当前位置:网站首页>What does ack attack mean? How to defend against ack attacks?
What does ack attack mean? How to defend against ack attacks?
2022-06-26 11:02:00 【IDC02_ FEIYA】
ACK What does attack mean ?ACK How to defend against an attack ?
ACK attack
ACK Flood The attack was TCP After the connection is established , All the transmitted TCP All messages have ACK Flag bit packets .
The receiving end receives a message with ACK Flag bit of the packet when , You need to check if the connection quadruple represented by the packet exists , If it exists, check whether the state represented by the packet is legal , Then pass the packet to the application layer .
If the data packet is found to be illegal during the inspection , If the destination port pointed to is not open , Then the operating system protocol stack will respond RST The packet tells the other party that the port does not exist .
When an attacker sends... Every second ACK The message rate reaches a certain level , In order to make the load of the host and firewall change greatly . When the contracting rate is very high , The host operating system will spend a lot of energy receiving messages 、 Judge the state , At the same time, take the initiative to respond RST message , Normal packets may not be processed in time . At this point, the client ( With IE For example ) The performance is that the response to visiting the page is very slow , High packet loss rate . This is it. ACK attack .
At this point, the server needs to do two actions , Table lookup and response ack/rst.
This type of attack does not syn flood The impact on the server is great ( because syn flood Occupied connection ), Such attacks must use large traffic ack Small packet impact will affect the server .
according to tcp Protocol stack principle , Random source IP Of ack The packet should be server Quickly discarded , Because on the server tcp These are not in the stack ack Status information of the package .
In the actual test, some tcp The service is right ack flood Is more sensitive .
about Apache perhaps IIS Come on , Dozens of kpps Of ack flood Not a threat , But a higher number ack flood The impact will cause the network card to interrupt too frequently and stop responding when the load is too heavy .
jsp server In a small number of ack Under the impact of small bags jsp server It is difficult to handle normal connection requests .
therefore ack flood Not only harm routers and other network equipment , And it also has a great impact on the application on the server .
Attack harms
attacker Use botnets to send a large number of ack message , Can cause the following three hazards :
1、 With a very large load ack flood attack , It will lead to link congestion .
2、 The attack packets arrive at the server and cause the processing performance to be exhausted , Thus refusing normal service .
3、 Very high rate variable source variable port ack flood attack , It is easy to cause the forwarding performance of devices that rely on session forwarding to degrade or even cause network paralysis .
Defense principle
resist D The device pairs based on the destination address ack Statistics of message rate , When ack The message rate exceeds the threshold and starts the source authentication defense .
The authentication source defense process is shown in the figure :

explain
1、 Start when the attack traffic reaches the threshold ack protective .
2、 The real message goes through ack After retransmission , The client relaunches the connection , At this point will pass syn Add the white list trust after the verification algorithm passes .
3、 fake ack The message is directly discarded by querying the session table .
边栏推荐
- The sixth MySQL job - query data - multiple conditions
- SQL Server 基础介绍整理
- 2、 Linear table
- Oracle sqlplus 查询结果显示优化
- Bit operation n & (n-1), leetcode231, interview question 05.06
- [Beiyou orchard microprocessor design] 10 serial communication serial communication notes
- 【深度学习理论】(7) 长短时记忆网络 LSTM
- Recent work report
- AIX basic operation record
- Basic MySQL
猜你喜欢

MySQL 9th job - connection Query & sub query

Adaptiveavgpool2d does not support onnx export. Customize a class to replace adaptiveavgpool2d
![Installer MySQL sous Linux [détails]](/img/38/77be56c3ef3923ce4c4e5df4a96f41.png)
Installer MySQL sous Linux [détails]

