当前位置:网站首页>Revil - blackmail Virus Emergency Response
Revil - blackmail Virus Emergency Response
2022-06-23 17:52:00 【Khan security team】
The load name is AnalysisSession1 Of Mandiant After analyzing the file , I navigate to “ Analyze the data > user ” To identify the different users present on the infected host . Here I can see the full name of the employee :
2. What is the operating system of the infected host ?
To find the operating system of the infected host , We can navigate to “ Analyze the data > system information ” And view the operating system information :
3. What is the name of the malicious executable opened by the user ?
According to the title of the room and the description of the challenge , The infected host appears to have been REvil Ransomware infection . I did some research on the Internet , I found the Secureworks This article of :
REvil/Sodinokibi Blackmail Software
author : Anti threat unit research group REvil( Also known as Sodinokibi) Extortion software in 4 month 17 It was first discovered on the th ......
Read through this article , I have learned that , As part of ransomware delivery , Threat actors use strategic networks to invade (SWC) By destroying Italy WinRAR Website and replace with malware instances WinRAR Install the executable to deliver REvil .SWC This leads to an unsuspecting WinRAR Infection of the customer system .
stay Redline in , I navigate to “ Analyze the data > file system ”, Found the... Opened by the user WinRAR Malicious executable :
4. The integrity that users access when downloading malicious binaries URL What is it? ?( Also includes binaries )
stay Redline in , I navigate to “ Analyze the data > File download history ” And find out what to use to download malicious binaries file Source URL:
5. The binary MD5 What is the hash value ?
To find malice WinRAR Binary files MD5 Hash , We can navigate to Redline Medium “ Analyze the data > file system ”, Then double click. WinRAR Entry for more details , For example, its file hash :
6. How many kilobytes is the size of the binary file ?
To find malice WinRAR File size of binary file , We can navigate to Redline Medium “ Analyze the data > file system ”, Then double click. WinRAR Entry for more details , For example, file size :
7. What is the extension for renaming user files ?
According to the above SecureWorks article ,REvil Check Software\recfg Whether there is... In the registry key rnd_ext value . This value contains the... Generated at run time Attach to encrypted file Of Random extension . If this registry value does not exist , The malware will generate a small letter (az) And number (0–9) A random string of components , The length range is 5 To 10 Characters ( contain ), And begin with a period ( for example ,.9781xsd4).
stay Redline in , I navigate to “ Analyze the data > file system ” And see a random file extension , Similar to the above description and example :
8. What is the number of files renamed and changed to this extension ?
To confirm rename and change to problem 7 Number of files with extensions determined in , I navigate to “ Analyze the data > Timeline ” And filter the extension in the summary column :
9. What is the full path of the wallpaper changed by the attacker , Include image name ?
Reference resources SecureWorks, If the encryption process is successful ,REvil Will change the desktop background , Make the victim aware of the threat .REvil Use a random file name to save the image to the host %Temp% Directory , The file name consists of a length of 3 To 13 Characters of lowercase letters and numbers , And add “ .bmp ” Extension ( for example ,C:\Users\ <user> \AppData\ Local \Temp\cd2sxy.bmp).
stay Redline in , I navigate to “ Analyze the data > Timeline ”, Then filter any with .bmp File with extension . I found one with SecureWorks The description provided matches the file :
10. The attacker left a note for the user on the desktop ; Provide a comment name with an extension .
stay Redline in , I navigate to “ Analyze the data > file system ”, Discover the notes left by the attacker on the user's desktop :
11. The attacker is C:\Users\John Coleman\Favorites\ I created a “Links for United States” Folder , And left a file there . Provide file name .
stay Redline in , I navigate to “ Analyze the data > file system ”, stay “ C:\Users\John Coleman\Favorites\ ” The file left by the attacker was found under :
12. Create a on the user's desktop 0 Hidden file of bytes . Provide the name of the hidden file .
stay Redline in , I navigate to “ Analyze the data > file system ” And search for a 0 Byte file :
13. The user downloaded a decryptor , Hope to decrypt all files , But failed . Provides the... For decrypting files MD5 Hash value .
stay Redline in , I navigate to “ Analyze the data > file system ” And see a name “decryp.tor.exe” The file of . I double-click the entry and see MD5 Hash :
14. In the ransomware description , The attacker has provided a... That can be accessed through a normal browser URL, To decrypt one of the encrypted files for free . The user tried to access it . Provide complete URL route .
Read through SecureWorks article , The ransom note instructs the victim to use Unique URL To decrypt their files . The website provides trial decryption to prove that the victim can decrypt the file , As shown in the figure below :
Look at the image , I can see “ Decryptor ” The word is used as the only URL Part of . stay Redline in , I navigate to “ Analyze the data > Browse URL Historical record ” And filter keywords “ Decryptor ”:
15. What are the three names associated with malware that infects this host ?( Enter names in alphabetical order )
I already know that the host has been REvil Blackmail attacks
边栏推荐
- 混沌工程在云原生中间件稳定性治理中的实践分享
- Intel arc A380 graphics card message summary: the entry-level price products of running point and bright driving need to be optimized
- January 5, 2022: there are four kinds of rhythms: AABB, ABAB and ABB
- [go] calling Alipay to scan code for payment in a sandbox environment
- Interpretation of eventbus source code
- 解答03:Smith圆为什么能“上感下容 左串右并”?
- C. Product 1 Modulo N-Codeforces Round #716 (Div. 2)
- AMQP协议
- QT当中的【QSetting和.ini配置文件】以及【创建Resources.qrc】
- Best practices cloud development cloudbase content audit capability
猜你喜欢
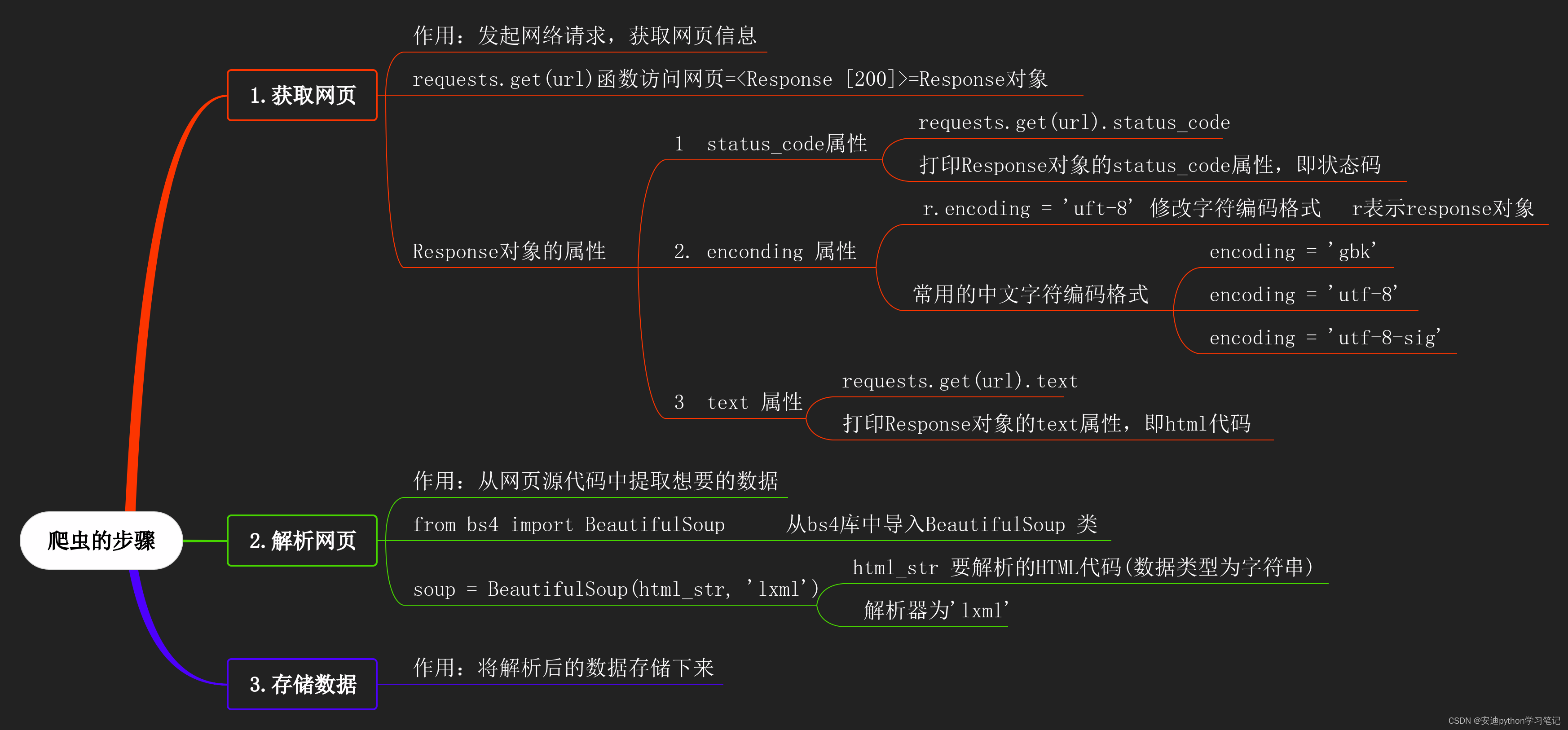
12 initialization of beautifulsoup class

