当前位置:网站首页>Design scheme of authority management of fusion model
Design scheme of authority management of fusion model
2022-06-25 00:14:00 【ByteDance technical team】
Focus on Dry goods don't get lost
A term is used to explain
ITAM:ITAM It's right IT Office assets -- Physical assets ( Like a laptop )、 Software assets ( Such as Office365)-- A system for life cycle management .
ITAM-Auth:ITAM Authentication service of the system .
ITAM-Data:ITAM Data service of the system .
SaaS: Software as a service ( English :Software as a Service, abbreviation :SaaS), A software delivery model . In this delivery model , The software only needs to go through the network , It can be used without traditional installation steps , The software and its related data are centrally hosted in cloud services .
ServiceNow:ServiceNow Is an American software company , Headquartered in Santa Clara, California , The company has developed a cloud computing platform , Help enterprises manage their enterprises IT workflow .ServiceNow By Fred · Ludiyu 2003 Founded in 2000 , Listed on the New York Stock Exchange , It's Russell 1000 Index and S & P 500 The constituent stocks of the index .2018 year ,《 Forbes 》 The magazine named it the first most innovative company in the world .
background
This scheme combs the mainstream permission models in the industry ,IT Saas The problems to be solved by the authority management in the process of virtualization , Reference is made to both inside and outside the company 、 Some authority design schemes at home and abroad , combination RBAC、ABAC The model proposes ITAM Fusion model permission management scheme .
The mainstream permission model
After referring to the permission implementation of multiple systems , Summarize the public authority theory model , Specific to the implementation of each system, there will be some transformation and optimization , This section introduces the permission model widely used in industry .
summary
The main body : The initiator of an access behavior , Here to simplify the understanding , Assume that all users
object : The object to which the access behavior is imposed , Pages such as 、 function 、 data

ACL (Access-Control List Access control list )
Subject: The main body , Visitors , It can be a person or a system 、 Equipment etc.
Action: Specific actions of access , Such as Create、Read、Edit...
Object: object , The visited party , It can be an entry in the system 、 A file, etc
A basic authority control mechanism , Simple and direct , It is often applied to file systems in operating systems .

MAC (Mandatory Access Control Enforce access control )
Subject: The main body , Visitors , It can be a person or a system 、 Equipment etc.
Action: Specific actions of access , Such as Create、Read、Edit...
Object: object , The visited party , It can be an entry in the system 、 A file, etc
Attributes: stay Subject and Object There may be more than one Attributes , Metadata used for authentication judgment
The subject and the object will be given a level of confidentiality respectively , Two way check whether the levels of subject and object match during access , It is often used in fields with high security requirements , Like the military 、 Finance 、 The government 、 Computer system security, etc , When two-way authentication is performed, follow authorization rule, The rule The storage location and management of are usually very strict .

DAC (Discretionary Access Control Autonomous access control )
Subject: The main body , Visitors , It can be a person or a system 、 Equipment etc.
Action: Specific actions of access , Such as Create、Read、Edit...
Object: object , The visited party , It can be an entry in the system 、 A file, etc
Grant: Delegation of authority ,Subject 1 But for Object To perform in whole or in part Action Sublicense to Subject 2
Autonomous access control is simply understood as permission Subject You can transfer your own permissions to other principals , It is usually to solve the problem of flexibility of permission allocation , But in B End systems often don't just use DAC This is a permission model ( For example, it will combine MAC Model ), Because this model will lead to permission diffusion beyond the control of the administrator .

RBAC (Role Based Access Control Role access control )
RBAC The essence of authority is Who Yes What the How operation
User: The main body , Visitors , Represent users in the system , But it can also be a machine 、 Network, etc - Who
Object: object , The visited party , It can be a menu in the system 、 Button 、 Data records 、API etc. - What
Operation: An action that a user can perform in a system - How
Permissions: jurisdiction , The representative may refer to RBAC Under the protection of Object perform Operation (What + How)
Role: role , It represents some responsibilities within the organization and the users under this responsibility have certain specified permissions
Session: conversation , The session is triggered by a user , Simultaneous session activates one or more... Associated with the session Role
This article focuses on being INCITS( International Information Technology Standards Committee ) Adopted standards RBAC Model
standard RBAC It is divided into 4 Submodel :
RBAC0 - Core RBAC

RBAC1 - Hierarchical RBAC

General inheritance : The inheritance between roles is an absolute partial order ( Directed acyclic , Circular role inheritance is meaningless ), This design is more free than a single tree inheritance , It is applicable to permission scenarios where role permissions have inheritance requirements but are not strictly related to upper and lower levels .