Using reflection to export entity data to excel

3、 Linked list exercise
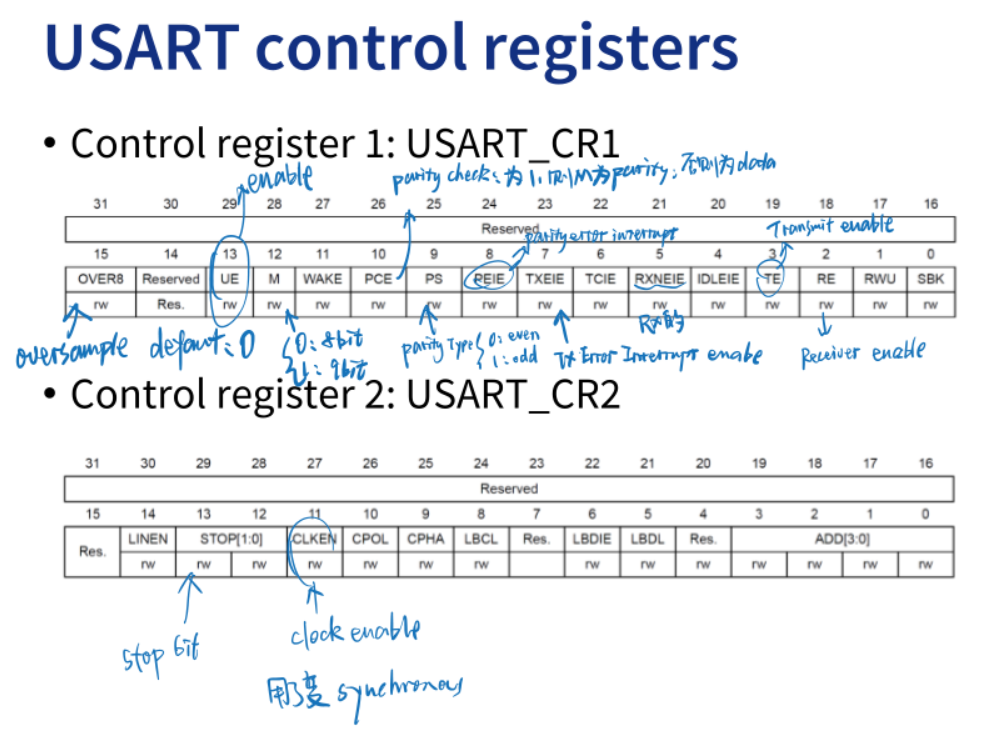
【北邮果园微处理器设计】10 Serial Communication 串口通信笔记

机器学习线性回归——实验报告

Alibaba cloud OSS - object storage service (tool)

ACK攻击是什么意思?ACK攻击怎么防御?
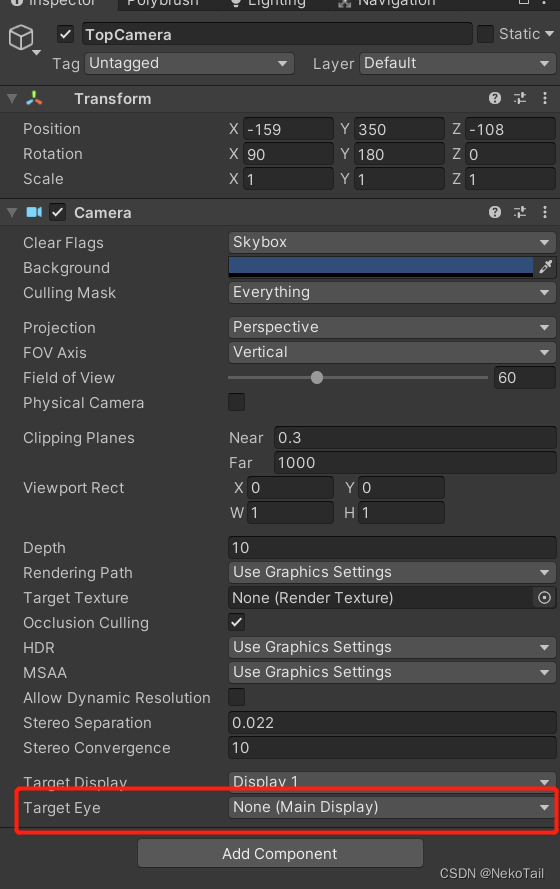
Unity使用SteamVRPlugin时如何不让其他Camera位置和旋转收到SteamVRPlugin控制
随机推荐
QT连接MySql数据查询失败
mysql性能監控和sql語句
wangEditor 上传本地视频修改
Redis (basic) - learning notes
Quantitative investment learning - Introduction to classic books
8- creating leecode algorithm with pictures and texts - algorithm solution of minimum stack and LRU caching mechanism
机器学习线性回归——实验报告
2020.7.6 interview with fence network technology company
Easyx-----c语言实现2048
OpenCV图像处理-灰度处理
AIX基本操作记录
ISO 26262 - 2 functional safety concept
Docker中实现MySQL主从复制
How does unity prevent other camera positions and rotations from being controlled by steamvrplugin when using steamvrplugin
laravel中使用group by分组并查询数量
Windows and Linux regularly backup MySQL database
UDP Flood攻击防御原理
Unity使用SteamVRPlugin时如何不让其他Camera位置和旋转收到SteamVRPlugin控制
[difficult and miscellaneous diseases] @transitional failure summary
指南针软件买股票进行交易安全吗?怎么开户买股票