当前位置:网站首页>RHCE first operation
RHCE first operation
2022-07-24 13:43:00 【bear(emo)】
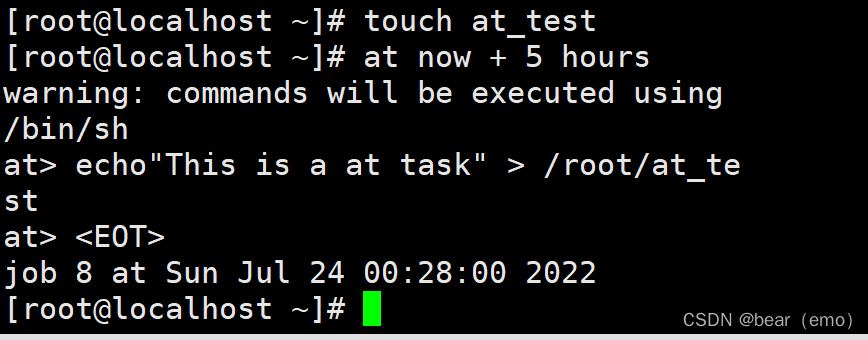
1.at Configure in 5 Hours later, , take "This is a at task" write in root Home directory at_test In file
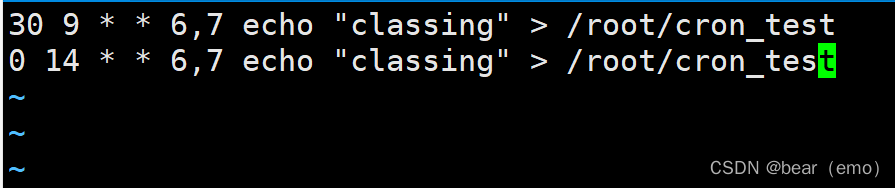
2.crontab To configure , Every Saturday , Sunday 9 Half past six ,14 spot Remind me to go RHCE course write in root Home directory cron_test In file

