当前位置:网站首页>Network Security Learning (II) IP address
Network Security Learning (II) IP address
2022-07-24 22:42:00 【Shake light·】
Clone virtual machine
1. Click snapshot Manager

2. Choose Clone

next step

3. Select snapshot

4. Select the clone type
The linked clone is based on the original clone , If the original clone is deleted , Then link cloning cannot be used
Full cloning is equivalent to creating a new virtual machine
Link cloning is recommended

5. Specify virtual machine name , route

Can be completed
Fundamentals of computer network
LAN : It's commonly known as the intranet
The composition of simple LAN : Switch 、 Ethernet cable 、PC( Or others IT terminal )
Switch : A device used to build a local area network for an intranet .
IP Address
IP An address is a unique identifier , It's a network code ( Binary system ), from 32 A composition
Such as 11111111.11111111.11111111.11111111
Easy to remember ( Convert to 10 Base number )
255.255.255.255
This representation is also known as dotted decimal
dotted decimal (Dotted Decimal Notation) The full name is point and minute ( Dot pattern ) Decimal notation , yes IPv4 Of IP Address identification method .IPv4 Four bytes are used to represent a IP Address , Each byte is expressed as 0~255. dotted decimal Just use 4 Group from 0~255 The number of , To represent a IP Address . Such as 192.168.1.1.
Subnet mask
LAN communication rules : In the same LAN , be-all IP You must be in the same network segment to communicate with each other .
IP The composition of the address : Network bit + Host bit ( The network bits are the same IP Address , For the same segment ).
How the subnet mask determines the network bit : And 255 The corresponding number is network bit , And 0 The corresponding number is the host bit

Here's an additional explanation IP And operation of address and subnet mask
“ And ” Operation can find this IP Subnet of address , Or the network segment it is in .
for instance :
IP: 192.168.1.160 subnet :255.255.255.128
1100 0000.1010 1000. 0000 0001. 1010 0100
1111 1111. 1111 1111. 1111 1111. 1000 0000
------------------------------------------------ Meet each other ( All for 1 Then for 1, Otherwise 0)
1100 0000.1010 1000.0000 0001.1000 0000
Convert to decimal to :192.168.1.128
IP Address details
classification
1、A class IP Address :1-126
One A class IP Address by 1 Byte network address and 3 Byte host address composition , The highest bit of the network address must be “0”, Address range from 1.0.0.0 To 126.0.0.0. Usable A There are 126 individual , Every network can hold 1 More than 100 million hosts .
2、B class IP Address :128-196
One B class IP Address by 2 Byte network address and 2 Byte host address composition , The highest bit of the network address must be “10”, Address range from 128.0.0.0 To 191.255.255.255. Usable B There are 16382 individual , Every network can hold 6 More than ten thousand hosts .
3、 C class IP Address :192-223
One C class IP Address by 3 Byte network address and 1 Byte host address composition , The highest bit of the network address must be “110”. Range from 192.0.0.0 To 223.255.255.255.C Class network up to 209 More than a , Every network can hold 254 Host computer .
4、 D class IP Address :224-239
The first byte is in “lll0” Start , It is a special door Reserved address . It doesn't point to a specific network , At present, this kind of address is used in multicast (Multicast) in . A multicast address is used to address a group of computers at a time , It identifies a group of computers that share the same protocol .
5、E class IP Address : 240-254
With “llll0” Start , Reserved for future use . All zeros (“0.0.0.0”) The address corresponds to the current host . whole “1” Of IP Address (“255.255.255.255”) Is the broadcast address of the current subnet .
stay win2003 Middle configuration ip Address
1. Right click on the Internet neighbor —— attribute

2. Right click local connection —— attribute

3. double-click tcp/ip agreement , Manual configuration ip Address ( The server uses fixed ip Address )
notes : Do not blindly follow the picture ip Address configuration !

see ip Address
1. Double click the local connection —— Support
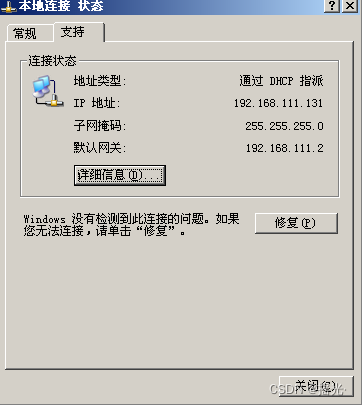
127.0.0.1
127.0.0.1 It's the return address , The local machine , Generally used to test the use of . Return address (127.x.x.x) It's the local loopback address (Loopback Address), I.e. mainframe IP Inside the stack ip Address , It is mainly used for network software testing and local computer , No matter what interprocess communication program , Once the data is sent using the return address , The protocol software immediately returns , No network transmission .
experiment
1. Turn on two virtual machines , Change the configuration to the setting in the figure
Among them, custom VMent Out of commission 0

2. Turn off the system firewall
Off by default
3. Set up the computer manually ip Address , Make it in the same network segment


4. Using the command line ping Command test (win + R—— Input cmd)

Some test commands
1. View network information
ipconfig # see IP The basic information of the address
ipconfig /all # see IP Address details 2. Test network connectivity
ping The goal is ip Address # Test network connectivity , You can communicate whenever you go back , Default send 4 A package
ping -t The goal is ip Address # Send test packages continuously
ping -n Number The goal is ip Address # Appoint ping The number of bags
3. Resolve the domain name manually
nslookup domain name # Resolve the domain name manually
边栏推荐
- 从暴力递归到动态规划,记忆化搜索
- Poj2308 continuously look at dfs+bfs+ optimization
- What are the methods of knowledge map relation extraction
- 阿里云SSL证书
- VC prompts to recompile every time you press F5 to run
- JUC concurrent programming - Advanced 05 - lock free of shared model (CAS | atomic integer | atomic reference | atomic array | field updater | atomic accumulator | unsafe class)
- CA证书制作实战
- "Fundamentals of program design" Chapter 10 function and program structure 6-13 divide and conquer method to solve the gold bullion problem (20 points)
- 洛谷 P2024 [NOI2001] 食物链
- From Fibonacci sequence to matrix fast power technique
猜你喜欢

AC automata

PCL点云处理之平面规则化(五十五)

From Fibonacci sequence to matrix fast power technique

QT6 with vs Code: compiling source code and basic configuration

Morris遍历

VScode默认输出到调试控制台如何调整到终端以及两者中的乱码问题

单调栈结构练习——子数组最小值的累加和

Background image and QR code synthesis

A compatible, smaller and easy-to-use web font API

老杜Servlet-JSP
随机推荐
Implementation of graph structure, from point to edge and then to graph
The rule created by outlook mail is invalid. Possible reasons
Push information to wechat through enterprise wechat self built application
Enterprise operation we media can't "self Hi": the content should be grounded, not advertising
Let‘s Encrypt
《ArchSummit:珍爱微服务底层框架演进》
What do GB, MB and KB mean respectively. What are the sizes
First engineering practice, or first engineering thought—— An undergraduate's perception from learning oi to learning development
背景图和二维码合成
From violent recursion to dynamic programming, memory search
PCL点云处理之平面规则化(五十五)
Projection regularization of line point set in PCL point cloud processing (56)
Let‘s Encrypt
What are the methods of knowledge map relation extraction
VScode默认输出到调试控制台如何调整到终端以及两者中的乱码问题
聊聊 Redis 是如何进行请求处理
PCL点云处理之均匀采样抽稀(六十一)
Error connecting MySQL database with kettle
[database learning] redis parser & single thread & Model
Background image and QR code synthesis