当前位置:网站首页>Another double win! Tencent's three security achievements were selected into the 2021 wechat independent innovation achievements recommendation manual
Another double win! Tencent's three security achievements were selected into the 2021 wechat independent innovation achievements recommendation manual
2022-06-24 06:58:00 【Tencent security】
2021 year 6 month 20 Japan , Key information infrastructure technology innovation alliance 、《 Research Report on independent innovation of Netcom 》 Jointly organized by the editorial board and the National Engineering Laboratory of key technologies for classified protection of information security “2021 Exchange and promotion of independent innovation achievements of wechat ” The results of the selection were presented in the second China I²S The summit was announced .
The activity has been reviewed by experts , From more than 400 enterprises across the country , Selected from nearly 500 projects 100 Innovation (50 A product 、50 Solutions ) Get into 《2021 Recommendation Manual of Netcom's independent innovation achievements 》, It aims to further demonstrate the power of independent innovation of wechat , Build user confidence , Support network security and information construction in key industries .
among , Tencent Security Threat Intelligence cloud search service , Obtain recommended products with application potential “ Sky mending Award ”; Tencent security leads the blockchain central system , Get the recommended scheme for technological innovation “ Fuxi prize ”; Public user identity control solution , Obtain the recommended scheme of application potential “ Longmen Award ”. Tencent security relies on its leading technology accumulation and rich industry practice in the security field , Once again, it has been affirmed and recognized by the industry .
One 、 Build a network security cordon Tencent Security Threat Intelligence cloud search service
as everyone knows , Intelligence is an effective tool against threats . Threat Intelligence is Tencent's core security capability , Capability has been exported to SOC、NTA、 Cloud firewall 、 Host security 、 Zero trust 、 Tencent security products such as vulnerability scanning , At the same time, we will work with our partners in the security industry , For Finance 、 Internet 、 education 、 Medical care 、 Users in many industries, such as manufacturing, will bring more perfect threat intelligence services . With unique data mining 、 Professional intelligence operation team 、 Self closing loop intelligence production capacity 、 Real time intelligence verification capability and Tencent's own brand and service advantages , Able to provide high-quality IOC Intelligence detection 、 Cover massive IP Credit intelligence analysis 、 Hacker portrait analysis 、 Unknown sample detection 、 Advanced threat discovery 、 Core capabilities such as industry intelligence sharing and private intelligence mining .
at present , Tencent's threat intelligence service already has up to 99.9% Accurate intelligence delivery capability , More than 90% of self-produced intelligence , Provide customers with professional advanced threat intelligence reports at the first time , Timely discover the key units that threaten customers in various industries and are closely related to the national economy and the people's livelihood 、 Network attacks in key industries , Timely detect potential safety hazards , Promote the improvement of cyberspace security protection level .
Two 、 make “ trusted ” The urban solution Tencent security leads the blockchain central system
With the acceleration of smart city construction , Incomplete information infrastructure 、 Data silos are common 、 Hidden dangers in data security and other development pain points have emerged one after another . Tencent security leading blockchain is based on trusted computing 、 Cryptography security 、 Node security sandbox and other security technologies , Build a full-service product capability from the bottom engine to the upper application for the smart city . It has created an autonomous and controllable trusted blockchain hub platform , boost “ Blockchain +” Industry solutions landing . Combined with the city level demand , Launch trusted blockchain middle office services , Provide safe and reliable strong support for the deployment and operation of urban blockchain . At the same time, it has launched a cross chain interaction platform , Provide commonalities 、 Secure basic blockchain capabilities and Multi Chain interworking , An open service platform for chain management .
The central system of Tencent security leading blockchain has been serving government affairs 、 Judicial deposit 、 Social welfare 、 Supply chain traceability and other core application fields have been implemented , A number of representative best practices in the industry have been formed .
Urban hyperbrain field
It has provided Wuhan and other cities with the construction of blockchain urban base , Realize the safe collection of Pan government data 、 Controllable distribution, data traceability and other trusted business requirements .
The field of judicial deposit
In conjunction with Beijing Fangzheng notary office, etc., we have created a blockchain based on leadership - Beijing Founder notarization and evidence collection platform , It provides online evidence collection based on blockchain for government departments and commercial institutions 、 existing evidence 、 The whole process electronic evidence service of solid evidence .
In the field of social public welfare
To create public welfare data “ Upper chain ”, Public institutions 、 Industry Association 、 Civil Affairs Bureau 、 Credit information regulatory agency 、 Credit reference center 、 Institutions such as asset custody have joined the alliance node , Tencent commonweal has realized the whole link process of each donation data , In tencent 99 Public welfare day , Average daily processing 1 More than 100 million donation transactions .
Anti counterfeiting traceability field
Cooperate with Changyu to build the first domestic high-end wine blockchain traceability platform , In tradition “ One thing, one yard ” The production code and two-dimensional code of each bottle of wine 、 Block chain coding for double binding , Realization 400 Chain tracing of the whole process information of Wanping winery .
3、 ... and 、 Digital government 、 Safety steward of smart culture, tourism and transportation , Public user identity control solution
With the government 、 The promotion of enterprise digital transformation , The user starts moving APP、 Small programs and other channels to complete the handling of personal business , Identity security becomes the first line of defense for business security . How to ensure security and comply with personal privacy regulations , Realize the management and unified authentication of public user identity , adopt “ identity ” Open up enterprise services to enhance economic value , Tencent's public user identity control solution provides a satisfactory answer .
The scheme has fast authentication access capability 、 High availability and high performance design 、 Identity account cleaning / Polymerization technology 、 Risk control based identity authentication design and other advantages , Designed to protect all users ( natural person / legal person 、 consumer 、 Administrator, etc ) Through all channels (web、 Applet 、 APP、H5) Access to any open business system has the same consistent experience , At the same time, ensure the security in the process of business access .
The program has been implemented by the government 、 Ministries and commissions 、 Wen Brigade 、 Transportation and other industries have been successfully put into use , Serve hundreds of units , brace “ Yue Kang code ”、“ Small procedures of the State Council ”、 Census and other large projects , Ensure 100 million user visits and stable operation .
Digital government application scenarios
Help the government build a unified national identity authentication system , Realization “ A certification , All network communication office ”.
Smart cultural tourism application scenarios
A mobile phone , One size fits all , Provide tourists with the whole process experience before, during and after the tour , Improve tourism satisfaction .
Intelligent transportation application scenarios
adopt OneID Provide a convenient registration and login process , Realize ticket purchase / Redeem points / Order management / One stop business experience of the mall .
Multiple products this time / Award winning solutions , It is an affirmation of Tencent's security technology capability and product application value . In the future, Tencent security will continue to take guarding network security as its own responsibility , Continue to integrate their own security advantages and capabilities , Output more advantageous solutions for the industry , Join hands with industry partners to jointly promote the healthy and steady development of industrial Internet security .
边栏推荐
- 记录--关于virtual studio2017添加报表控件的方法--Reportview控件
- Several methods for reinstalling the system:
- C语言学生管理系统——可检查用户输入合法性,双向带头循环链表
- Database stored procedure begin end
- puzzle(019.1)Hook、Gear
- With a goal of 50million days' living, pwnk wants to build a "Disneyland" for the next generation of young people
- Overview of new features in mongodb5.0
- leetcode:1856. 子数组最小乘积的最大值
- Application of O & M work order
- Online font converter what is the meaning of font conversion
猜你喜欢
面渣逆袭:MySQL六十六问,两万字+五十图详解
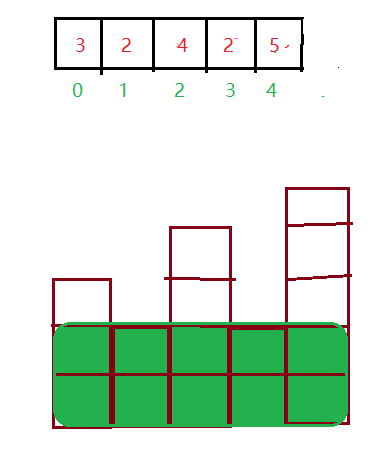
leetcode:84. The largest rectangle in the histogram

