当前位置:网站首页>Introduction to digital signature technology
Introduction to digital signature technology
2022-07-24 01:23:00 【Little ash of the prairie】
- digital signature ( Also known as public key digital signature ) Only the sender of information can produce a digital string that others can't forge , This digital string is also an effective proof of the authenticity of the information sent by the sender . Digital signature is the application of asymmetric key encryption technology and digital digest technology
- Digital signature mechanism is one of the means to ensure the security of network information , Sure Solve forgery 、 Deny 、 Impersonation and tampering problems . One of the purposes of digital signature is to replace the traditional manual signature and seal in the network environment , It plays an important role
- Digital signature in modern times web It is of great significance in business . Most countries have regarded digital signature as an authorization mechanism with the same legal effect as manual signature .
Introduction to the principle of digital signature
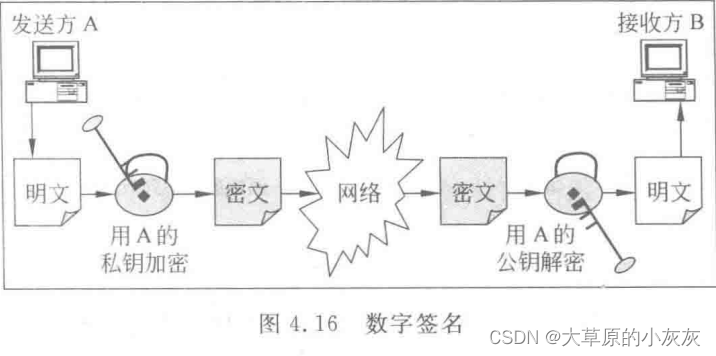
- The sender A Use the private key to encrypt the information ( Also called signature ), Get the ciphertext ( It's also called digital signature ).
- The receiving party B After receiving the ciphertext , Use public key to decrypt ( Also called signature verification ), Get the original .
- We know , In theory, anyone can get the public key . If C Get A The public key , that C Intercepted ciphertext information , Is it possible to decrypt information directly . Here we will talk about the role of digital signature , Digital signatures are not intended to encrypt data , But to make sure that the information is indeed A Emitted , And the information has not been tampered . hypothesis C I forged a set of data , however C No, A The private key , Therefore, you cannot encrypt your forged data , perhaps C Encrypt data with your private key , Send to B,B It can't be decrypted . therefore B I know the news is not A Emitted . hypothesis C Intercepted A Ciphertext sent , Tampered with the ciphertext ,B Also cannot decrypt . therefore , as long as B The message is received and can be decrypted successfully , that B You can be sure , The message is indeed A Sent and the message has not been tampered .
The practical application
- The application of digital signature technology in practice is introduced below .
1 Summary of calculation
- The sender A Use a digest algorithm for messages M Make a summary calculation , Get a summary of the news (MD1)

2 Signature
- The sender A Encrypt the message digest with the private key , Get a digital signature (DS)

3 Send a message
- The sender A The message is M And digital signatures (DS) Send it to the receiver together B

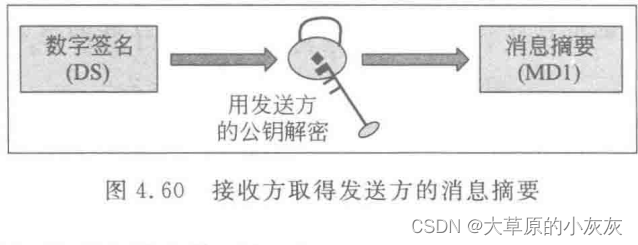
4 The receiver calculates the message digest
- B Received a message M And digital signatures (DS) after , First, use the same message summarization algorithm to summarize messages M Make a summary , Get a summary of the news (MD2).

5 The receiver's signature
- The receiving party B Decrypt the digital signature with the sender's public key ( Also called signature verification ). obtain MD1.
6 Compare and verify
- B Compare the message summary obtained from the signature verification MD1 And the message summary calculated by summarizing the original message MD2 Are they the same? . If the same , The information is really A Sent without tampering .

边栏推荐
- 为什么博途V17及以下的HMI面板不能与1500固件版本2.9或1200版本4.5 的CPU建立连接?
- Linkerd service grid survey notes
- Kotlin基础从入门到进阶系列讲解(基础篇)关键字:suspend
- C语言力扣第53题之最大子数组和。动态规划与分治
- c语言支持yaml配置文件通用方法
- kubernetes 部署 dashboard(可視化界面)
- Sublime text 3 Chinese + add common plug-ins
- Idea compiler sets the separation line between methods
- SQL CASE 多条件用法
- Description of TCP packet sticking problem code
猜你喜欢
数仓搭建——ODS层

OSI、TCP/IP(A1)

Redis - configuration and Application

SCM learning notes 8 -- keys and external interrupts (based on Baiwen STM32F103 series tutorials)

数字化转型时代的企业数据新基建 | 爱分析报告

Basic use of crawler requests module

Easyexcel export case (only you can't think of it)

LVS load balancing scheduling principle and configuration method

HCIP第三天笔记

面试了二三十家公司所总结的问题,Android面试吃完这一套没有拿不到的Offer......
随机推荐
HCIP第二天笔记
How to solve cnpm stuck during execution?
Skywalking distributed system application performance monitoring tool - upper
Detailed explanation of OSPF in hcip
Free learning machine learning transaction resources
复制可读路径不好使
HCIP,OSPF综合实验
HCIP第六天_特殊区域综合实验
SCM learning notes 1 -- data download and environment construction (based on Baiwen STM32F103 series tutorials)
Redis - basic concept
MGRE experiment
Linkerd service grid survey notes
Notes: binary tree pruning (recursion, iteration)
Explanation of terms in Polymer Physics
How safe is Volvo XC90? 5 seats and 7 seats are available
B tree and b+ tree
C language database: detailed description. Use the student management system to understand the operation of the database, which is simple and easy to understand.
LVS load balancing scheduling principle and configuration method
Hypothesis test of Pearson correlation coefficient
OSPF(第四天笔记)