当前位置:网站首页>Network security - Web penetration testing
Network security - Web penetration testing
2022-07-24 13:34:00 【Beluga】
Web Penetration test
First step , Open the network topology , Start the experimental virtual machine , View the virtual machines separately IP Address :
Kali Linux

Linux 
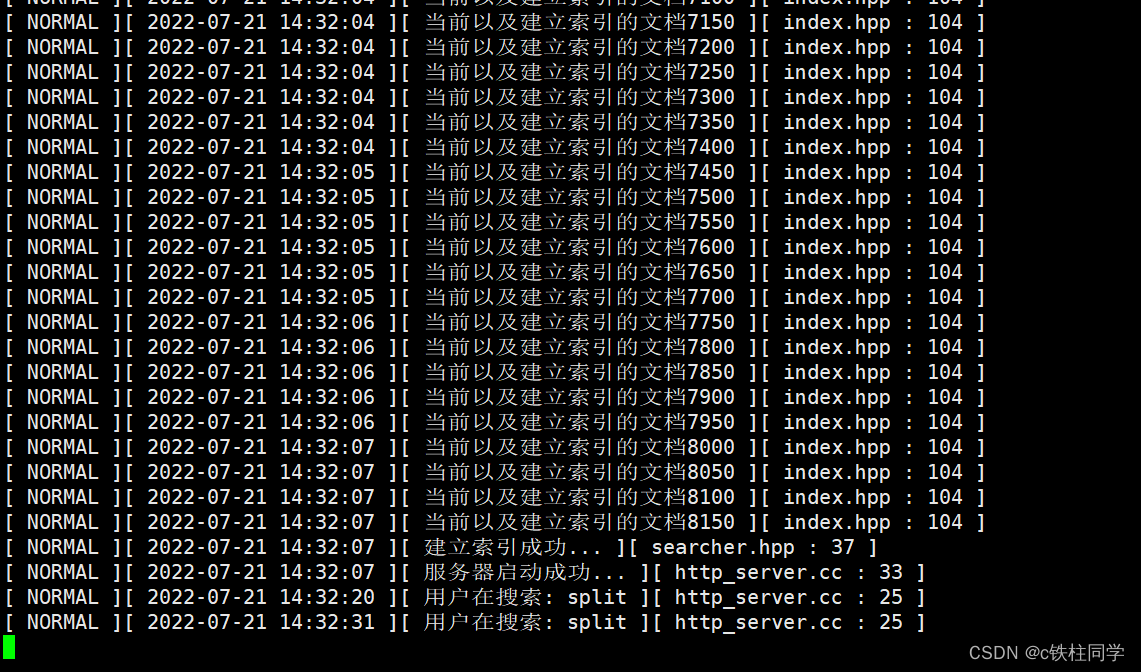
1. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Penetration test ( Using tools w3af Target of Web Server for auditing ), stay w3af Under the command line interface of , Use the command to list all plug-ins for auditing , Use the command used for this operation as Flag Value submission ;
Get into Kali Linux Commands used in the command console w3af_console Get into w3af Command line mode , By entering the command “plugins” Configure the plug-in , Reuse command list audit You can list all audit modules

Flag:list audit
2. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Penetration test , Using tools w3af Yes Web Server for auditing , stay w3af The crawling module is loaded under the command line interface of phpinfo Information and spider crawling data , Use the command used for this operation as Flag Value submission ;
Use command crawl phpinfo web_spider Load crawling module
![]()
Flag:crawl phpinfo web_spider
3. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Penetration test , Using tools w3af Yes Web Server for auditing , stay w3af Enable the audit plug-in in the command line interface of :sql Blind note 、 Command injection and sql Inject to test the security of the server website , And use the command used for this operation as Flag Value submission ;
Use command audit blind_sqli os_commanding sqli call sql Blind note 、 Command injection and sql Injection module
![]()
Flag:audit blind_sqli os_commanding sqli
4. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Penetration test , Using tools w3af Yes Web Server for auditing , stay w3af Set the target server address to start scanning in the command line interface of , Use the fixed string in the command for this operation Flag Value submission ;
Use command “back” Return to the initial menu , Then use the command target Enter target ip Configuration interface , Set the target ip

Flag:set target
5. In infiltration machine Kali Linux View the audit results in , The audit results contain loopholes URL Address as Flag value ( When submitting answers IP use 192.168.80.1 Instead of , for example http://192.168.80.1/login.php) Submit ;
return w3af Console initial menu , Use command start Start detection

According to the echo result , Find out http://172.16.1.200/checklogin.php Page exists SQL Inject holes
Flag:http://192.168.80.1/checklogin.php
6. In the 5 Based on the question , Get into exploit Pattern , load sqlmap The module is used to SQL Injection test , Load sqlmap The module is used to SQL The commands that need to be used for injection testing are Flag Value submission ;
Use command exploit Enter the utilization module , And then call sqlmap The module injects

Flag:exploit sqlmap
7. Through the infiltration machine Kali Linux Target machine Linux Conduct SQL Injection test , Take the name of the last database as Flag Value submission ;
According to the echo result , Use command “interace 0” Activate shell conversation 
Enter the command dbs Export all database names in the target target database

Flag:mysql
8. Through the infiltration machine Kali Linux Target machine Linux Conduct SQL Injection test , In the database form root The user's password is used as Flag Value submission .
Enter the command dump Export the form contents in the target target database

Flag:v5a4r8e2w5u9
边栏推荐
- 汉字风格迁移篇---无监督排版传输
- 登临科技联合创始人王平:创新+自研“双核”驱动,GPU+赋能AI落地生根|量子位·视点分享回顾...
- Make a fake! Science has exposed the academic misconduct of nature's heavy papers, which may mislead the world for 16 years
- hdparm
- 支持鹏程系列开源大模型应用生态演化的可持续学习能力探索
- 有好用的免费的redis客户端工具推荐么?
- Research and progress of traffic situation awareness based on social media data enhancement
- 基于ABP实现DDD--实体创建和更新
- How can flinksql run in perjob mode on yarn? I submit tasks on SqlClient
- flow
猜你喜欢

Go deadlock problem

Bayesian width learning system based on graph regularization

Make a fake! Science has exposed the academic misconduct of nature's heavy papers, which may mislead the world for 16 years

Data + AI Summit 2022 PPT 下载

汉字风格迁移篇---无监督排版传输
基于boost库的搜索引擎
Experience sharing | how to use SaaS for enterprise knowledge management
How to quickly learn Embedded

EAS environment structure directory

About thread (3) thread synchronization
随机推荐
Implementation of dynamic columns in EAS BOS doc list
Packaging class (mutual conversion between types)
浅谈Node Embedding
ICML2022 | 分支强化学习
WSDM 22 | 基于双曲几何的图推荐
Embedded cognitive network card PHY self negotiation
网络安全——Web渗透测试
Two stacks implement one queue
Summary of embedded network problems (packet loss of network card, unrecognized network card)
Integer inversion of force deduction questions
Icml2022 | branch reinforcement learning
Odoo+ test
About the concept of thread (1)
Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation
Atcoder beginer contest 261 f / / tree array
脑注意力机制启发的群体智能协同避障方法
Detailed tutorial of ettercap
Aggregation measurement of robot swarm intelligence based on group entropy
Modern data architecture selection: Data fabric, data mesh
Go redis pipeline application