当前位置:网站首页>Todolist case
Todolist case
2022-07-24 19:53:00 【_ ocean】
List of articles
Component writing process
- Split static components
- Components should be split according to function points , Do not name with html Element conflict .
- Implement dynamic components :
Consider where the data is stored , Data is a component in use , Some components are still in use :
- A component is in use : Just put it on the component itself .
- Some components are in use : On their common parent component (
Status up).
- Implement interaction
Start with binding events .
npm i nanoid
nanoid Is a stand-alone build id A third party library .
- install :
npm i nanoid - introduce :
import {nanoid} from 'nanoid' - Use :
id:nanoid()
data
If two sibling components need to share one data, will data It's defined in app in , Again by app.js Transmit the data decibel to the brother components .
How to transfer the data of child components to parent components
props Apply to :
- Parent component ==> Subcomponent communication
- Child components ==> Parent component communication ( Ask the parent to give the child a function first ):
Define a function in the parent component , With one parameter
Take the function of the parent component asprops ParametersPass to subcomponent
Subcomponents receive and call functions , To his own data Value is passed as a parameter to the function passed by the parent component .
In this way, the function of the parent component can receive the value passed by the child component
v-model And props
- Use v-model Remember to : v-model Bound value cannot be props Transmitted value , Because of this props The value of will be modified
- props If the value of the object type is passed , When modifying properties in an object Vue No mistake. , But this is not recommended .
Where is the data? , The operation of data should be where
TodoList Case realization effect
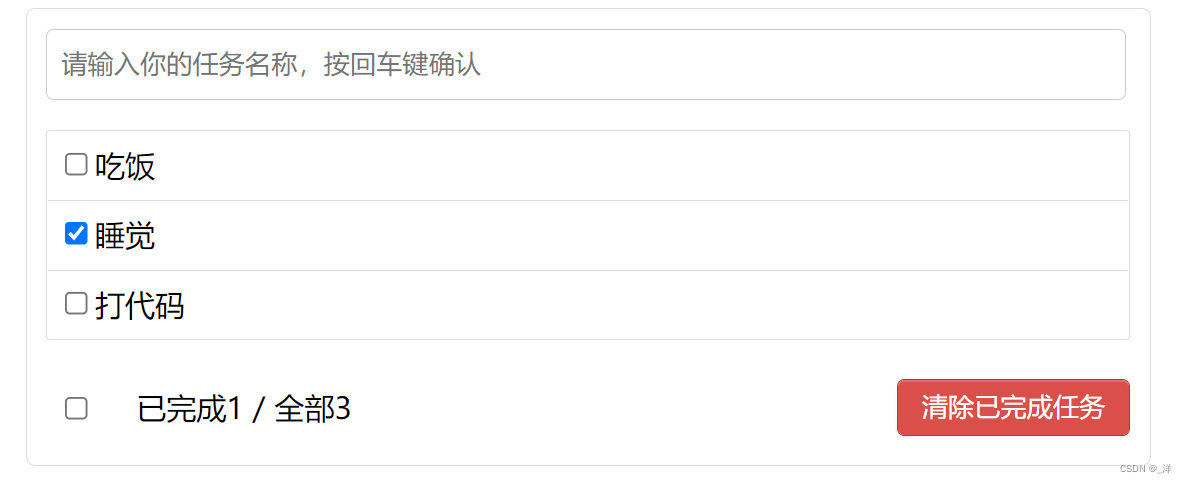
The source code for :https://github.com/Panyue-genkiyo/vue-advance/tree/master/07_src_Todolist%E6%A1%88%E4%BE%8B
边栏推荐
- Sword finger offer 48. the longest substring without repeated characters
- Functional test of redisgraph multi active design scheme
- Solve the problem of error l6218e undefined symbol XXX
- Redisgraph graphic database multi activity design scheme
- Software core data protection solution
- MySQL8.0学习记录20 - Trigger
- Channel state information (CSI) conjugate multiplication denoising method
- Sword finger offer 50. the first character that appears only once
- Please ask a question. Follow the quick start method. After creating the table, the Flink SQL queries and displays the table structure, but there is an error when it exceeds the limit. What should we
- 871. Sum of divisors
猜你喜欢

Basic idea of regularization

Sword finger offer 52. The first common node of the two linked lists
![[face to face experience of school recruitment] 8 real questions of pointer interview. Come and test how many you have mastered.](/img/2c/e687b224285aeee66dacace6331161.png)
[face to face experience of school recruitment] 8 real questions of pointer interview. Come and test how many you have mastered.

Clion configuring WSL tool chain

Tencent Browser service TBS usage

Flink Window&Time 原理

Virtual machine win7 system installation vmtool

【JVM学习03】类加载与字节码技术

Use of paging assistant PageHelper

LSTM and Gru of RNN_ Attention mechanism
随机推荐
从服务器批量下载文件到本地
从码农转型大音乐家,你只差这些音乐处理工具
Reading notes: you only look once:unified, real time object detection
MySQL8.0学习记录20 - Trigger
Look at the interface control devaxpress WinForms - how to customize auxiliary function properties (Part 2)
Sword finger offer 42. maximum sum of continuous subarrays
Description of large and small end mode
The beginning of winter in the year of bitterness and ugliness
Anaconda installs labelimg (super simple and available)
Unit DLU of resource editor
ATL container - catlmap, crbmap
Recursion of function [easy to understand]
Mysql8.0 learning record 19 - Page segments and tablespaces
Prevent static decompilation, dynamic debugging and plug-in
[in depth study of 4g/5g/6g topic -39]: urllc-10 - in depth interpretation of 3GPP urllc related protocols, specifications and technical principles -3- how to distinguish urllc services? Detailed expl
C # shelling tool for code encryption protection
Leetcode402 remove K digits
Tencent Browser service TBS usage
Leetcode652 finding duplicate subtrees
Feature extraction tool transformer Bert