RBAC2 - Constrained RBAC

RBAC3 = RBAC 1 + RBAC 2
RBAC3 yes RBAC1 and RBAC2 A collection of , It includes both role inheritance and related constraints .
advantage : The most powerful .
shortcoming :4 The most complex of the models , Management costs are high .
Overall ,RBAC It is considered to satisfy three important authority principles :
Minimum permissions : Users only get their roles when the session action is triggered , This role defines the minimum permissions required to complete the action .
Permission abstraction : Specific permission behaviors can be abstracted in combination with business , Such as making comments 、 Upload attachments , Not simply read 、 Write 、 check .
Separation of duties : The role itself represents the responsibility , add RBAC Support the mutual exclusion mechanism between roles , Divide and conquer high-risk actions .
To the standard RBAC An extension of
The administrative cost of authorizing to a single user : You can skip Role Authorize users directly
Management cost for mass user authorization :Group Can also be assigned to Role in
Maintenance oriented Role The cost of management : The user is in Role Permission clipping is available in ( On behalf of this user, only this Role Part of the permissions for )、 Replicable Role wait
And other permission models :
and DAC 、MAC The combination of
and ABAC The combination of
ABAC (Attribute Based Access Control Property access control )
Subject: The main body , Visitors , Represent users in the system , But it can also be a machine 、 Network, etc
Object: object , The visited party , It can be a file in the system 、 equipment 、 Database records, etc
Operation: The function of the subject in the system to execute the request of the object / Behavior , May include read、write、edit、delete etc.
Attributes: attribute ,Subject、Object、Operation and Environment Condition All have attributes , Property is a pair of key values
Policy: A series of rules or relationships consisting of attributes and attribute values , Through the rule / Relationships determine whether an access is allowed
Environment Conditions: Identifiable environmental conditions , The context in which the access behavior occurs , It can usually be time 、 place 、IP、 equipment 、 operating system 、 Risk level, etc
ABAC It's based on Subject attribute 、Object attribute 、 Environment attributes and access Policy Fine grained permission control over ,ABAC Only those that conform to specific properties can be achieved Subject Under certain conditions, it can be used for Object Execute a permission action .

Next generation permission model exploration - NGAC
stay DAC、MAC、RBAC、ABAC Beyond these mainstream permission models , There are a number of other permission models ( Such as LBAC、GBAC、CBAC、OrBAC、RAdAC...), But at present, no permission model has been widely adopted by the industry .
Academic circles have already made some research achievements on the next generation permission model .
NIST( National institute of standards and technology ) stay 2019 It was proposed that NGAC(Next Generation Access Control Next generation access control model ), It is proposed that this is a new model that is different from the existing permission model and can be widely compatible with various permission scenarios in the current digital ecosystem .
It looks more like RBAC Thinking and ABAC Combination of ideas , The combination point is user —— Role relationships are no longer artificially assigned , But according to Policy Automatically assigned , When the user performs permission behavior as a role, go over it again ABAC The rule of judgment .
Typical application scenarios :Alice Only on weekday mornings 10:00-18:00 Under the office network in London (role-based permission policy) In order to access and modify the data in the order system in the role of finance (role-based permission policy)

Conclusion

No permission model is perfect , What matters is how to integrate with the business , Consider security 、 Extensibility 、 flexibility 、 Ease of use 、 Administration cost 、 Compliance and other factors are balanced , This process is often the most complicated .
Scheme reference
With these goals , Mainly look at it. ServiceNow Permission implementation scheme of , From the basic idea 、 Design can be used for reference 、 The disadvantages of the scheme are analyzed as follows .
ServiceNow
The basic idea
ServiceNow Permission management adopts RBAC1+ACL The way ,ACL control ObjectType Of Operation visit , adopt Role、Condition、Script Perform dynamic verification .
The permissions model

Users and user groups
User basic information management , Department , A user can join multiple user groups , A user can exercise the system authority of the user by setting an agent ;
The user group contains multiple users , User groups can inherit , The child user group inherits the permissions of the parent user group .
role
The use of roles is passive ,Module Roles can be associated during configuration ,UI Action You can associate roles ,ACL Configuration can be associated with roles , The role has inheritance relationship , The child role inherits the permissions of the parent role .
Applications and resources
ServiceNow Internal differentiation of different applications , Different applications have different resources 、 role 、 permissions , application (Application) Is abstracted as a set of installable component resources , Resources include Table( Data sheet )、Dictionary( Data columns )、API Interface (REST_Endpoint)、Menu( menu )、Module( Page components )、UI Page( Independent page )、UI Action( Page button ) etc. , Where is the menu 、 Page components 、 Page buttons use RBAC Access mode ; Data sheet 、 Data columns 、API Interface 、 Independent pages use ACL authentication .
It's special ,Table stay ACL Authentication colleagues , Have configuration Application Access, each table Set the operation permission according to the application .
ACL Authenticated Object and Operation The types are as follows .