About Stacked Generalization

记录--关于JSP前台传参数到后台出现乱码的问题

Virtual file system

About Stacked Generalization
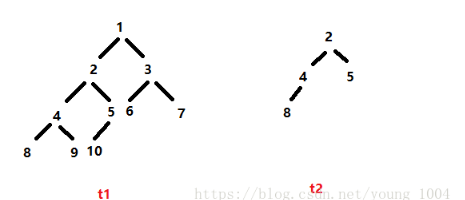
Leetcode: Sword finger offer 26: judge whether T1 contains all topologies of T2

leetcode:85. 最大矩形

leetcode:85. Max rectangle

leetcode:剑指 Offer 26:判断t1中是否含有t2的全部拓扑结构
随机推荐
Become TD hero, a superhero who changes the world with Technology | invitation from tdengine community
为什么要用lock 【readonly】object?为什么不要lock(this)?
What is the main function of cloud disk? How to restore deleted pictures
Deploy DNS server using dnsmasq
基于三维GIS系统的智慧水库管理应用
If you want to learn programming well, don't recite the code!
Laravel文档阅读笔记-Laravel Str slug() Function Example
What are the audio formats? Can the audio format be converted
Five minute run through 3D map demo
Record -- about the method of adding report control to virtual studio2017 -- reportview control
数据同步工具 DataX 已经正式支持读写 TDengine
网吧管理系统与数据库
On BOM and DOM (6): bit value calculation of DOM objects and event objects, such as offsetx/top and clearx
Authoritative recognition! Tencent cloud data security Zhongtai was selected as the 2021 pioneer practice case
The three-year action plan of the Ministry of industry and information technology has been announced, and the security industry has ushered in major development opportunities!
成为 TD Hero,做用技术改变世界的超级英雄 | 来自 TDengine 社区的邀请函
How to build an app at low cost
35 year old crisis? It has become a synonym for programmers
创客教育给教师发展带来的挑战
Game website making tutorial and correct view of games