美团三面:聊聊你理解的Redis主从复制原理?

Performance test bottleneck tuning in 10 minutes! If you want to enter a large factory, you must know

Self supervised learning (SSL)

What does the timestamp 90K mean?

Date selection of hotel check-in time and check-out time

qYKVEtqdDg

Wechat applet: time selector for the estimated arrival date of the hotel

Robot Orientation and some misunderstandings in major selection in college entrance examination

【网络通信 -- WebRTC】WebRTC 源码分析 -- 接收端带宽估计
随机推荐
[go]沙盒环境下调用支付宝扫码支付
Codeforces Round #620 (Div. 2)ABC
How to use JSON data format
C. Phoenix and Towers-Codeforces Global Round 14
qYKVEtqdDg
Redis ubuntu18.04.6 intranet deployment
Method of copying web page content and automatically adding copyright information (compatible with ie, Firefox and chrome)
Spdlog logging example - create a logger using sink
Li Kou daily question - day 25 -495 Timo attack
Kdevtmpfsi processing of mining virus -- Practice
Petitpotam – NTLM relay to ad CS
Tencent Qianfan scene connector: worry and effort saving automatic SMS sending
[untitled] Application of laser welding in medical treatment
Three functional forms of intelligent switch
History of storage technology: from tape to hardware liquefaction
创新技术领航者!华为云GaussDB获颁2022年云原生数据库领域权威奖项
浅谈5类过零检测电路
10分钟后性能测试瓶颈调优!想进大厂这个必须会
Intranet penetration token stealing
Réponse 02: pourquoi le cercle Smith peut - il "se sentir haut et bas et se tenir à droite et à droite"?