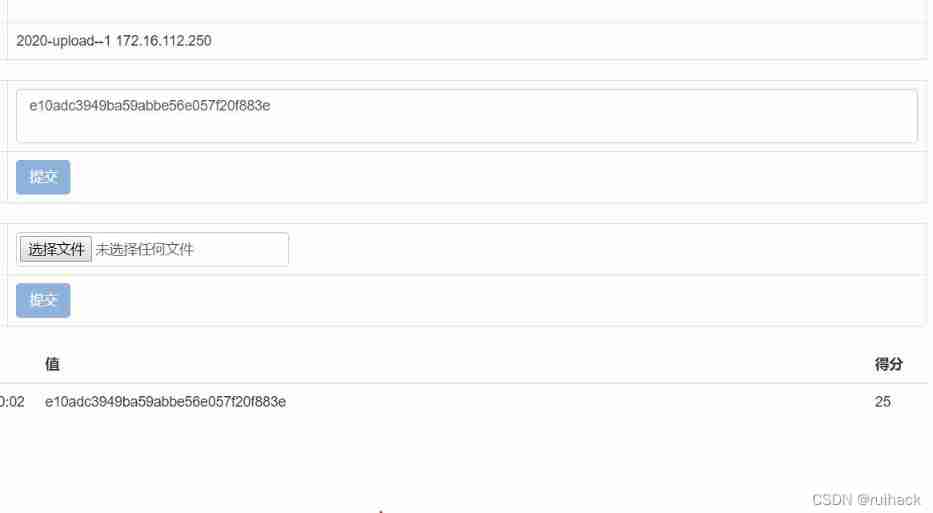
Let's move on to the next topic :

Ask for the version number of the data :
We then inject :
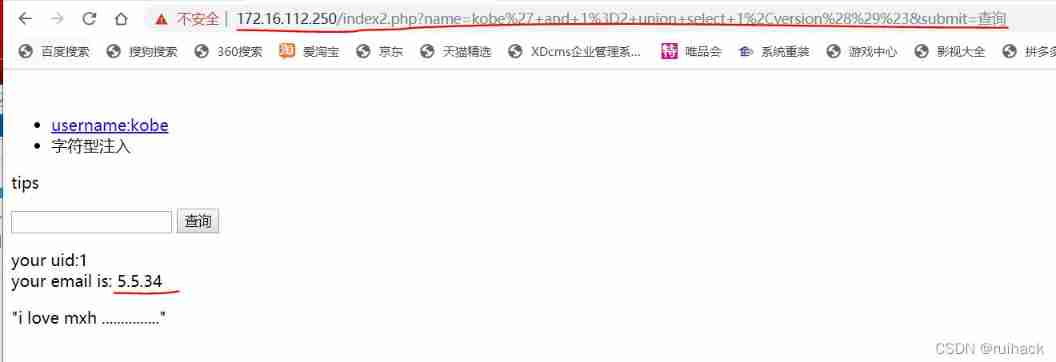
The version number has also been successfully injected :

This topic needs environment. You can confide in me .
边栏推荐
- Restful design method
- Three indicators to help you measure the effectiveness of digital transformation
- Noi Mathematics: solution of quadratic congruence equation
- Issue 39: MySQL time class partition write SQL considerations
- How to create simple shapes in illustrator 2022
- How to decompile APK files
- Project Management Guide: tips, strategies and specific practices
- TCE入围2020年工信部信创典型解决方案
- 这个巡检平台你还不知道,真是亏大了!
- About whether arm's large and small end mode is related to CPU or compiler
猜你喜欢
Millions of dollars worth of NFT were stolen in the attack, and Google issued an emergency warning to 3.2 billion users worldwide | February 21 global network security hotspot

Wechat applet to realize stacked rotation

Business leaders compete for CIO roles

On software requirement analysis
[quick news] the jeecgboot low code platform was successfully selected into the 2021 scientific innovation China · open source innovation list

Six configuration management tools that administrators must know
Issue 39: MySQL time class partition write SQL considerations
Business based precipitation component = & gt; manage-table
An analysis of the comments on the TV series Douban by procedural apes

Overall planning and construction method of digital transformation
随机推荐
On the principle of cloud streaming multi person interaction technology
浅谈云流送多人交互技术原理
Bigdecimalavoiddoubleconstructorrule: do not directly use the double variable as a parameter to construct BigDecimal
Four security issues of low code and no code development
[quick news] the jeecgboot low code platform was successfully selected into the 2021 scientific innovation China · open source innovation list
About whether arm's large and small end mode is related to CPU or compiler
[North Asia data recovery]_ mdb_ catalog. Mongodb database data recovery case in case of WT file corruption
Overall planning and construction method of digital transformation
About pyqt5 to realize paging function (one window implements different interfaces)
How about China Power Investment Xianrong futures? Is it safe to open futures accounts?
How much does it cost to develop a small adoption program similar to QQ farm?
(Video + graphics) introduction to machine learning series - Chapter 11 support vector machines
Noi Mathematics: solution of quadratic congruence equation
布隆过滤器综述文章论文阅读:Optimizing Bloom Filter: Challenges, Solutions, and Comparisons
投资理财产品的钱能随时取出来吗?
[NLP] 3 papers on how Stanford team builds a better chat AI
EasyGBS视频平台TCP主动模式拉流异常情况修复
视频平台如何将旧数据库导入到新数据库?
What makes data analysts good- Cassie Kozyrkov
持续助力企业数字化转型-TCE获得国内首批数字化可信服务平台认证

![[quick news] the jeecgboot low code platform was successfully selected into the 2021 scientific innovation China · open source innovation list](/img/1a/c148d02eb7d58a15c92a91b6cdefc4)