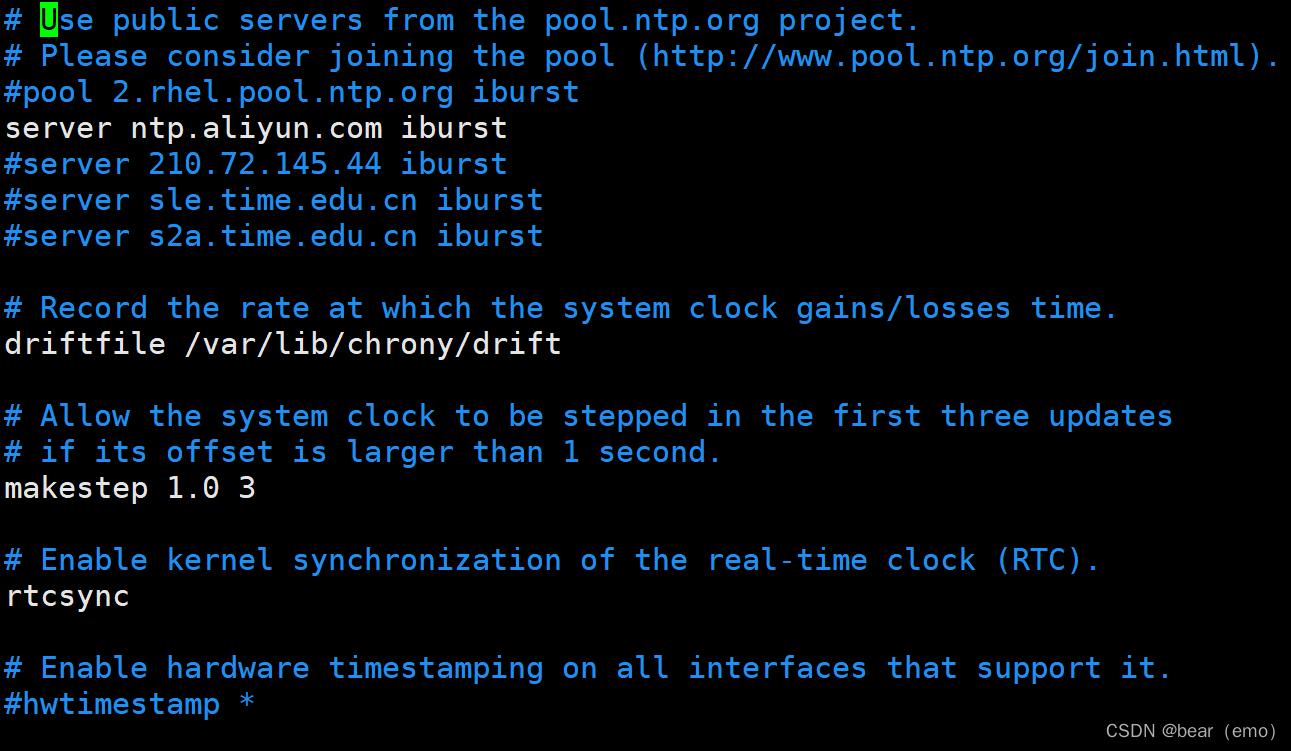
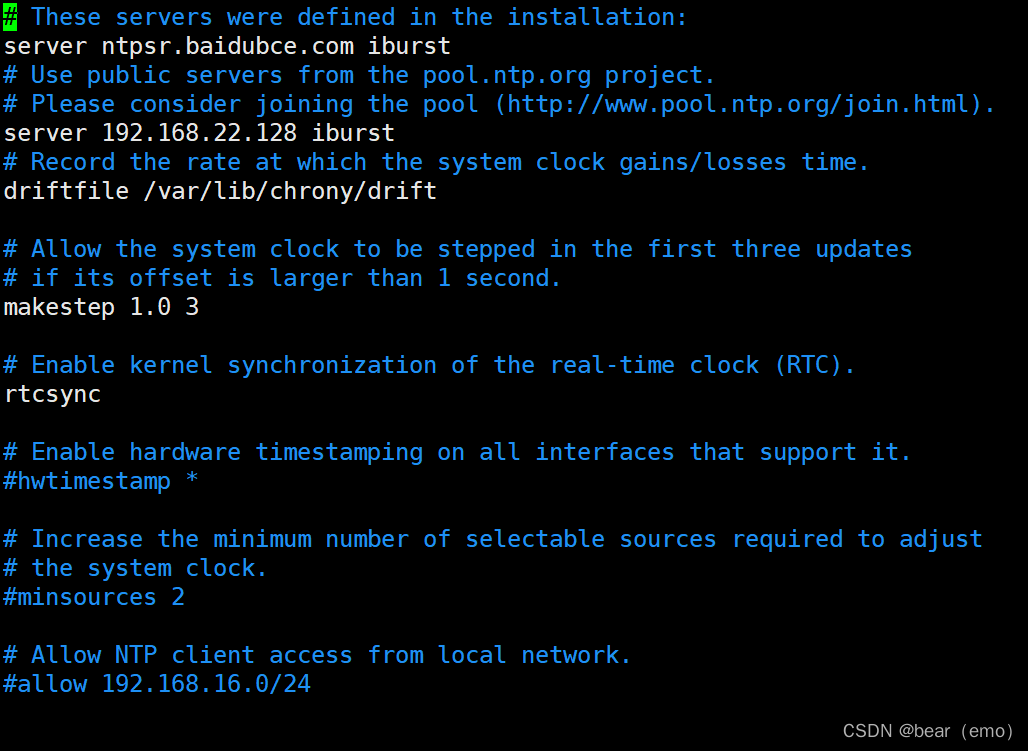
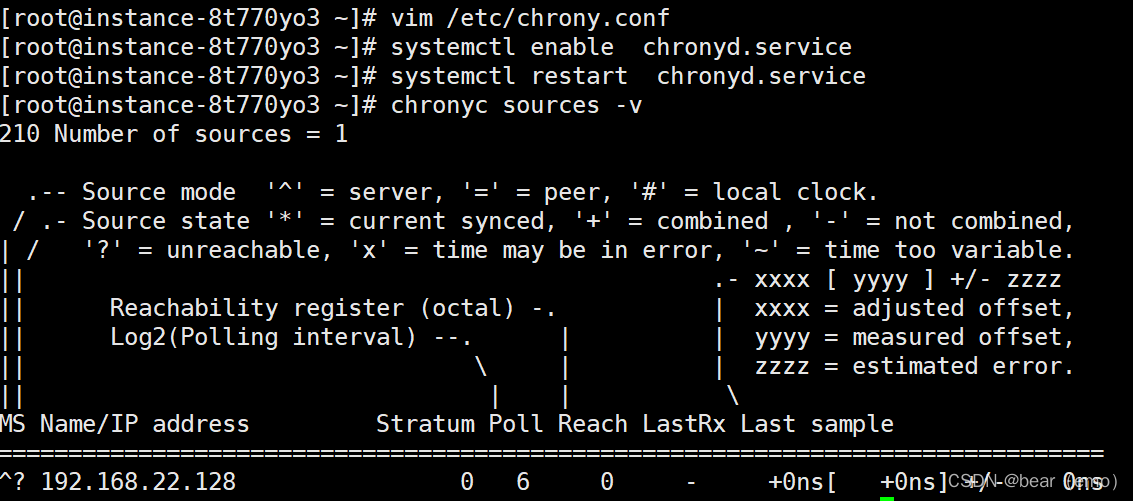
3. On two Linux Upper Department chrony service : requirement : The first one synchronizes the time from Alibaba cloud server , The second synchronizes the time from the first





