当前位置:网站首页>Network security - Web information collection
Network security - Web information collection
2022-07-24 13:34:00 【Beluga】
Web information gathering
First step , Open the network topology , Start the experimental virtual machine , View the virtual machines separately IP Address :
Kali Linux

Linux

1. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Scanning penetration test ( Using tools Nikto, View the complete help file for this command ), And the operation uses the fixed string in the command as Flag Value submission ;
Command view Nikto Complete help file for the tool

Flag:nikto -H
2. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Scanning penetration test ( Using tools Nikto, Scan target server 80 port , Detect its open state ), And regard all commands to be used in this operation as Flag Value submission ( The destination address is in http://10.10.10.1 To express );

Flag: nikto -host http://10.10.10.1
3. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Scanning penetration test ( Using tools Nikto, Scan target server 80 port ), Echo information to Apache The version number of the service is used as Flag Value submission ;
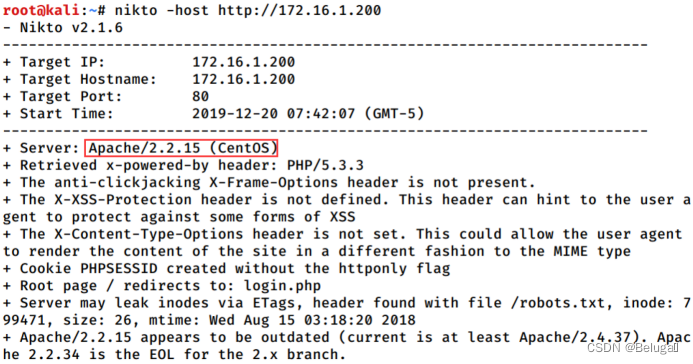
Flag:2.2.15
4. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Scanning penetration test ( Using tools Nikto, Scan target server 80 port ), Echo information to PHP The version number of is used as Flag Value submission ;

Flag:5.3.3
5. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Scanning penetration test , Using tools Nikto And combine Nmap Scan according to the scanning results , use first Nmap The effect of the tool on the network segment where the target is located 80 Port scan , And output the scanning results to the specified file in all formats target in , Take the parameters needed for outputting all formats as Flag Value submission ;

Flag:oA
6. Through the infiltration machine Kali Linux Target machine Linux Conduct Web Scanning penetration test , Using tools Nikto Generated by scanning question 5 target Web site in file , And all commands used in this operation are regarded as Flag Value submission .
Since all formats are output in question 5 to target in , The following three files will be generated under the execution path ,

Then directly call the suffix .gnmap Is ok

Flag:nikto -host target.gnmap
End of experiment , Shut down the virtual machine .
边栏推荐
- Sorting method: bubble sorting (use an array to arrange a string of numbers in order (from large to small or from small to large))
- 群体知识图谱:分布式知识迁移与联邦式图谱推理
- LEADTOOLS 22 套件 LEADTOOLS 超级套
- vscode配置用户代码片段(包括删除方法)
- An example of how to save various data types by using esp32 EEPROM library functions under Arduino framework
- 【论文阅读】Mean teachers are better role models
- Odoo+ test
- Interface document evolution atlas, some ancient interface document tools, you may not have used them
- 汉字风格迁移篇---无监督排版传输
- 游戏思考04总结:针对帧、状态、物理同步的总结(之前写的太长,现在简略下)
猜你喜欢

网络安全——Web渗透测试

How to draw Bezier curve and spline curve?
基于boost库的搜索引擎

【论文阅读】TEMPORAL ENSEMBLING FOR SEMI-SUPERVISED LEARNING

Digital intelligence integration accelerates enterprise business innovation
LEADTOOLS 22 套件 LEADTOOLS 超级套

Activity start (launchactivity/startactivity)_ (1)_ WMS of flow chart

Search engine based on boost library

Thread multithreading

Redis(13)----浅谈Redis的主从复制
随机推荐
基于社会媒体数据增强的交通态势感知研究及进展
About thread (4) thread interaction
selenium环境配置和八大元素定位
基于典型相关分析的多视图学习方法综述
Implementation of dynamic columns in EAS BOS doc list
Sorting method: bubble sorting (use an array to arrange a string of numbers in order (from large to small or from small to large))
How to quickly learn Embedded
Common doc commands
The core capability of accelerating enterprise data application innovation flexibility
Repair the problem of adding device groups and editing exceptions on easycvr platform
Vscode configuration user code snippet (including deletion method)
Win10 log in with Microsoft account and open all programs by default with administrator privileges: 2020-12-14
现代数据架构选型:Data Fabric、Data Mesh
编写浏览器插件
Atcoder beginer contest 261e / / bitwise thinking + DP
HCIP第十三天
Bayesian width learning system based on graph regularization
户外广告牌不能“想挂就挂”!广州城管部门加强户外广告安全管理
Research on data governance quality assurance
Common OJ questions of stack and queue