Components (Module) There are many ways to access , With ListRecord and URL Visit mainly , As shown in the figure below .ListRecord Represents a record that accesses a table ,URL The access mode means that you can access through URL-Get Accessing data in parameter mode .Module The authentication of is performed by configuring the associated Role To achieve .
Module Of LinkType( access ) Yes 13 Kind of ,ListRecord The way can be through Filter Specify the default filter query criteria , But it is not used as data row range permission , After entering the specific page , Filter conditions can be cleared .


RBAC authentication
Resources requiring authentication are associated with required roles during configuration , The use of roles is passive ,Module Roles can be associated during configuration ,UI Action You can associate roles ,ACL Configuration can be associated with roles .
The user or user group selects the associated role during configuration .
ACL authentication
ACL Authentication designation Object Of Operation Authentication is needed , Authentication is performed in three ways
Role
Condition
Script
Table Addition, deletion and modification of 、 Fields can be added, deleted, modified, and queried through ACL To configure the
ServiceNow Yes Table、Column Of ACL Control is mostly ReadOnly

Design can be used for reference
The management granularity of resources is fine , Therefore, the control granularity of permissions 、 Flexibility ;
Different authentication models are used for different authentication scenarios ;
UI Data links for layer resources and permissions 、 Of each message Link The jump design is meticulous ;
shortcoming
The association of users and user groups lacks flexibility , For example, circle a group of users as a group according to user attributes ;
The permission configuration is scattered , The use permissions are scattered at various resource management portals ;
ACL Of Condition The configuration function is simple , Configure high threshold ;
Authentication in open and integrated scenarios is not considered ;
No data range authentication .
problem
The essence of permission management is to user Access system resources do jurisdiction control , You need to define the user 、 resources 、 jurisdiction ;
Large user volume 、 When the post turnover rate is high , Be efficient 、 Convenient Circle users 、 to grant authorization ;
Data authentication , Including data row authentication 、 Column authentication , Efficient authorization of data authority 、 authentication ;
Good business scalability ;
The front and back modules of permission management and permission use are not consistent , The business definition is inconsistent with the engineering definition , For example, the front end is an integrated service , The background is divided into multiple microservices , In authority management 、 Functional Authentication 、 How to divide and control data authentication ;
Special functions required by permissions : Roles are mutually exclusive , Identity proxy , Permission pre dependency , Authority approval process , Set the validity period for role authorization , Permission policy priority .
The goal is
Technical objectives
The work efficiency : How quickly can users get the permissions they should have ;
Authentication efficiency : High performance authentication does not affect normal business logic processing ;
Security : Ensure that the function will not be caused by misjudgment of permission system 、 Data leaks ;
Extensibility : Provide scalability at multiple nodes of the system , Including but not limited to user type extensions 、 User attribute extension 、 Resource type extension 、 Resource attribute extension .
Functional objectives
Basic function
Development of basic functions of authority , Solve the above problems 1-5.
Field edit permission
When the current user has no permission to edit the field , The front-end display control is disabled .
Identity proxy
Users ask for leave or job transfer , There will be people who temporarily or permanently transfer the system authority to the handover . This function is designed to support , Later, it is implemented through version iteration ,MVP Version does not implement .
design scheme
The design of this scheme adopts RBAC+ABAC The integration method realizes permission management , namely NGAC. compatible RBAC、ABAC The advantages of , At the same time, extension points are reserved in the implementation scheme , The whole scheme can be implemented through “ Big design 、 Small implementation ” The way of iterative opening , Keep the overall architecture unchanged , It can be realized first MVP edition , Then iteratively implement the functions in the design scheme step by step .
Technical terms
User: user , It can be a natural person user in the tenant 、 It can be a third-party system 、 It can be a subsystem within the application , All kinds of users have basic attributes , Properties can be customized according to the tenant dimension ;
UserGroup: A group of users specified in the management platform , It is used to grant access rights to these users ;
Role: role , Roles are used to configure permission policies , A role is associated with a user type , The role policy configures the function permissions that the role has 、 Data column permissions 、 Data row range permission ;
Resource: Permission resource item , for example flow( technological process ),Resource Hierarchical relationship , Corresponding multiple Action, Non leaf nodes only have Read, Leaf nodes have 1-N individual Action;
Action: action , such as : management 、 Check the details 、 modify
Condition: Conditions , Can carry Subject、Object Attached properties , It can also host the attributes passed in by the business system ( You can talk to Subject、Object irrelevant ), adopt Expression Language To realize dynamic operation based on context
Expression Language: Expression language , According to context parameters 、 Built in method dynamic calculation results
ALC(Access Contrl) : Access control , This article refers to the project resource access policy
The permissions model