4. What is symmetric encryption , What is asymmetric encryption , What are the encryption algorithms of symmetric encryption , What encryption algorithms are needed for asymmetric encryption
Symmetric encryption It means that both encryption and decryption use the same key , The asymmetric key is a pair of keys It consists of public key and private key
Symmetric key Compared with asymmetric key encryption, it is faster , But the security is not as good as asymmetric key , Asymmetric keys ensure a certain degree of security , But the identity of the other party cannot be confirmed , There are also risks .
Symmetric encryption algorithm :DES encryption 、 Information verification code 、AES encryption 、 triple ·DES
Encryption algorithm of asymmetric encryption :RSA、Elgamal、 Knapsack algorithm 、Rabin、D-H、ECC Elliptic curve encryption algorithm
边栏推荐
- Simple use and difference of symmetric res, AES and asymmetric RSA (JWT)
- Flink综合案例(九)
- Detailed explanation of odoo JS DoAction
- Chinese character style migration --- diversity regularization stargan for Chinese character multi font generation
- Flex layout
- Atcoder beginer contest 261 f / / tree array
- Network security - error injection
- Paper notes: swing UNET: UNET like pure transformer for medicalimage segmentation
- Network security - Cookie injection
- 基于社会媒体数据增强的交通态势感知研究及进展
猜你喜欢

基于典型相关分析的多视图学习方法综述

网络安全——Web渗透测试

Network security - Web information collection

WSDM 22 | graph recommendation based on hyperbolic geometry
网络安全——服务漏洞扫描与利用

论文笔记:Swin-Unet: Unet-like Pure Transformer for MedicalImage Segmentation

Network security - file upload blacklist bypass

Network security - file upload competitive conditions bypass

Simulate the implementation of the library function memcpy-- copy memory blocks. Understand memory overlap and accurate replication in detail

从云原生到智能化,深度解读行业首个「视频直播技术最佳实践图谱」
随机推荐
Aggregation measurement of robot swarm intelligence based on group entropy
软链接、硬链接
Overview of multi view learning methods based on canonical correlation analysis
rhce第一次作业
Data formatting widget
Mongodb uses mongotemplate operations to add, delete, modify, query, page, sort, aggregate (including embedded data), file upload and download
网络安全——Web渗透测试
开放环境下的群智决策:概念、挑战及引领性技术
How to configure webrtc protocol for low latency playback on easycvr platform v2.5.0 and above?
The gather function of tidyr package of R language converts a wide table into a long table (a wide table into a long table), the first parameter specifies the name of the new data column generated by
Network security - penetration using evil maid physical access security vulnerabilities
Adjust the array order so that odd numbers precede even numbers
Mass data excel download - the author of this article only tried to download 510000 data, which took 7 seconds
22-07-23周总结
From cloud native to intelligent, in-depth interpretation of the industry's first "best practice map of live video technology"
Network security - file upload whitelist bypass
申请了SSL数字证书如何进行域名验证?
数据类型二进制字符串类型
脑注意力机制启发的群体智能协同避障方法
Kunyu(坤舆) 安装 详解