Application partition
Business applications are divided from the perspective of users , The granularity of application can be discussed
for example , Definition ITSM Inside ITAM As a business application , Or the definition ITAM The account in (Account) As a business application ;
Business applications can be divided into 1-N Engineering applications , Engineering applications may include front-end engineering 、 Back end microservice engineering .
Purpose : Permission items are bound to business applications , It is convenient for users to set the role of a business from the user's perspective 、 jurisdiction ;
An engineering application belongs to a business application , for example ITAM There are ITAM-A,ITAM-B And other engineering applications , Each engineering application manages its own permissions ( menu 、 Button 、HTTP Interface 、RPC Interfaces, etc. )
Purpose : Engineering application and business application binding , Engineering resources are bound with engineering applications , Permission items are bound to project resources , It is convenient for developers to set access policies on demand .
Users and user groups
Users are defined as system resource accessors , A broad range of user definitions , Not only the natural persons within the tenant , It also includes in application subsystems 、 Third party systems, etc , Different types of users have different basic attributes , User attributes are extensible ;
Efficiently delineate users
A user belongs to multiple user groups , A user group contains multiple users , The association relationship between users and user groups can be statically specified 、 It can be done by Condition Composed of Expression Language Expression to dynamically match , Dynamic matching needs to monitor the user attribute changes of master data , Implementation is more complex , Iteratively implement
User groups do not implement relationship inheritance , In specific use , User group inheritance increases the complexity of authority traceability , It is not very useful for efficient user delineation .
resources
Resource management under engineering application , Different user types can access different project resources ,
for example , The resources accessed by natural persons are menus 、 Interface 、 The button has the gateway interface corresponding to the button ;
The resources accessed by the system are API Interface (HTTP、RPC).
Permission item
The permission item is the permission information that the administrator sees when authorizing a role , Including function permission items and Data permission items ; Permission items are the definitions of engineering resources and master data in the permission business field , And define the corresponding configuration of permission business .
For example, master data assets (Asset) There are properties model (Model), Configure corresponding permission items
- name: Physical assets
key: Asset
attributes:
- name: Asset model
key: "model"
deny_show: "-888888"
value_type: "int"Resource access control (ACL)
If authentication is required for engineering resources , Bind with the corresponding permission item
For example, application business ITAM Front end engineering athena.node Of HTTP Interface GetAssetList Authentication is needed , Required permission items ITAM The permission Item Configuration under application is asset:view_list,ACL The configuration is as follows :
Interface resource table format :{ Business applications }:{ Engineering applications }:{ Interface }
Function permission item format :{ Business applications }:{resource}:{action}
CheckPermission: true
InterfaceName: itam:node:GetAssetList
RuleList:
- Rule:
- AuthKey: itam:asset:view_listRole and permission settings
When adding a role , Bind a user type , The type could be Global,Global Roles do not distinguish between user types ;
Role permission settings : Set function permission items of roles , Data permission items
Data field permission items can be set to allow 、 Disable both policies ( Reference resources PeopleSaas authentication )
The data row range permission matches the user type attribute and the master data field attribute to delineate the range ,
for example , role A User type Association for :Employee, The scope of access to assets is to only access idle assets in the region , expression :
employee.location==asset.location&&asset.status=='idle'
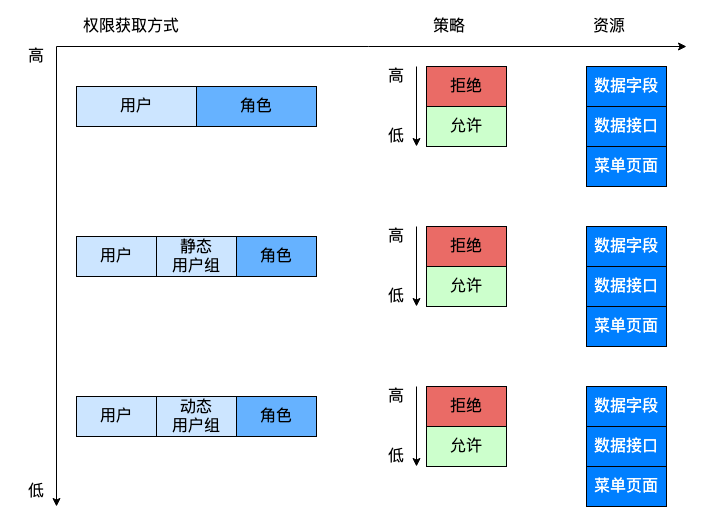
to grant authorization
A single user can be directly associated with a user group , User group associated roles , So as to obtain permission ;
A single user can be matched to a dynamic user group by criteria , User group associated roles , So as to obtain permission ;
A single user can set roles directly , So as to obtain the permission of role settings .
Privilege priority
The permissions obtained by users from different ways may conflict and overlap , Define priorities as follows
Scene flow
scene 1: Third party user asset repurchase - Confirm the payer
IT The department introduces a third-party company A The employees' , His job duties are to ITAM The backstage is responsible for confirming the payment entity of asset repurchase in the region , You can only see the repurchase process sheet in the region in the status of the confirmed entity , Only asset number and application time can be seen in each line of record .

scene 2: Engineering applications itam-flow Get master data Employee Part of the permissions for
itam-flow Only master data Employee Of UserName、Logo、Department、Sequence Query authority
itam-flow Register as a privileged user as an internal system ;
Set up a character , This role can query itam-data Service Employee Query interface , The data column has only UserName、Logo、Department、Sequence;
itam-data Of Employee Query interface , distinguish itam-flow System , Query by policy itam-flow Data permission of , Return data according to permission configuration .
Physical architecture

Join us
We are byte beating Lark-LBA-People C&B The team , In charge of flying books compensation 、 option 、 vacation 、 social security 、 Bonus And other business system platforms . This year we are starting from 0 To 1 Set up basic salary and vacation SaaS System , And will start using for bytes and external tenants , Extremely short of talents .
stay HCM field , Flying book is still very early . In terms of technical system and team building , We are also very early . therefore C&B The team has a lot of opportunities , Can let everybody undertake the technology 、 Business 、 Bigger challenges on the team , Also get more rapid growth .
We will find that 2B SaaS Microsoft, the leader of 、Oracle、SAP Both have decades of history , Even domestic UFIDA 、 Kingdee ( Although it is not first-class ) Is the same .
2B SaaS It's a big track , It is also a career that can be invested for decades , Both technology and domain knowledge can make us competitive in our forties and fifties , What are you waiting for , Get in the car quickly ~ Below scan QR code Or click on “ Read the original ” Find the position & The CV !

边栏推荐
- Dry and wet contacts
- 第三代电力电子半导体:SiC MOSFET学习笔记(五)驱动电源调研
- Related operations of ansible and Playbook
- Svg+js keyboard control path
- JDBC - database connection
- Assessment of public finance of Jilin University in March of the 22nd spring -00091
- Tape SVG animation JS effect
- DO280OpenShift访问控制--加密和ConfigMap
- Analysis report on operation trend and investment strategy of global and Chinese tetrahydrofurfuryl propionate industry from 2022 to 2028
- Scala IO writes data to a text file
猜你喜欢

im即时通讯开发应用保活之进程防杀

Is there really something wrong with my behavior?

Svg+js keyboard control path

Svg line animation background JS effect

Outer screen and widescreen wasted? Harmonyos folding screen design specification teaches you to use it

MySQL problem points

Eye gaze estimation using webcam

微搭低代码中实现增删改查

canvas线条的动态效果

人体改造 VS 数字化身
随机推荐
DO280OpenShift访问控制--加密和ConfigMap
How to delete the entire row with duplicate items in a column of WPS table
Is there really something wrong with my behavior?
Canvas spiral style animation JS special effect
[interview question] what is a transaction? What are dirty reads, unrepeatable reads, phantom reads, and how to deal with several transaction isolation levels of MySQL
Hibernate学习3 - 自定义SQL
Common redis commands in Linux system
MySQL log management
离散数学及其应用 2018-2019学年春夏学期期末考试 习题详解
Scala IO serialization and deserialization
Power application of 5g DTU wireless communication module
One way 和two way ANOVA分析的区别是啥,以及如何使用SPSS或者prism进行统计分析
svg+js键盘控制路径
Analysis report on operation mode and future development of global and Chinese methyl cyclopentanoate industry from 2022 to 2028
Phprunner 10.7.0 PHP code generator
部门新来的00后真是卷王,工作没两年,跳槽到我们公司起薪18K都快接近我了
技术分享| WVP+ZLMediaKit实现摄像头GB28181推流播放
Scala IO reads binary files
Analysis report on operation pattern and supply and demand situation of global and Chinese cyano ketoprofen industry from 2022 to 2028
∞ symbol line animation canvasjs special effect